Introduction: The shifting foundation of access control
IEEE 802.1X (Port-Based Network Access Control) has been the definitive standard for securing enterprise wired and wireless networks. It acts as a hard gatekeeper, ensuring only authenticated devices and users gain network access at the very first point of connection.
However, the operating environment has changed fundamentally. The rise of cloud adoption, the shift to Zero Trust architectures, massive IoT proliferation, and the permanence of the hybrid workforce have exposed the limitations of the traditional, on-premises 802.1X model. What was once robust in a centralized environment now struggles with scalability, security, and user experience.
Traditional 802.1X architecture: The technical backbone
The 802.1X mechanism is a precise, protocol-driven transaction designed to enforce a hard security boundary at Layer 2.
The standard and port states
The IEEE 802.1X standard defines the process. When a device connects to an Authenticator (switch or AP), the port defaults to the Unauthorized state, blocking all Layer 3 (IP) and data traffic. Only EAP over LAN (EAPoL) frames are permitted to pass. Upon successful authentication, the Authentication Server (RADIUS) signals the port to transition to the Authorized state, opening the connection for data flow. This mechanism enforces security at the physical and link layers.
Learn the fundamentals in our complete 802.1X guide.
Key roles and packet flow
The classic setup involves three roles:
- Supplicant: The client device requesting access.
- Authenticator: The network access device controlling the port.
- Authentication Server: The RADIUS server, which validates credentials against an identity store (e.g., Active Directory).
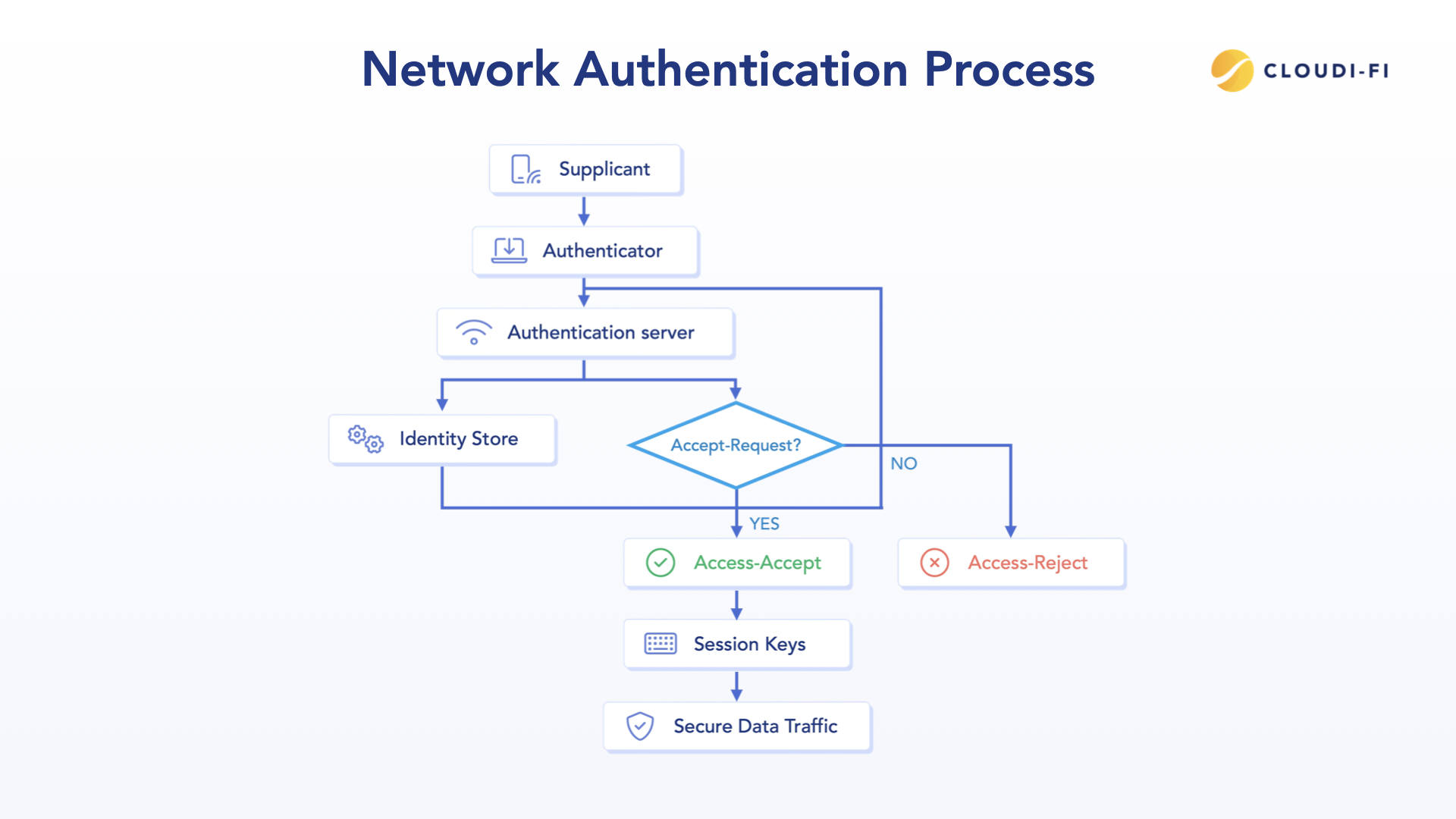
The core transaction is a multi-step EAP exchange, relayed via a RADIUS Access-Request and completed with an Access-Accept or Access-Reject. The Access-Accept includes the necessary session keys (like the PMK) to secure subsequent data traffic.
EAP methods: The ecosystem of choices
The Extensible Authentication Protocol (EAP) allows 802.1X to support various authentication types:
- EAP-TLS: The security gold standard, requiring mutual certificate-based authentication for both client and server, eliminating password risk.
- PEAP / EAP-TTLS: These wrap password-based authentication in a TLS tunnel. However, security hinges on clients correctly validating the server certificate—a common point of failure leading to man-in-the-middle attack vulnerabilities.
- EAP-FAST: A proprietary method (often Cisco) that uses Protected Access Credentials (PACs), reducing certificate overhead but introducing its own PAC lifecycle complexity.
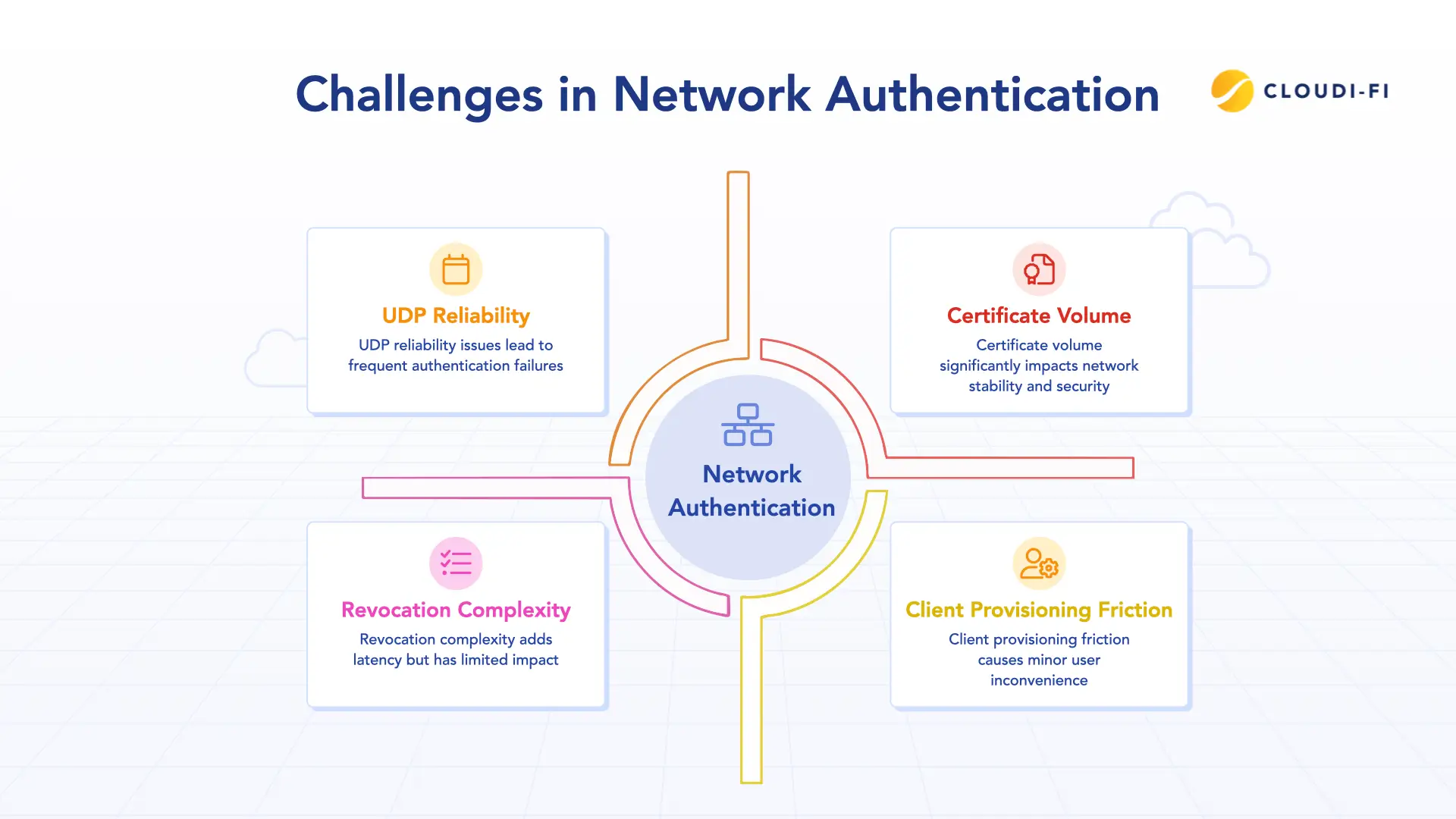
The bottlenecks of traditional 802.1X
The traditional, on-premises model faces compounding operational and technical strains as environments scale and modernize.
The PKI operational burden
Running EAP-TLS at scale is highly resource-intensive:
- Certificate volume: A large enterprise may manage tens of thousands of certificates (user, device, and server), where expired certificates are a leading cause of massive network outages.
- Revocation complexity: High-security policies require the Authenticator to validate a certificate's status via the Certificate Revocation List (CRL) or OCSP (Online Certificate Status Protocol) check, which introduces significant latency and a distributed failure point.
RADIUS scalability and reliability limits
Traditional RADIUS deployments (NPS, ISE) struggle with global scale:
- Appliance bloat: Scaling across sites requires proprietary replication, proxying, or clustering mechanisms, leading to high hardware costs and operational overhead.
- UDP reliability: The RADIUS protocol is based on UDP (User Datagram Protocol), which is connectionless and offers no guarantee of delivery. Over high-latency or lossy WAN links (common in hybrid work), UDP packet loss causes authentication timeouts and retries, directly degrading user experience.
Client provisioning friction
Configuring the Supplicant remains a major pain point. While MDM helps with corporate devices, onboarding BYOD requires manual setup (SSID, EAP method, server certificate trust), often driving high volumes of helpdesk tickets.
Onboarding and 802.1X
The complexity of 802.1X setup directly impacts the user onboarding experience, particularly when striving for the highest security posture with EAP-TLS. Achieving robust, certificate-based security necessitates a mechanism to distribute the supplicant's identity credentials (certificates) and correctly configure the network profiles (SSID, server validation trust chains) before the user attempts to connect. The operational friction of manual provisioning often creates a security incentive mismatch: IT teams frequently default to less secure password-based EAP methods (PEAP) or the weak MAB for guest and BYOD access simply to minimize helpdesk load and avoid complex certificate management, thereby undercutting the full security potential of 802.1X.
Key drivers: Zero Trust and IoT
Two fundamental shifts demand a re-architecture of the 802.1X ecosystem.
Zero Trust and continuous verification
802.1X is designed for point-in-time access control. Zero Trust requires continuous verification of device posture (e.g., is the OS patched, is the EDR agent running?).
The technical solution to this is the RADIUS Change of Authorization (CoA) message. If a threat intelligence platform detects a compromise after the device has been connected, the RADIUS server sends a CoA to the Authenticator, which immediately disconnects the client or reassigns it to a Quarantine VLAN. Implementing real-time CoA integration is complex with static, on-premises RADIUS servers.
IoT proliferation and MAB insecurity
IoT devices often lack the complexity to run a full 802.1X Supplicant, forcing enterprises to rely on the insecure MAC Authentication Bypass (MAB). Since MAC addresses are easily spoofed, this creates a massive attack vector.
Mitigation requires advanced device profiling engines that use passive methods like OUI lookups, DHCP fingerprinting, and SNMP queries to classify and identify the device type, enabling dynamic, restrictive policy enforcement.
Device and user detection
802.1X provides fundamental Device and User Detection by leveraging the Extensible Authentication Protocol (EAP) to authenticate entities using unique identifiers, which can be either user credentials or device certificates. The Authentication Server (RADIUS) is the policy engine that verifies these identities against the identity store. Crucially, upon successful verification, the RADIUS server doesn't just grant access; it returns specific RADIUS attributes (Vendor-Specific Attributes, or VSAs) in the Access-Accept message. These attributes, such as VLAN ID or Tunnel-Private-Group-ID, instruct the Authenticator (switch/AP) on how to segment the newly connected device. This mechanism ensures that network access is not just authenticated, but also dynamically authorized and controlled based on the unique identity of the connecting entity.
How cloud migration reshapes 802.1X
Cloud-native solutions address the technical and operational limitations of the traditional model, turning the 802.1X infrastructure into an identity-centric service.
Cloud-native RADIUS (RaaS)
RADIUS-as-a-Service (RaaS) fundamentally improves reliability and scalability:
- RadSec (RADIUS over TLS): Replaces insecure, unreliable UDP transport with encrypted, integrity-checked communication over TCP/TLS, ensuring delivery and security across the WAN.
- Global architecture: Geo-distributed Points of Presence (PoPs) handle authentication requests closer to the user, minimizing the latency issues associated with remote authentication.
- Elastic scaling: Eliminates the need for manual appliance clustering and proprietary replication.
Automated Cloud PKI
Cloud PKI platforms solve the certificate lifecycle problem:
- Protocol automation: They leverage protocols like SCEP (Simple Certificate Enrollment Protocol) and EST (Enrollment over Secure Transport) to integrate directly with MDM tools, enabling automated, zero-touch certificate issuance and renewal.
- Real-time revocation: Certificates can be instantly revoked across the network, vastly improving security posture.
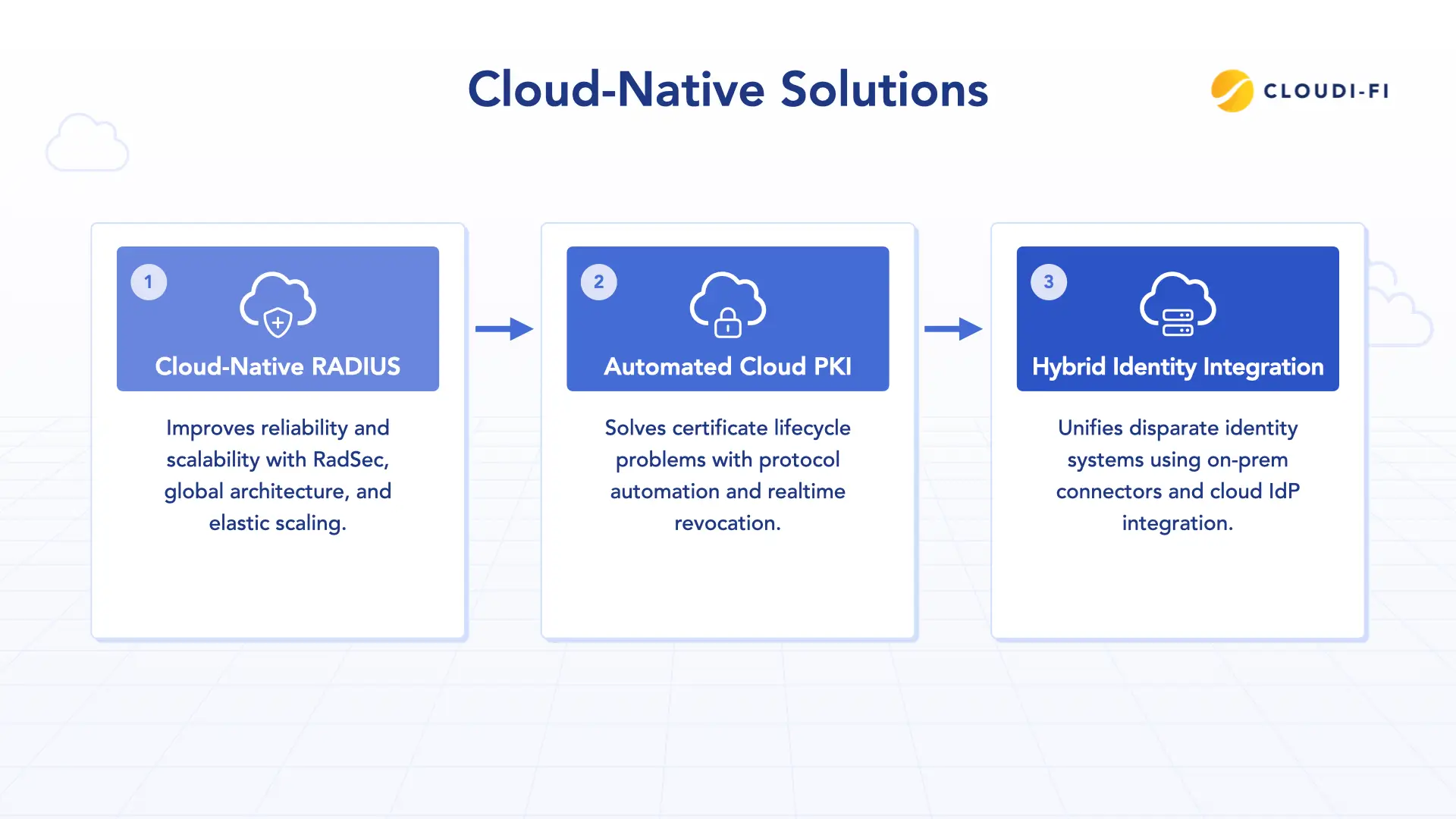
Hybrid identity integration
Modern RADIUS solutions serve as the control plane that unifies disparate identity systems:
- They use a lightweight on-prem connector to securely proxy authentication requests to legacy AD/LDAP.
- They integrate directly with cloud Identity Providers (IdPs) like Azure AD, Okta, and Ping via SAML/OIDC federation.
This creates a single, unified authentication fabric for both legacy and cloud identities.
Policy enforcement
The primary function of the RADIUS server, once identity is verified, is Policy enforcement. This involves applying granular, role-based access policies (RBAC) to control what specific network resources (servers, applications, internal zones) the authenticated user or device can access. By returning specific authorization attributes in the Access-Accept message, the 802.1X process moves beyond simple connection access to determine the logical segmentation and permissions of the endpoint, thereby strengthening security and operational efficiency simultaneously.
Dynamic VLAN assignment
A core component of policy enforcement is Dynamic VLAN assignment. The RADIUS server assesses the authenticated user or device identity and posture against predefined policies, and then directs the Authenticator (switch or AP) to place the endpoint into the appropriate Virtual Local Area Network (VLAN). For instance, a finance team laptop might be placed in a high-security VLAN, while a guest device is shunted to a restricted internet-only VLAN. This improves network segmentation, minimizes the attack surface, and simplifies resource management without requiring manual port configuration.
Conclusion: The path forward is identity-centric
802.1X remains a non-negotiable cornerstone of enterprise access control. However, the protocol is no longer managed by dedicated, static appliances. The future is an identity-centric, cloud-aware 802.1X ecosystem that provides:
- Global, low-latency RADIUS delivery (RaaS).
- Automated, secure certificate lifecycle management (Cloud PKI).
- Continuous security enforcement (CoA and ZTNA overlay).
- Dynamic segmentation for IoT and BYOD devices.
The challenge is not the protocol itself, but the management paradigm. The shift from on-premises hardware management to cloud-delivered service orchestration is inevitable.
How Cloudi-Fi helps
Cloudi-Fi accelerates this migration, delivering a cloud-native, identity-first approach that modernizes 802.1X and integrates it seamlessly with Zero Trust principles:
- Cloud RADIUS-as-a-Service (RaaS): Provides globally distributed PoPs utilizing RadSec for reliable, low-latency authentication across all sites and remote users, eliminating the UDP reliability challenge.
- Cloud PKI automation: Fully automates the certificate lifecycle management using SCEP and EST, integrating with major MDM platforms (Intune, Jamf) for zero-touch enrollment and renewal, dramatically reducing PKI-related outages.
- Hybrid identity unification: Offers native integration with cloud identity providers like Azure AD and Okta via SAML, while maintaining compatibility with on-prem AD/LDAP via secure proxying.
- Dynamic access control: Features advanced device profiling for IoT and BYOD, enabling automated, identity-driven dynamic segmentation via RADIUS attributes like VLAN ID and Tunnel-Private-Group-ID.
For enterprises seeking to reduce operational complexity while strengthening network security in the hybrid cloud era, Cloudi-Fi provides the comprehensive, cloud-native 802.1X solution.








