Your organization's sensitive data floating through the air, invisible radio waves carrying everything from customer records to financial information. Without proper Wi-Fi security, you're essentially broadcasting your most valuable assets to anyone within range. In today's hyperconnected world, wireless security isn't just an IT concern, it's a business imperative that can make or break your organization's reputation and bottom line.
Wi-Fi security fundamentals: Building your defense foundation
The wireless revolution transformed how we work, but it also opened Pandora's box of security vulnerabilities. Understanding where we've been helps us appreciate where we need to go, and the evolution of Wi-Fi security tells a story of constant adaptation to increasingly sophisticated threats.
A brief journey through wireless security history
Wireless security has evolved dramatically since the late 1990s. The original security protocol, WEP (Wired Equivalent Privacy), was introduced in 1999 but quickly proved catastrophically flawed; it could be cracked in minutes using readily available tools. This led to WPA (Wi-Fi Protected Access) in 2003, followed by the more robust WPA2 in 2004, which remained the gold standard for over a decade. Today, WPA3 represents the cutting edge of wireless security, addressing vulnerabilities that persisted even in WPA2.
Understanding 802.11 shared key authentication
The 802.11 standard originally included Shared Key Authentication, which ironically was less secure than its alternative, Open System Authentication. In Shared Key Authentication, both the client and access point possessed a secret key (WEP key). The authentication process involved a four-way handshake where the AP would send a challenge text, the client would encrypt it using the shared key, and send it back for verification.
The critical flaw? This process actually exposed the keystream to eavesdroppers, making the network more vulnerable than using no authentication at all. This is why Shared Key Authentication was deprecated and why modern networks rely on far more sophisticated methods.
The enterprise security model
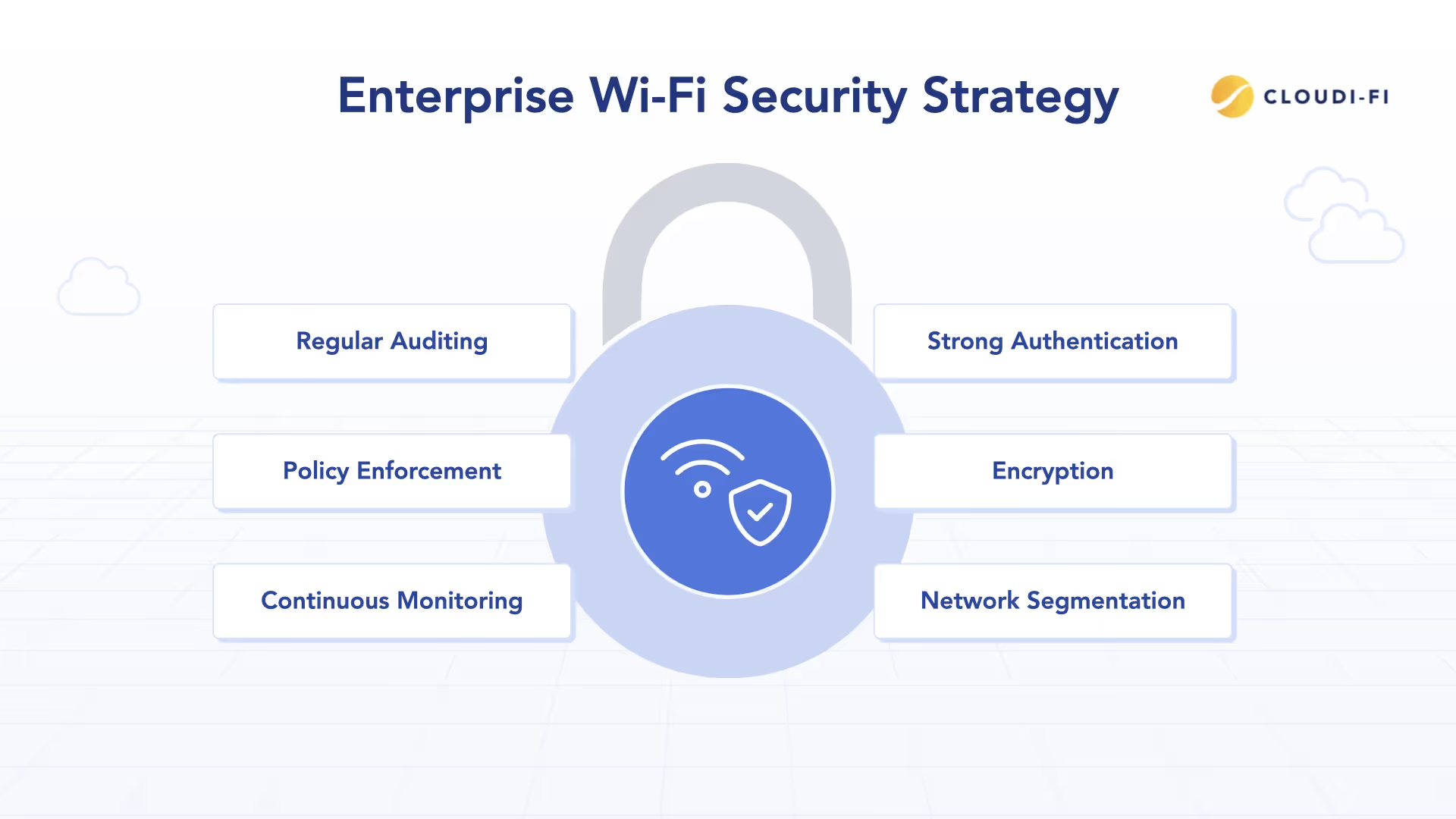
For large enterprises, successful Wi-Fi security isn't about a single technology, it's about implementing a layered defense strategy. A robust enterprise security model should include:
1. Strong Authentication: Implement 802.1X with EAP methods that use certificates or secure credentials
2. Encryption: Deploy WPA2-Enterprise or WPA3-Enterprise for data protection
3. Network Segmentation: Separate guest, employee, and IoT traffic into distinct VLANs
4. Continuous Monitoring: Deploy wireless intrusion detection/prevention systems (WIDS/WIPS)
5. Policy Enforcement: Implement role-based access controls and network access control (NAC)
6. Regular Auditing: Conduct periodic security assessments and penetration testing
This multi-faceted approach ensures that even if one layer is compromised, others remain intact to protect your network.
Wi-Fi security challenges: Know your enemy
Every wireless network faces an invisible battlefield where attackers probe for weaknesses 24/7. The challenge isn't just technical, it's also operational, financial, and constantly evolving as attack methods become more sophisticated.
Passive and active WLAN discovery
Attackers begin their assault through reconnaissance. Passive discovery involves simply listening to wireless traffic using tools like Wireshark, completely undetectable to network administrators. Active discovery takes it further, with attackers sending probe requests to identify hidden networks and gather information about security configurations.
The scary part? Both methods require minimal technical expertise and can be performed from a laptop in a parking lot.
Open System Authentication and EAP vulnerabilities
Open System Authentication sounds innocent but creates significant risks. While it doesn't authenticate users, it allows anyone to associate with the network. Combined with weak or no encryption, this becomes an open invitation for attackers.
Even when implementing EAP (Extensible Authentication Protocol), challenges emerge. Poorly configured EAP methods, weak passwords, or failure to validate server certificates can leave networks vulnerable despite using enterprise-grade protocols.
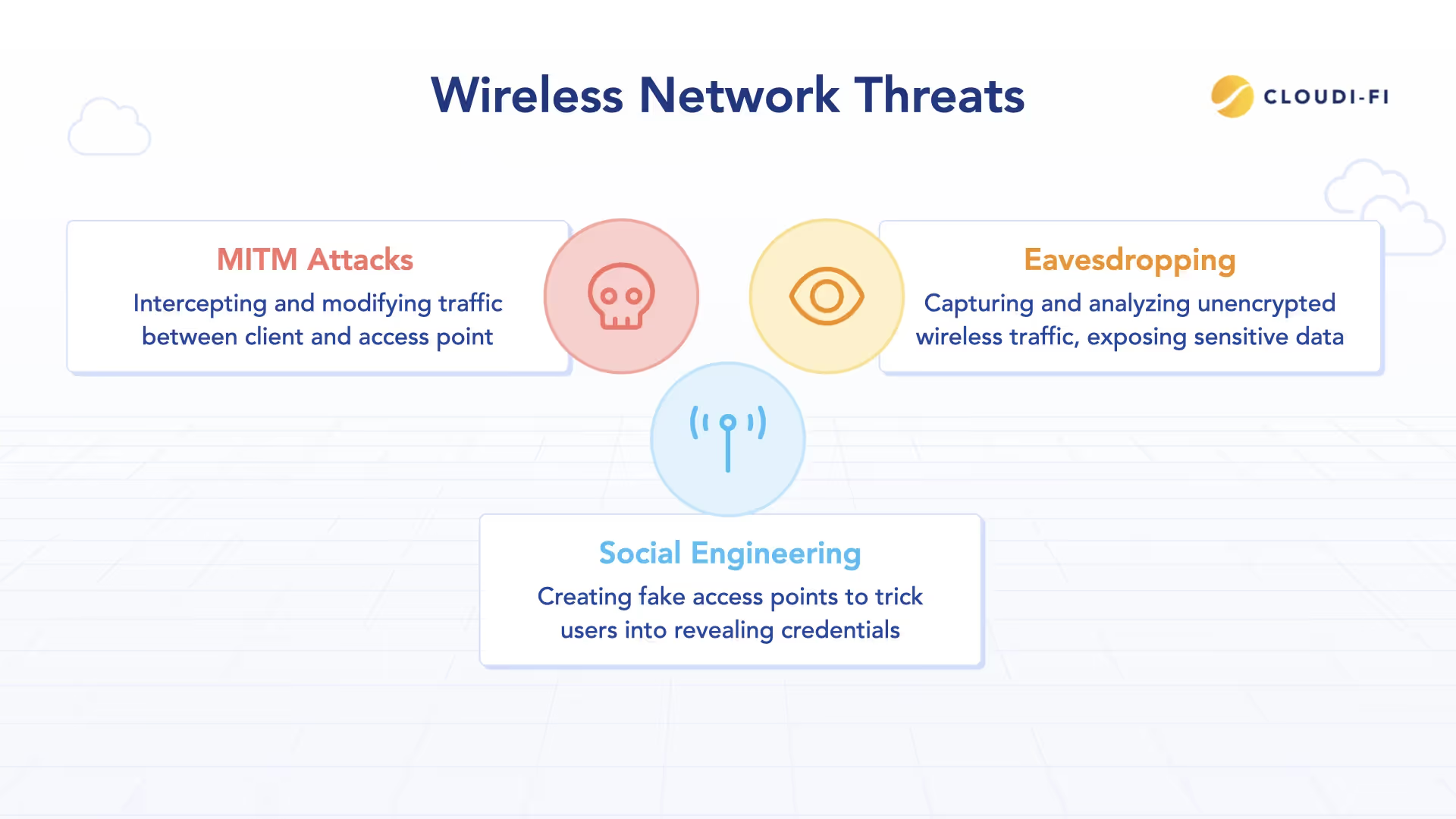
The threat landscape
Eavesdropping: Unencrypted or weakly encrypted wireless traffic can be captured and analyzed. Everything from emails to login credentials becomes accessible to anyone with packet capture tools.
Social Engineering: Attackers create fake access points with names similar to legitimate networks (evil twin attacks) or set up rogue APs that appear to offer free connectivity, tricking users into connecting and revealing credentials.
Man-in-the-Middle (MITM) Attacks: By positioning themselves between the client and legitimate AP, attackers intercept and potentially modify all traffic, stealing credentials, injecting malware, or manipulating data.
The cost factor
Beyond technical challenges, IT teams face significant operational and financial burdens:
- Personnel costs: Training staff on complex security protocols and continuous monitoring
- Infrastructure investment: Enterprise-grade access points, authentication servers (RADIUS), certificate authorities
- Maintenance overhead: Regular security updates, certificate lifecycle management, troubleshooting authentication issues
- Incident response: Time and resources spent investigating breaches or security events
These costs must be balanced against the potentially catastrophic expenses of a data breach—which can include regulatory fines, litigation, reputation damage, and customer loss.
Learn the key guest Wi-Fi security best practices.
Authentication methods: The keys to your kingdom
Authentication is the gatekeeper of your wireless network; get it wrong, and everything else falls apart. Modern Wi-Fi authentication has evolved beyond simple passwords to include sophisticated cryptographic methods that verify both users and infrastructure.
Wi-Fi authentication methods generally fall into three categories:
1. Pre-Shared Key (PSK) / Simultaneous Authentication of Equals (SAE): Simple password-based authentication (WPA2/WPA3-Personal)
2. Enterprise Authentication: 802.1X with EAP methods requiring authentication servers
3. Enhanced Open/OWE: Opportunistic encryption for public networks
For enterprise environments, the choice of credential type significantly impacts both security and usability:
- Digital Certificates
Digital certificates represent the gold standard in wireless authentication. These cryptographic credentials, issued by a Certificate Authority (CA), provide mutual authentication; both the client and server prove their identities cryptographically.
Certificates contain 1. public key infrastructure (PKI) for encryption, 2. identity information (subject name, organization), 3. digital signature from the issuing CA, and 4. validity period. The beauty of certificates is that they eliminate password transmission entirely, making credential theft through eavesdropping impossible. However, they require robust PKI infrastructure and proper certificate lifecycle management.
- PAC Files (Protected Access Credentials)
PAC files were introduced with EAP-FAST to improve upon legacy authentication methods. A PAC is essentially a shared secret established between the client and authentication server, used to create a secure tunnel for subsequent authentication. PACs can be provisioned:
- Automatically: Dynamically generated during first connection (less secure)
- Manually: Pre-distributed by administrators (more secure but operationally intensive)
While PACs simplified deployment compared to certificates, they're less commonly used today as certificate management has improved.
- Username and Password
Traditional username/password authentication remains popular due to its simplicity and user familiarity. Combined with secure EAP methods like PEAP, passwords can provide reasonable security.
However, passwords introduce vulnerabilities:
- Susceptible to brute force attacks if weak
- Can be compromised through social engineering
- Require secure transmission mechanisms
- Often reused across services, increasing breach impact
Best practices include enforcing strong password policies, implementing multi-factor authentication where possible, and using secure inner authentication methods.
The 802.1X/EAP framework: enterprise-grade protection
When you need to authenticate thousands of users across hundreds of access points, nothing beats the scalability and security of 802.1X. This IEEE standard provides network access control by requiring authentication before granting network access; think of it as a sophisticated bouncer for your wireless network.
The 802.1X framework involves three key players:
- Supplicant: The client device requesting access
- Authenticator: The access point controlling network access
- Authentication Server: Typically a RADIUS server validating credentials
The process begins when a client attempts to connect. The AP places them in an unauthenticated state, allowing only authentication traffic. The client and RADIUS server then perform mutual authentication through the AP. Only after successful authentication does the AP grant full network access.
Want to dive deeper into how 802.1X authentication works? Check out our detailed article on 802.1X authentication for a comprehensive breakdown.
EAP method comparison
Different EAP (Extensible Authentication Protocol) methods offer varying security levels and deployment complexity:
PEAP (Protected EAP): PEAP creates an encrypted TLS tunnel before authenticating the user, protecting credentials from eavesdropping. It's widely supported and commonly paired with MSCHAPv2 for inner authentication. The main requirement is deploying a trusted server certificate; clients don't need individual certificates, making it popular for password-based authentication.
EAP-FAST (EAP Flexible Authentication via Secure Tunneling): Developed by Cisco as an improvement over LEAP, EAP-FAST uses PAC files to establish a secure tunnel quickly without requiring certificates. While less common today, it's useful in environments where certificate deployment is challenging. However, automatic PAC provisioning can be vulnerable to MITM attacks.
MSCHAPv2 (Microsoft Challenge Handshake Authentication Protocol version 2): MSCHAPv2 is an inner authentication method typically used within PEAP or EAP-FAST tunnels. It provides mutual authentication using passwords but should never be used alone—it requires the outer tunnel's protection. While convenient, it's considered less secure than certificate-based methods.
EAP-TLS (EAP Transport Layer Security): EAP-TLS represents the most secure EAP method, requiring certificates on both client and server. Mutual authentication happens cryptographically without transmitting any passwords. The challenge? You need functional PKI infrastructure and must deploy certificates to all devices. Despite the operational complexity, it's the gold standard for high-security environments.
Security design scenarios: Real-world implementation
Designing wireless security isn't one-size-fits-all; different scenarios demand different approaches. Nowhere is this more apparent than in public network access, where traditional security models simply don't work.
Public network access and captive portals
Public Wi-Fi presents a unique challenge: you want to provide access without requiring pre-distributed credentials. Historically, this meant open networks with no encryption : a security nightmare.
Captive portals emerged as a solution, intercepting web traffic to present authentication pages before granting internet access. However, early implementations had significant flaws:
- Traffic before authentication was unencrypted
- Authentication often happened over HTTP (not HTTPS)
- No device or user verification beyond the initial login
- Easy to bypass or spoof
Modern approaches: zero trust principles
Today's security design incorporates Zero Trust principles, fundamentally changing how we approach public access:
1. Never Trust, Always Verify: Every connection attempt is authenticated and authorized, regardless of location
2. Least Privilege Access: Users receive only the minimum access necessary for their purpose
3. Assume Breach: Design with the assumption that attackers are already present
4. Continuous Verification: Authentication isn't one-time—it's continuous throughout the session
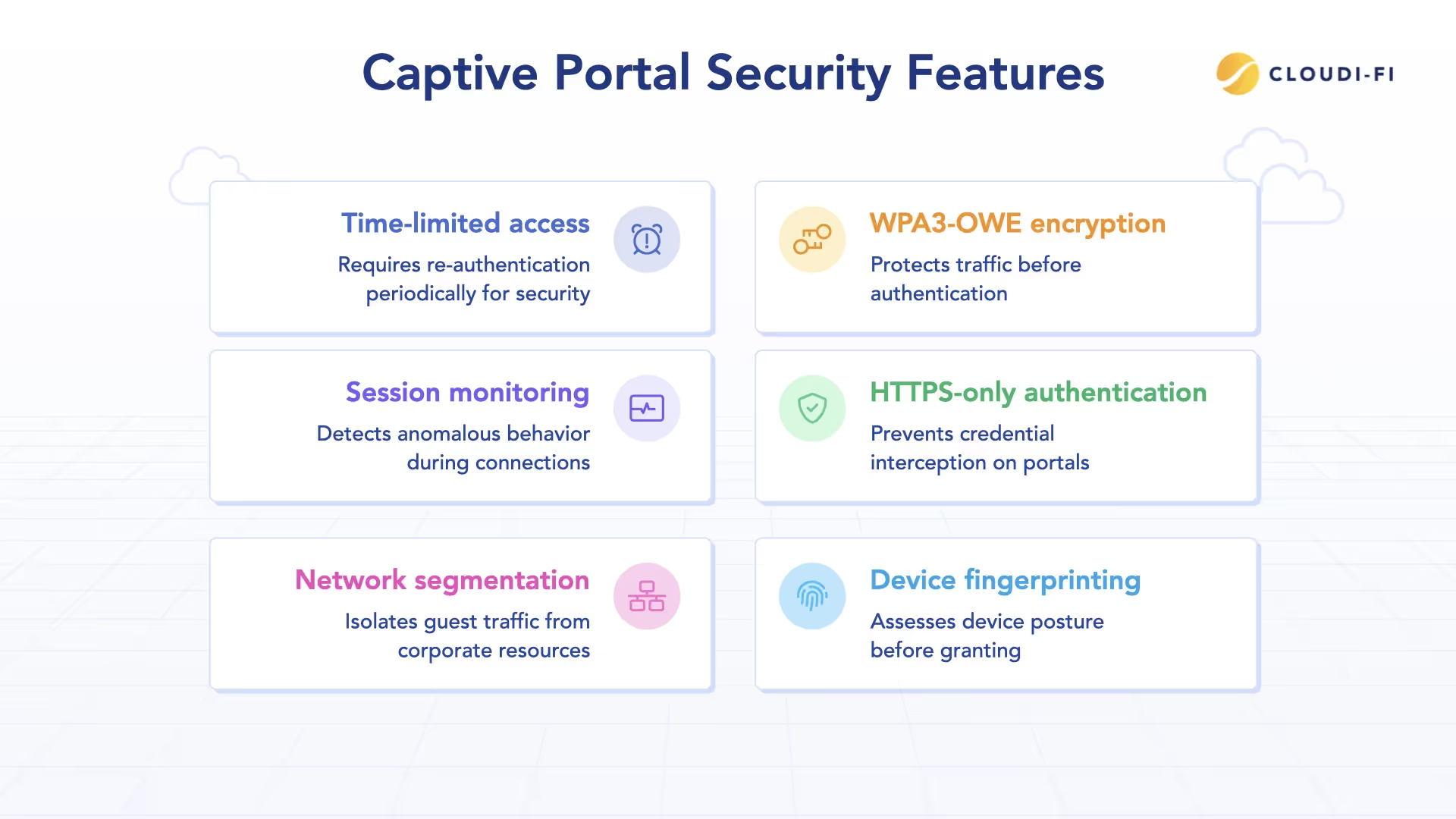
Modern captive portal solutions combined with Zero Trust include:
- WPA3-OWE encryption protecting traffic even before authentication
- HTTPS-only authentication portals preventing credential interception
- Device fingerprinting and posture assessment before granting access
- Network segmentation isolating guest traffic from corporate resources
- Session monitoring detecting anomalous behavior during connections
- Time-limited access requiring re-authentication periodically
This layered approach means that even if one component is compromised, the network remains protected. Public access networks are no longer the vulnerable soft targets they once were.
WPA3 and OWE: The next generation of wireless security
After 14 years of WPA2 dominance, the wireless industry finally addressed long-standing vulnerabilities with WPA3. Alongside it came OWE (Opportunistic Wireless Encryption), revolutionizing how we secure open networks.
WPA3: Stronger, smarter, safer
WPA3 introduces several critical security enhancements:
Simultaneous Authentication of Equals (SAE): Replacing WPA2's PSK four-way handshake, SAE provides forward secrecy and protection against offline dictionary attacks. Even if someone captures your wireless traffic, they can't crack your password offline.
192-bit Security Suite: WPA3-Enterprise offers optional 192-bit cryptographic strength, meeting the needs of highly sensitive environments like government and finance.
Protected Management Frames: Unlike WPA2 where this was optional, WPA3 mandates protection for management frames, preventing deauthentication and disassociation attacks.
Simplified Security: WPA3-Easy Connect uses QR codes for device onboarding, making secure configuration accessible even for non-technical users.
Prerequisites for WPA3 implementation
Deploying WPA3 requires:
- Compatible hardware: Both access points and client devices must support WPA3 (most devices from 2019+ do)
- Firmware updates: Existing equipment may need updates to enable WPA3 support
- Transition mode planning: Supporting both WPA2 and WPA3 clients during migration
- Testing protocols: Ensuring compatibility across your diverse device ecosystem
OWE: Securing open networks
Opportunistic Wireless Encryption (OWE) solves a long-standing problem: how to encrypt public open networks without shared passwords.
OWE (also known as Enhanced Open) provides:
- Individualized data encryption: Each client gets unique encryption keys
- Protection against eavesdropping: Traffic can't be intercepted by other clients
- No authentication required: Maintains the convenience of open networks
- Backward compatibility: Can coexist with legacy open networks
The magic of OWE lies in its Diffie-Hellman key exchange during association, creating encrypted tunnels without pre-shared credentials. For coffee shops, airports, or hotels, OWE transforms inherently insecure open Wi-Fi into reasonably protected connectivity.
OWE Implementation requirements
Rolling out OWE requires:
- OWE-capable access points: Many enterprise APs gained support through firmware updates
- Client support: Operating systems from iOS 13+, Android 10+, Windows 10 (2004+) support OWE
- Proper SSID configuration: OWE networks use separate SSIDs or dual-mode configurations
- Clear user communication: Users won't notice differences, but IT should understand the protection level
Conclusion: Your wireless security journey starts now
Wireless security isn't a destination, it's an ongoing journey of learning, adaptation, and vigilance. From understanding historical vulnerabilities to implementing cutting-edge WPA3 and Zero Trust architectures, every layer of defense matters.
The key takeaways:
- Layer your defenses: No single technology protects everything
- Authenticate strongly: Certificates beat passwords, 802.1X beats PSK
- Encrypt everything: WPA3 and OWE eliminate excuses for unencrypted traffic
- Monitor continuously: Threats evolve faster than any static defense
- Never stop learning: Whether through CWNP certification or staying current with emerging threats
Your wireless network transmits your organization's most valuable assets through open air. Protecting it isn't optional, it's essential. The tools and knowledge exist to build robust wireless security. The question is: will you implement them before attackers find your weaknesses?








