Providing guest network access has become a baseline expectation in modern workplaces, retail spaces, and hospitality environments. Customers, partners, and employees expect instant connectivity when visiting your offices, stores, or campuses. Yet this convenience often masks one of the most overlooked security gaps in enterprise networks. Guest network security is critical, as unsecured networks can serve as entry points for attackers, distribute malware, or expose sensitive data, while creating compliance and reputational risks.
Organizations must implement guest Wi-Fi security best practices that address both technical vulnerabilities and operational challenges. A secure guest network requires a comprehensive, multi-layered approach combining technical controls, policy enforcement, and continuous monitoring.
Introduction to guest Wi-Fi security
A well-designed guest Wi-Fi network balances accessibility with security. By isolating guest devices from internal systems and combining encryption, identity verification, and device-aware policies, organizations protect both visitors and corporate resources. This approach prevents data theft, malware spread, and compliance issues while delivering a reliable, trustworthy connection.
Top security risks of unsecured guest Wi-Fi
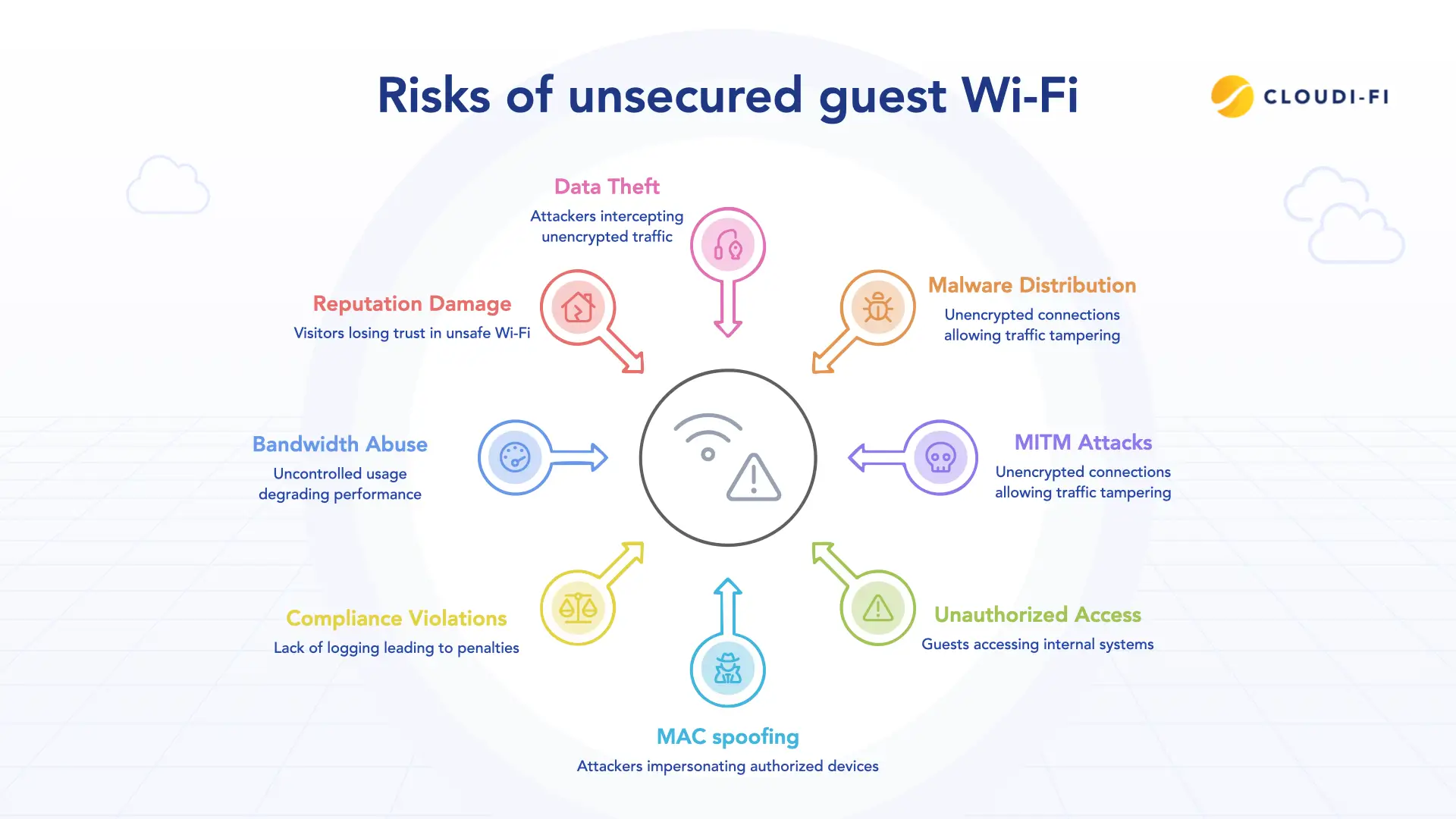
Unprotected guest Wi-Fi exposes enterprises to several risks:
- Data theft – Attackers intercept unencrypted traffic or steal credentials.
- Malware distribution – Compromised devices can spread malicious payloads across the network.
- Man-in-the-middle (MITM) attacks – Unencrypted connections allow traffic tampering.
- Unauthorized network access – Guests bridging into internal systems can exfiltrate sensitive data.
- MAC spoofing – Attackers impersonate authorized devices to bypass controls.
- Compliance violations – Lack of logging and retention can result in regulatory penalties.
- Bandwidth abuse – Uncontrolled usage degrades performance for employees and critical services.
- Reputation damage – Visitors losing trust in unsafe Wi-Fi experiences.
These risks are fully manageable when enterprises apply guest Wi-Fi security best practices grounded in modern networking principles.
Guest Wi-fi network architecture
Designing a guest Wi-Fi network is not just about connectivity—it is about embedding security, privacy, and operational resilience into the very fabric of the network. While earlier sections focus on risks and tactical best practices, this section addresses architecture-level decisions that determine how guest access integrates with enterprise systems, protects internal resources, and scales across locations.
To achieve this, guest networks should be built around several core architectural principles that ensure security, compliance, and a seamless user experience:
1. Network segmentation as a foundation
Beyond basic VLANs, segmentation should be policy-driven and enforceable at every layer, from AP to firewall to cloud management. Guest traffic must be strictly isolated from employee, IoT, and sensitive networks, ensuring any compromise remains contained.
2. Layered security by design
Architectural decisions should embed multi-layered protections including client isolation, secure DNS, WPA3 OWE, and controlled firewall policies. These mechanisms are baked into the network, not retrofitted, so protection is consistent, auditable, and enforceable without manual intervention.
3. Identity-aware access
Integrating authentication at the architectural level—via captive portals, OTPs, or social logins—enables accountability and regulatory compliance from the outset. Policies should allow context-aware access, adapting permissions based on device type, posture, and user role.
4. Observability and auditability
A robust architecture incorporates logging, telemetry, and continuous monitoring. This ensures all sessions are trackable, anomalies are detectable early, and compliance reporting is automated rather than reactive.
5. Scalability and operational resilience
Cloud-managed or centrally orchestrated networks allow uniform enforcement of policies across multiple sites, support peak traffic seamlessly, and minimize manual configuration errors. Scalability and automation become integral to the network’s architecture rather than afterthoughts.
13 best practices for guest Wi-Fi security
1. Network segmentation and isolation
The most fundamental control for guest Wi-Fi security is strict separation from the corporate LAN. This is achieved through VLANs (Virtual Local Area Networks), which logically divide traffic into isolated segments, ensuring that guest devices cannot communicate with internal servers, employee workstations, or sensitive applications. Firewalls reinforce this boundary by explicitly blocking guest-to-corporate traffic.
Within the guest network itself, implement IP isolation (also called client isolation). This prevents guest devices from seeing or communicating with each other, stopping malware or worms from spreading laterally between visitors.
To further harden the environment:
- DHCP snooping ensures that only authorized DHCP servers can respond to client requests, blocking rogue DHCP attacks.
- DHCP guard prevents unauthorized devices from acting as DHCP servers, a common attack vector for redirecting traffic.
- Port security and dynamic ARP inspection (DAI) protect against MAC spoofing, ensuring attackers cannot impersonate another device to bypass access restrictions.
Together, these mechanisms create a layered defense that isolates guests, prevents impersonation, and ensures network integrity.
“Segmentation is the security cornerstone when it comes to implementing guest Wi-Fi – guest access must live on a completely isolated network. Implement VLANs or physical separation to create an air-gapped barrier between visitors and your internal infrastructure. A guest device should be treated as a zero-trust entity. When (not if) one is compromised, that threat must be contained instantly. No segmentation means a rogue device could instantly pivot into a breach of your core systems.” — Kevin Walker, Founder, Black Swan Cyber Security Solutions
2. Captive portals with identity controls
A captive portal is more than a splash page—it’s the identity gateway to your guest network. The distinction between anonymous and identity-based access is critical. With anonymous access, you have no visibility into who connected or what activity they performed. With identity-based access, each session is tied to a real user through mechanisms such as SMS verification, email validation, social logins, or corporate SSO.
From a compliance perspective, identity binding is essential. Regulations such as GDPR, HIPAA, PCI DSS, and local telecom laws often require organizations to maintain detailed logs of who connected, when, and what they did. Without identity controls, an enterprise cannot demonstrate accountability, leaving itself exposed in the event of a regulatory audit or legal investigation.
By capturing user identity and correlating it with network activity, the captive portal provides:
- A clear audit trail for security teams and regulators.
- Non-repudiation, ensuring users cannot deny their activity.
- The ability to perform forensic investigations if malicious or illegal activity originates from the guest network.
This transforms the guest network from an unmanaged liability into a compliant, controlled, and accountable service.
3. Opportunistic wireless encryption (OWE)
Traditional open Wi-Fi is inherently insecure because all traffic is transmitted in cleartext, making it trivial for attackers to intercept. Opportunistic Wireless Encryption (OWE), part of the WPA3 standard, solves this problem. It automatically establishes a unique, encrypted session key for every client when they connect, without requiring a shared password.
OWE provides:
- Confidentiality, by preventing passive eavesdropping.
- Protection against man-in-the-middle (MITM) attacks, since each client session is individually encrypted.
- Ease of use, as users connect as they would on an open network, but with the added benefit of encryption.
This makes OWE a perfect balance of usability and privacy, ensuring guest traffic is no longer exposed to everyone in range of the access point.
4. TLS certificates for captive portals
When a guest device is redirected to a captive portal, trust is established at the very first click. If the portal lacks a valid TLS certificate signed by a recognized certificate authority, browsers display warnings that undermine confidence and may push users to disconnect entirely.
By deploying properly managed certificates:
- Guests are guaranteed a secure HTTPS connection to the portal.
- The risk of session hijacking or MITM attacks during redirection is minimized.
- The organization projects professionalism and trustworthiness from the start.
Certificates should be renewed automatically, centrally managed, and aligned with the organization’s overall PKI and TLS policies.
5. Bandwidth controls and QoS
Guest Wi-Fi isn’t just a security concern — it can also impact business productivity. Without controls, a single guest streaming 4K video can degrade performance for business-critical apps like VoIP or video conferencing.
Implement Quality of Service (QoS) and per-user bandwidth limits to ensure fair distribution and prioritization:
- Business traffic first: Prioritize apps such as CRM, ERP, or Microsoft Teams over guest sessions.
- Per-session caps: Limit guest bandwidth to prevent abuse.
- Dynamic shaping: Adjust limits based on network load.
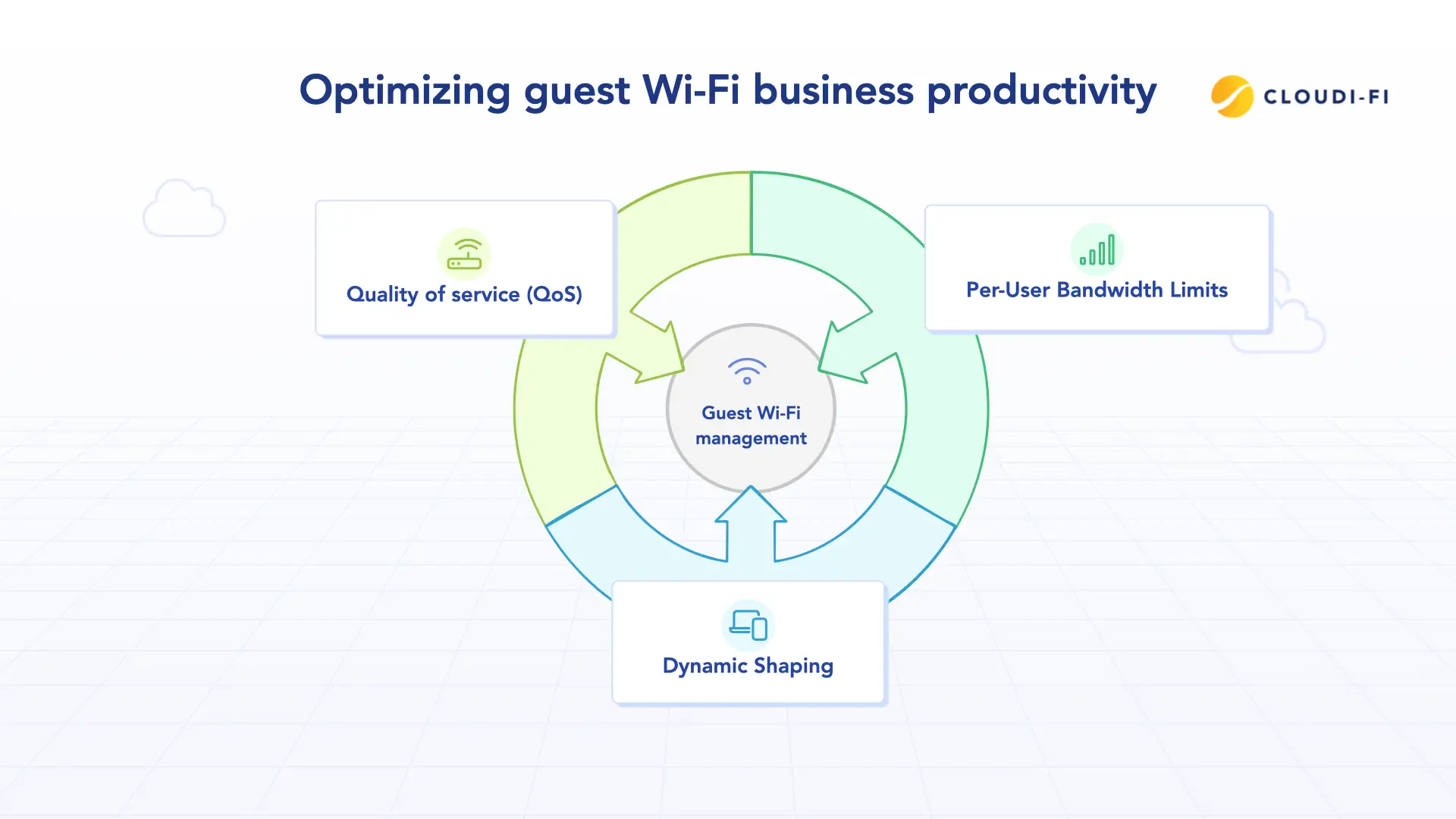
This ensures that guest access is available, but never at the expense of employees or corporate operations.
6. Layered content filtering and firewall rules
Protecting both guests and the enterprise requires defense-in-depth. A single firewall rule isn’t enough. Instead, use multiple layers of filtering:
- DNS security to block requests to malicious domains.
- URL filtering to restrict categories like adult content, gambling, or known phishing sites.
- Application-aware firewalling to block risky services like peer-to-peer file sharing or anonymizers.
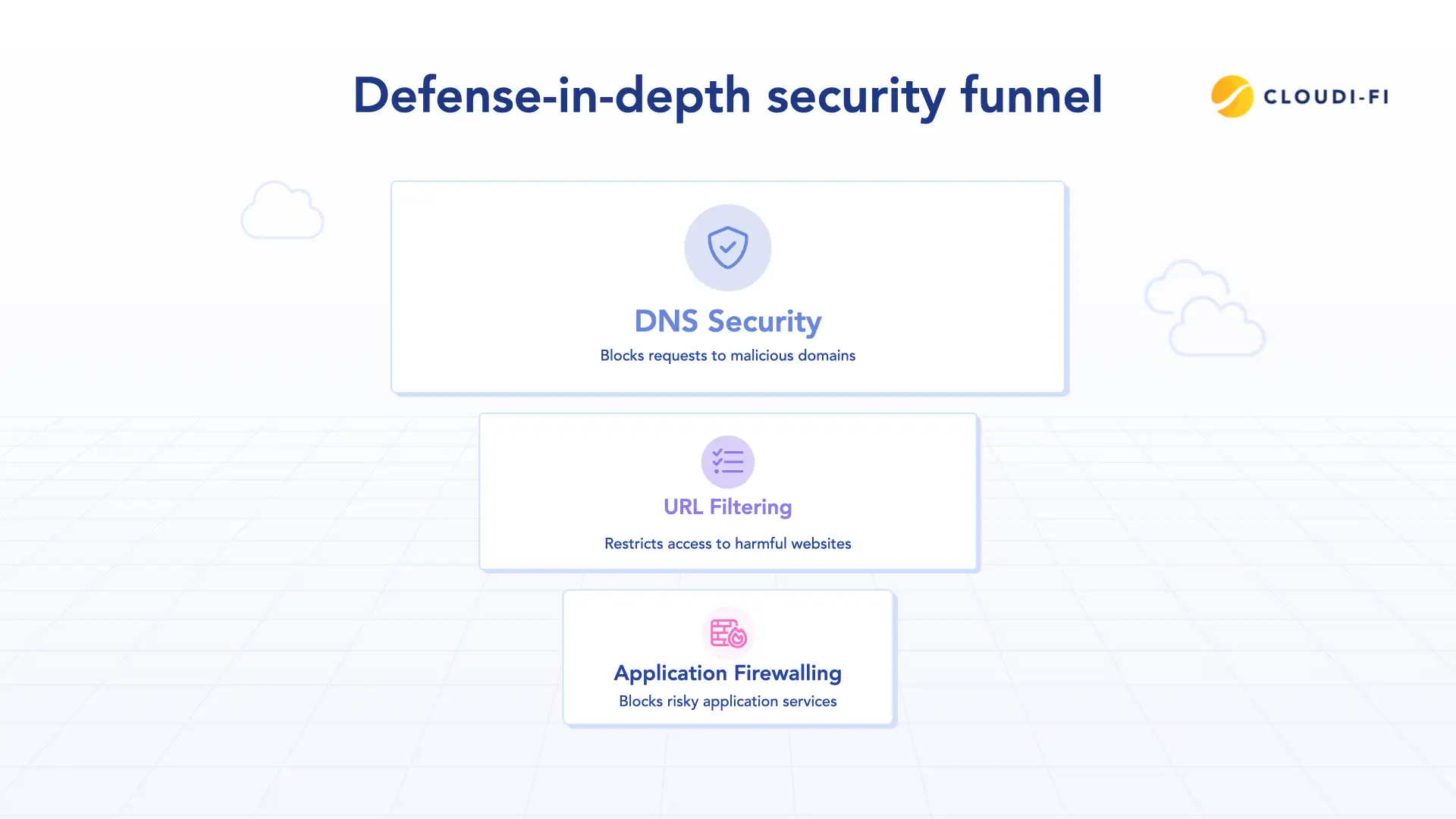
Layering these defenses reduces risk exposure and adapts more effectively to emerging threats, ensuring malicious traffic is stopped before it can cause harm.
7. Time-limited access
Persistent guest sessions create unnecessary security risks. For example, a forgotten session left active on a tablet can be exploited days later. Time-limited access solves this by automatically disconnecting or requiring reauthentication after a set period (e.g., 24 hours).
This provides:
- Risk reduction, by eliminating stale connections.
- Session accountability, ensuring each connection is recent and intentional.
- Better reporting accuracy, as logs reflect active sessions only.
8. Device fingerprinting
MAC addresses alone are insufficient for security since they can be easily spoofed. Device fingerprinting goes deeper by analyzing attributes such as OS, browser, device type, and behavior patterns to generate a unique identity.
Benefits include:
- Context-aware policies: For example, a corporate laptop can be granted broader access than a personal smartphone.
- IoT visibility: Smart devices connecting to guest networks can be identified and monitored.
- Zero Trust extension: Access policies are no longer static but adaptive to device type and posture.
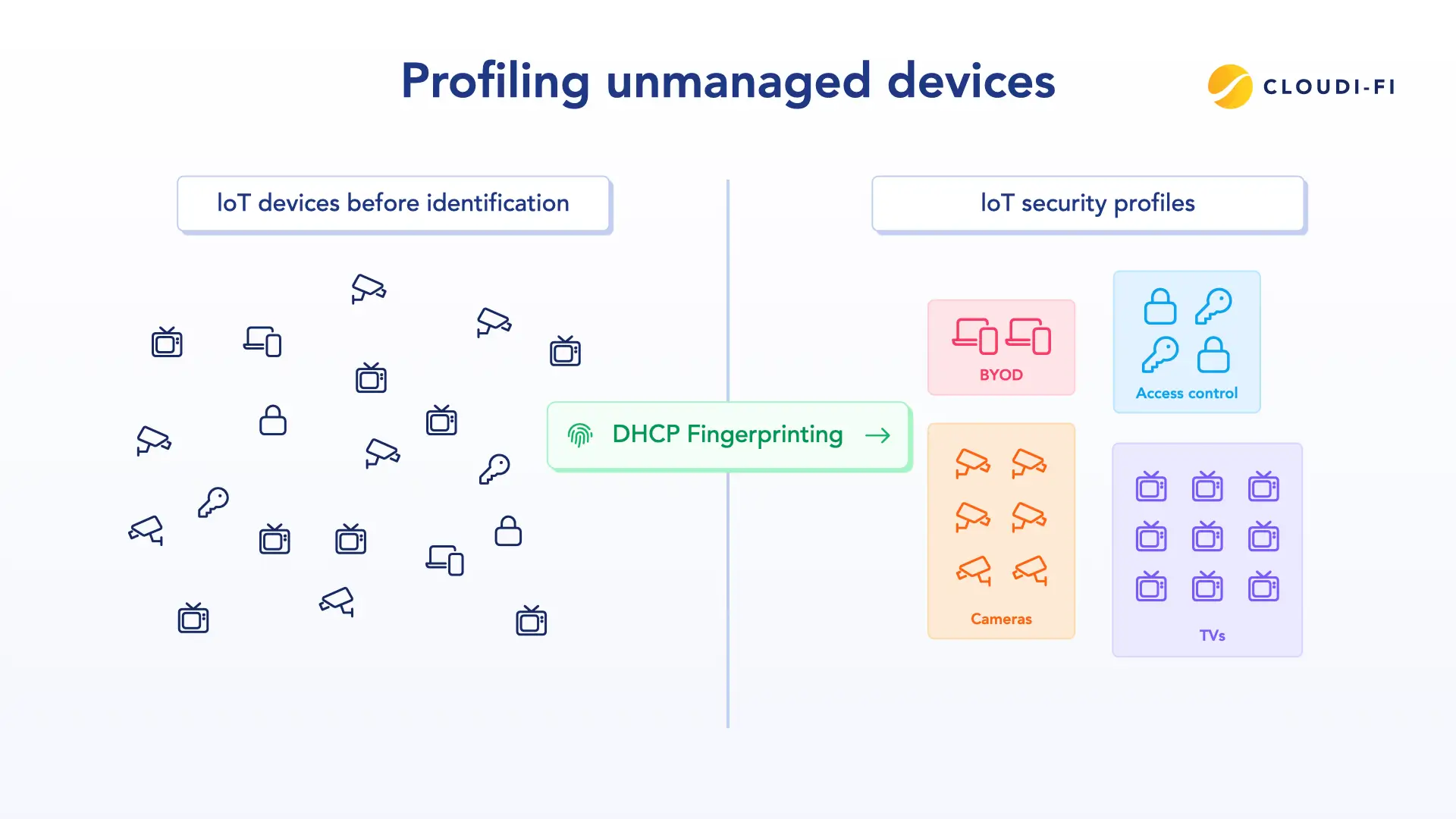
This ensures that policies are granular, dynamic, and harder for attackers to bypass.
9. Logging and compliance reporting
Detailed logging is non-negotiable for both security and compliance. At minimum, the system should record:
- User identity (if available).
- Device identifiers (MAC, fingerprint).
- Connection timestamps and session duration.
- Assigned IP addresses.
- Activity logs if legally required (varies by jurisdiction).
These logs are crucial for:
- Regulatory compliance (GDPR, HIPAA, PCI DSS, telecom regulations).
- Incident response, enabling forensic reconstruction of events.
- Audit readiness, demonstrating accountability to regulators and stakeholders.
10. Zero Trust access control
Zero Trust applies the principle of “never trust, always verify” to guest Wi-Fi. Instead of granting blanket access after authentication, policies continuously evaluate context such as:
- Device type and security posture.
- Time of day and location.
- User role or identity source.
This transforms guest access from a static permission into a dynamic evaluation process. A visitor may only access the internet, while a contractor using a corporate laptop may gain temporary access to collaboration tools — all enforced in real time.
11. Seamless integration with existing infrastructure
A guest Wi-Fi solution must integrate with the organization’s existing firewalls, APs, identity providers, and cloud security tools. This prevents the creation of isolated silos and avoids costly rip-and-replace projects.
Benefits include:
- Simplified administration through a single policy framework.
- Consistent enforcement across both guest and employee networks.
- Operational efficiency, reducing overhead for IT teams.
Integration ensures security enhancements do not come at the expense of complexity or manageability.
12. Cloud-based scalability
For multi-site organizations, managing hardware-based guest Wi-Fi solutions at each location is inefficient and error-prone. A cloud-native platform centralizes control, delivering:
- Uniform policy enforcement across all offices, branches, or retail locations.
- Simplified deployment, with no need for local configuration.
- Elastic scalability, handling seasonal or event-driven traffic spikes seamlessly.
This model reduces operational overhead while providing a consistent, secure guest experience everywhere.
13. User experience monitoring
Security without usability fails its purpose. Monitoring onboarding success rates, connection times, and latency ensures guests have a smooth experience. Poor connectivity directly impacts brand perception, especially in hospitality, retail, or customer-facing industries.
By continuously monitoring and analyzing user experience:
- IT teams can proactively fix issues before they impact visitors.
- Security controls can be tuned to minimize friction.
- The organization demonstrates care for both security and customer satisfaction.
This balance reinforces trust, encouraging guests to use the service without hesitation.
Conducting regular security audits
Securing a guest Wi-Fi network is not a one-time task—it demands continuous oversight and proactive validation. Regular security audits are essential to identify emerging vulnerabilities, verify that controls are functioning as intended, and ensure compliance with internal policies and regulatory requirements. These audits should encompass network segmentation, firewall rules, authentication mechanisms, device posture assessments, and encryption standards, providing a comprehensive view of the network’s security posture.
Beyond threat detection, systematic audits enable enterprises to:
- Update and optimize controls: Identify gaps or outdated configurations and implement corrective measures before they are exploited.
- Demonstrate compliance: Maintain detailed records of guest access and security measures for regulatory audits or internal reporting.
- Enhance trust and reliability: Reassure stakeholders and visitors that guest connectivity is safe, monitored, and professionally managed.
By institutionalizing regular audits as part of operational governance, organizations transform guest Wi-Fi from a potential liability into a resilient, trusted, and strategically managed service.
Transforming guest Wi-Fi into a secure enterprise network
Guest Wi-Fi doesn’t have to be a liability. By applying these guest Wi-Fi security best practices, and understanding the fundamentals of guest network design, enterprises can protect against data theft, malware, MAC spoofing, compliance violations, and performance issues. A secure guest network becomes a professional, trusted, and business-enhancing service rather than a liability.
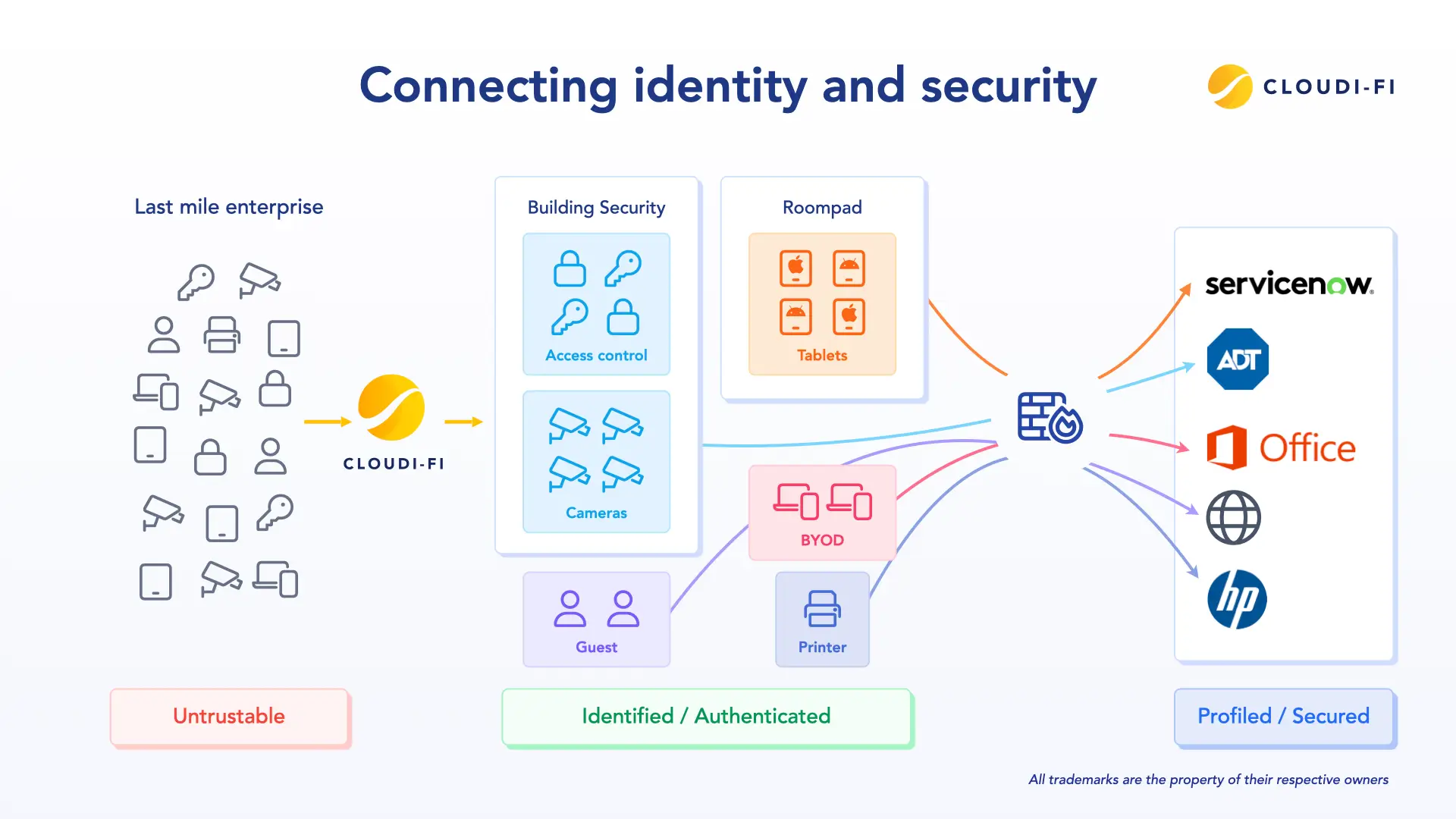
For organizations looking to modernize guest network security, Cloudi-Fi offers a cloud-native platform that delivers comprehensive identity-based access control, device fingerprinting, and Zero Trust enforcement. With Cloudi-Fi, enterprises can:
- Enforce granular, context-aware policies for every user and device, including BYOD and IoT.
- Centralize logging and compliance reporting for audits and regulatory alignment.
- Apply Zero Trust principles to the guest network, continuously authenticating and validating access.
- Scale policies across multiple sites without added hardware complexity.
With Cloudi-Fi, guest Wi-Fi is no longer just a convenience — it becomes a strategic asset that safeguards operations, protects your brand, and delivers a seamless, secure experience for every visitor.








