Introduction
Corporate Wi-Fi has long been treated as a trust boundary: connect, and access follows. Modern enterprise networks challenge that assumption. Cloud applications, remote work, and bring-your-own-device (BYOD) usage reduce the relevance of network location as a trust factor.
The Open SSID plus Zero Trust Network Access (ZTNA) model separates connectivity from authorization. Wi-Fi provides encrypted transport, while Cloudi-Fi and ZTNA control access based on identity, device posture, and context. This approach maintains security without complicating onboarding or guest access.
Why the old Wi-Fi model no longer works
Traditional Wi-Fi relied on network location and pre-shared keys or 802.1X credentials. These methods assume trust based on connectivity, creating security gaps in modern environments. Key challenges include:
- Cloud-first applications that bypass local network controls.
- Remote and mobile devices that connect from unpredictable locations.
- Operational complexity from multiple VLANs, DHCP scopes, and PSK or certificate management.
Zero Trust principles address these issues:
- No implicit trust: network access alone does not grant authorization.
- Per-session access control: each session is evaluated dynamically.
- Policy enforcement at the application layer: access is determined per application, device, and context rather than network segment.
The Open SSID approach positions Wi-Fi as a secure conduit, while Cloudi-Fi and ZTNA enforce policy consistently across all devices.

Open Wi-Fi with encryption
Open Wi-Fi does not imply unprotected traffic when using Opportunistic Wireless Encryption (OWE). OWE enables encrypted, password-free connections with the following properties:
- Diffie-Hellman key exchange establishes a unique session key between client and access point.
- Traffic is encrypted using AES-CCMP at the same level as WPA3-Personal.
- Protected Management Frames (PMF) prevent deauthentication and disassociation attacks.
- Client isolation blocks lateral movement between devices on the same SSID.
OWE transition mode allows coexistence with legacy devices while providing encryption for capable clients. This configuration mitigates passive sniffing without requiring pre-shared keys or 802.1X certificates.
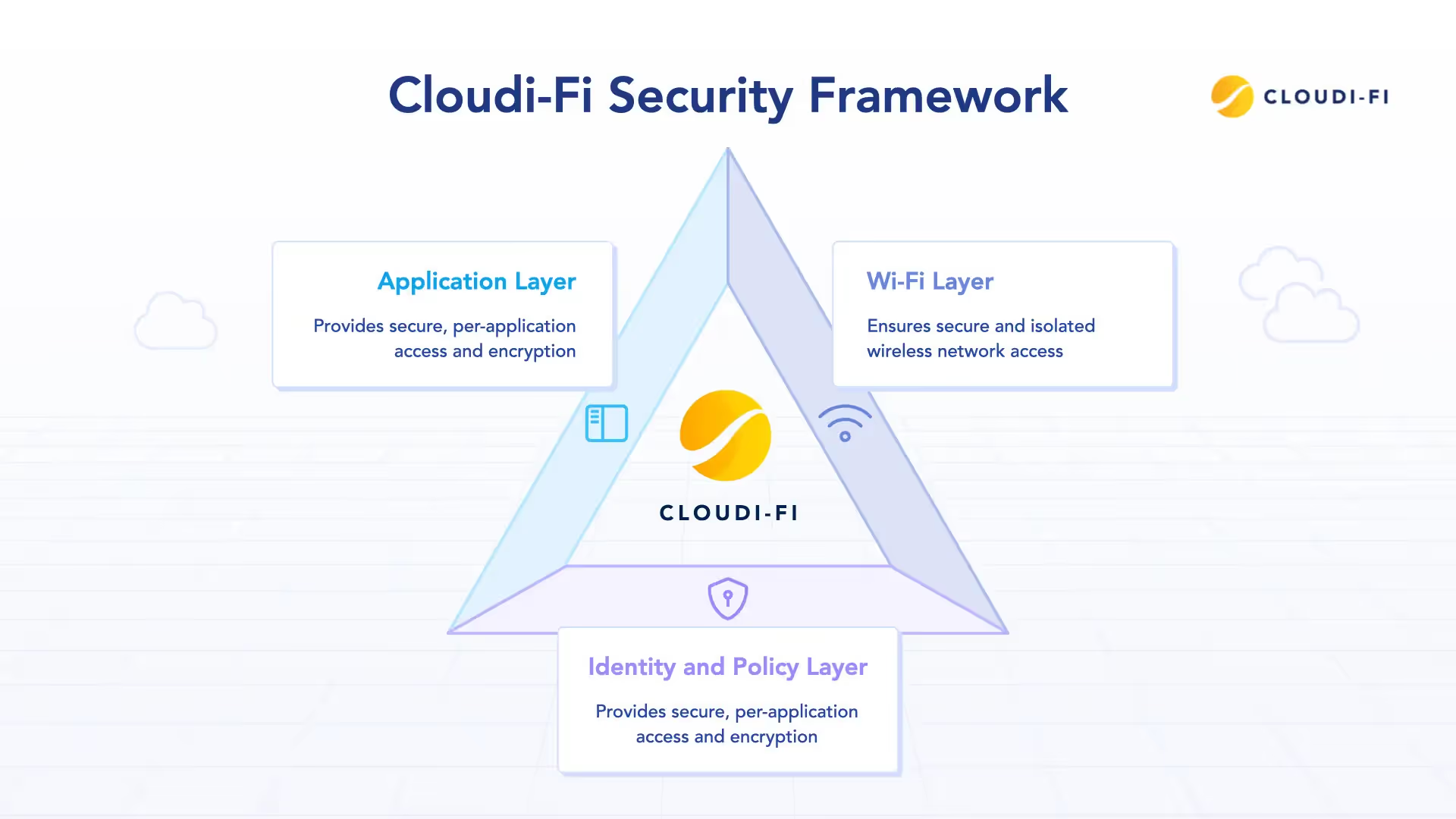
Cloudi-Fi reference architecture
Wi-Fi layer
- SSID: Open (OWE preferred) with PMF required.
- Client isolation: enforced at the access point or wireless LAN controller.
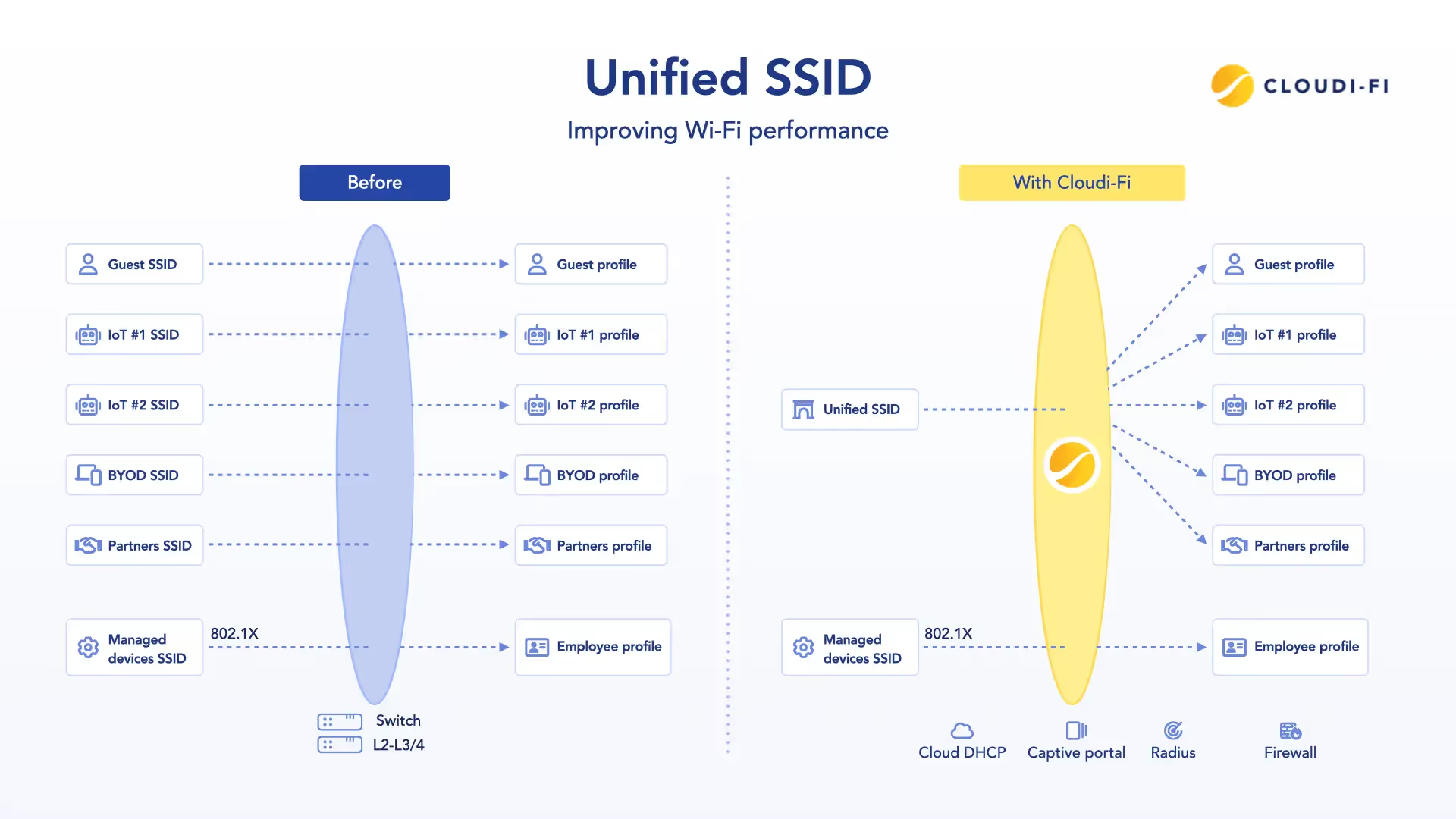
- Transport VLAN: a single Layer 2 segment with no default or internal routing paths. All traffic is directed to ZTNA gateways or secure internet egress, where Cloudi-Fi policies apply.
- DHCP fingerprinting: automatically identifies device type, operating system, and posture using DHCP options before authentication. This enables dynamic classification of BYOD, IoT, and managed devices.
Identity and policy layer
- Integration with identity providers using SAML for single sign-on and other authentication methods.
- RADIUS-based policy enforcement: Cloudi-Fi uses RADIUS attributes, including Vendor-Specific Attributes, Filter-IDs, and dynamic session parameters, to enforce granular access per device, user, and application.
- Policy decisions consider device type, user group, location, session context, and DHCP fingerprint results.
Application layer
- ZTNA provides per-application access rather than network-level access.
- TLS encrypts all application sessions end-to-end.
- Continuous evaluation ensures that changes in posture or context immediately affect access rights.
Security and operational benefits
The Open SSID plus ZTNA model reduces risk and simplifies operations:
- Encrypted traffic by default with OWE and TLS 1.3.
- Rogue AP and session hijacking mitigated by WIDS/WIPS and token binding within ZTNA tunnels.
- Lateral movement prevented through Layer 2 isolation and transport VLAN segmentation.
- DHCP fingerprinting enables automated device classification without VLAN sprawl.
- RADIUS-based policies provide centralized, per-device access control.
- Elimination of PSK or certificate rotation.
- Unified onboarding for employees, guests, and BYOD devices.
Compliance and governance
This architecture aligns with modern cybersecurity frameworks and regulatory expectations:
- Supports Zero Trust principles.
- Centralized access control provides a single, auditable source of truth.
- Consolidated logging simplifies audits and incident response.
- Continuous policy enforcement ensures ongoing compliance across all devices and sessions.
Key considerations
- Legacy devices or IoT endpoints may require separate service VLANs with outbound-only rules or identity-aware proxies.
- Where WPA3/OWE or PMF is not supported, fallback options should be temporary, and access controls enforced at the application layer.
Conclusion
The Open SSID plus ZTNA model separates connectivity from access control. Wi-Fi provides encrypted transport, while Cloudi-Fi and ZTNA enforce identity- and device-based policies. DHCP fingerprinting and RADIUS-based policy enforcement ensure devices are automatically classified and access is granted based on verified attributes.
This approach reduces operational complexity, strengthens security, and ensures compliance with modern Zero Trust frameworks. Networks are treated as conduits, not trust boundaries, allowing organizations to secure applications without burdening users.








