Understanding what a MAC address is and how it functions is crucial for anyone working with computer networks, troubleshooting network issues, or simply curious about how devices communicate with each other. In this comprehensive guide, we’ll explore the technical details, practical applications, and security considerations of MAC addresses in modern networking.
MAC address explained
A MAC address, formally known as a media access control address, is a unique 48-bit hardware identifier assigned to every network interface controller (NIC) in a device. This physical address serves as a permanent, hardware-level identifier that distinguishes one network interface from all others on a local network.
The media access control address is typically represented as twelve hexadecimal characters arranged in six pairs, separated by colons or hyphens. For example, a wireless MAC address might appear as 00:1A:2B:3C:4D:5E or 1A:2B:3C:4D:5E:6F. This format ensures that each MAC address identifies a specific network interface with near-universal uniqueness.

Every network adapter, whether wired or wireless, receives its own MAC address during the manufacturing process. This means a laptop with both an Ethernet port and Wi-Fi capability will have two distinct MAC addresses - one for each network interface. The device’s MAC address is burned into the network interface card by the manufacturer, creating what’s known as a “burned-in address” or hardware address.
The structure of a media access control MAC address consists of two main components:
- Organizationally Unique Identifier (OUI): The first 24 bits identify the manufacturer of the network interface card
- Device Identifier: The remaining 24 bits provide a unique identifier within the manufacturer’s assigned range
This 48-bit address space supports approximately 281 trillion possible MAC addresses, providing ample capacity for current and future networking needs. The Institute of Electrical and Electronics Engineers (IEEE) manages the allocation of OUIs to manufacturers, ensuring that each vendor receives a unique range of addresses for their network devices.
How MAC addresses work in networks
MAC addresses play a crucial role in local area network communication by operating at the data link layer of the OSI model. When a device connected to a local network wants to communicate with another device on the same network, it uses MAC addresses to ensure data reaches the correct destination.
Network switches and bridges maintain forwarding tables that associate MAC addresses with specific physical ports. When a frame arrives at a switch, the device examines both the source and destination MAC addresses. The switch learns the association between the source MAC address and the physical port, storing this information for future use. This process enables efficient frame forwarding within the local network.
In wireless networks, the Wi-Fi address (another term for wireless MAC address) serves a similar function. Access points use MAC addresses to identify and manage connected devices, implementing features like access control and device tracking. The Wi-Fi MAC address becomes particularly important in enterprise environments where network administrators need to monitor and control device access.
Types of MAC addresses
Network communication requires different types of MAC addresses to handle various communication patterns. Understanding these address types is essential for comprehending how network devices interact with each other.
Unicast MAC address
A unicast MAC address identifies a single, specific network device. This represents the most common type of MAC address, with each network interface receiving its own unique identifier. When a device sends a frame to a unicast MAC address, only the device with that specific address processes the frame.
The Individual/Group (I/G) bit in the MAC address indicates whether an address is unicast or multicast. For unicast addresses, this bit is set to 0, signaling that the address targets a single device rather than a group.
Multicast MAC address
Multicast MAC addresses enable efficient communication with groups of devices simultaneously. Instead of sending separate frames to each device, a sender can use a multicast MAC address to deliver data to all devices configured to receive that particular multicast stream.
The multicast address format uses the I/G bit set to 1, indicating group communication. Network protocols like IPv6 neighbor discovery and various routing protocols rely on multicast MAC addresses for their operation. These group addresses enable protocols to communicate with multiple devices without flooding the entire network.
Broadcast MAC address
The broadcast MAC address (FF:FF:FF:FF:FF:FF) represents a special case where all devices on the local network segment receive and process the frame. Broadcast addresses prove essential for network discovery protocols, DHCP requests, and other scenarios where a device needs to communicate with all reachable devices.
Network switches typically flood broadcast frames to all ports except the originating port, ensuring network-wide delivery. However, routers do not forward broadcast frames between different network segments, limiting broadcast traffic to the local area network.
MAC address vs IP address
While both MAC addresses and IP addresses serve as device identifiers, they operate at different layers of the network stack and serve distinct purposes in network communication.
The physical address (MAC address) enables communication within a single network segment, while the logical address (IP address) facilitates communication across multiple networks and the internet. Network devices require both types of addresses to function properly in modern networking environments.
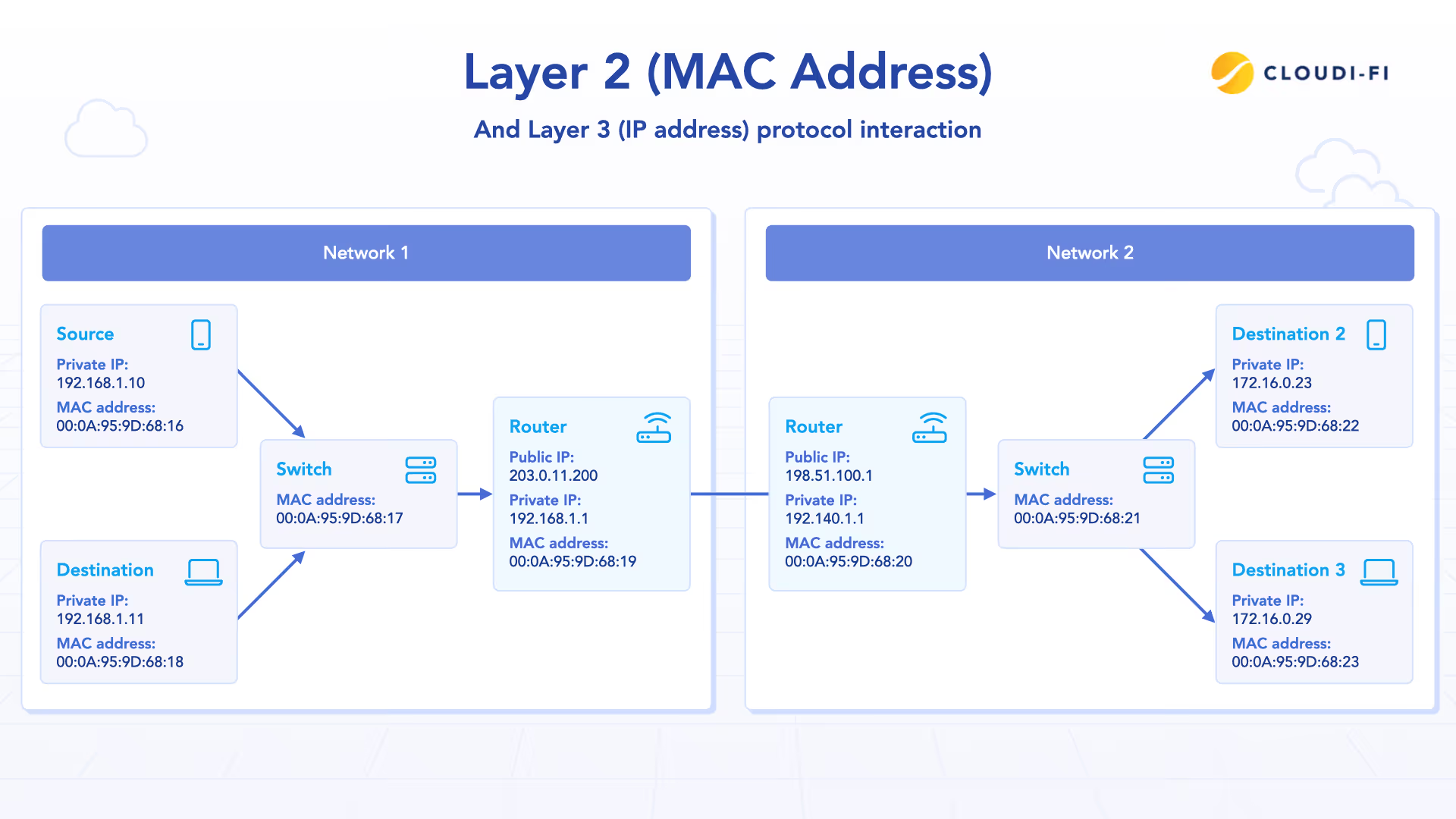
When a device sends data across network boundaries, routers use IP addresses for path determination while switches within each network segment use MAC addresses for local delivery. This complementary relationship ensures efficient data transmission from source to destination across complex network topologies.
The internet protocol relies on IP addresses for routing decisions, but the actual frame delivery within each network segment depends entirely on MAC addresses. Network address translation and routing protocols modify IP addresses as packets traverse different networks, while MAC addresses change at each network hop to reflect the current local delivery requirements.
MAC address security and spoofing
MAC address security typically involves filtering, where networks restrict access to a whitelist of approved devices. While useful, this method has limitations because MAC addresses can be spoofed, manually changed in software to impersonate another device.
This spoofing is possible through the locally administered address feature, which lets devices override the manufacturer-assigned hardware address. While this can support privacy (e.g., randomization to prevent tracking), it also creates opportunities for bypassing access controls.
Privacy, tracking, and MAC address randomization
A permanent, unique MAC address can unintentionally expose a device to tracking and profiling. Every time a device searches for Wi-Fi networks, it sends out probe requests containing its MAC address. Retail stores, airports, and other public spaces can collect these broadcasts to track movement, count foot traffic, or even build consumer behavior profiles.
This capability supports device fingerprinting, where networks or third parties create a persistent identity for a device without the user’s consent. Even if a device changes networks, its unchanged MAC address can allow continued tracking across different locations.
To protect privacy, modern operating systems have introduced MAC address randomization — also called private Wi-Fi addresses:
- iOS & iPadOS: Enable random MAC addresses by default on new Wi-Fi connections.
- Android: Randomization is default on newer versions and can be toggled per network.
- Windows 10/11: Offers random hardware addresses as a privacy option for wireless connections.
By periodically generating temporary, randomized MAC addresses, devices reduce the ability of networks and third parties to track them over time.
However, this privacy feature can present challenges for network management and troubleshooting. Many enterprise Wi-Fi systems and analytics tools still rely heavily on static MAC addresses to identify users, enforce access policies, or monitor network performance. As a result, IT teams may encounter difficulties when tracking devices, applying security controls, or diagnosing connectivity issues.
Common MAC address use cases
Network troubleshooting frequently involves MAC address identification and analysis. When network issues occur, administrators can trace communication problems by examining MAC address entries in switch forwarding tables, identifying the physical location of problematic devices, and diagnosing connectivity issues.
DHCP reservations rely on MAC addresses to provide consistent IP address assignments to specific devices. By associating a MAC address with a particular IP address, network administrators ensure that critical devices like servers and printers always receive the same network configuration, simplifying network management and reducing configuration errors.
Asset management in enterprise environments often incorporates MAC addresses as part of device inventory and tracking systems. Since MAC addresses provide unique hardware identification, organizations can maintain accurate records of network equipment, monitor device locations, and ensure compliance with licensing and security policies.
Wi-Fi access control systems commonly use MAC addresses for device identification and policy enforcement. Guest networks, parental controls, and bandwidth management features often rely on MAC address recognition to apply appropriate network policies to different device types and user categories.
FAQ
How to find your MAC address
Finding your MAC address varies depending on your device's operating system. Here are common methods with step-by-step instructions:
- Windows:
- Press the Windows key and type Command Prompt, then press Enter.
- In the Command Prompt window, type ipconfig /all and press Enter.
- Scroll through the results to find your active network adapter.
- Look for the "Physical Address" entry; this is your MAC address. Alternatively:
- Click the Start menu and select Settings.
- Navigate to Network & Internet > Status.
- Click on View hardware and connection properties.
- Find the MAC address listed under your active network connection.
- MacOS:
- Click the Apple menu and select System Preferences.
- Choose Network.
- Select your active network connection (Wi-Fi or Ethernet) from the sidebar.
- Click the Advanced button.
- Open the Hardware tab to view your MAC address.
- Linux:
- Open a terminal window.
- Type ifconfig or ip link and press Enter.
- Locate your network interface (e.g., eth0, wlan0).
- Find the MAC address listed as "ether" or "HWaddr".
- Android:
- Open Settings.
- Tap About Phone or About Device.
- Select Status or Hardware Information.
- Look for the Wi-Fi MAC address or similar entry.
- iOS:
- Open Settings.
- Tap General > About.
- Scroll down to find the Wi-Fi Address, which is the MAC address.
You may also find the MAC address printed on a label on the device or its packaging.










