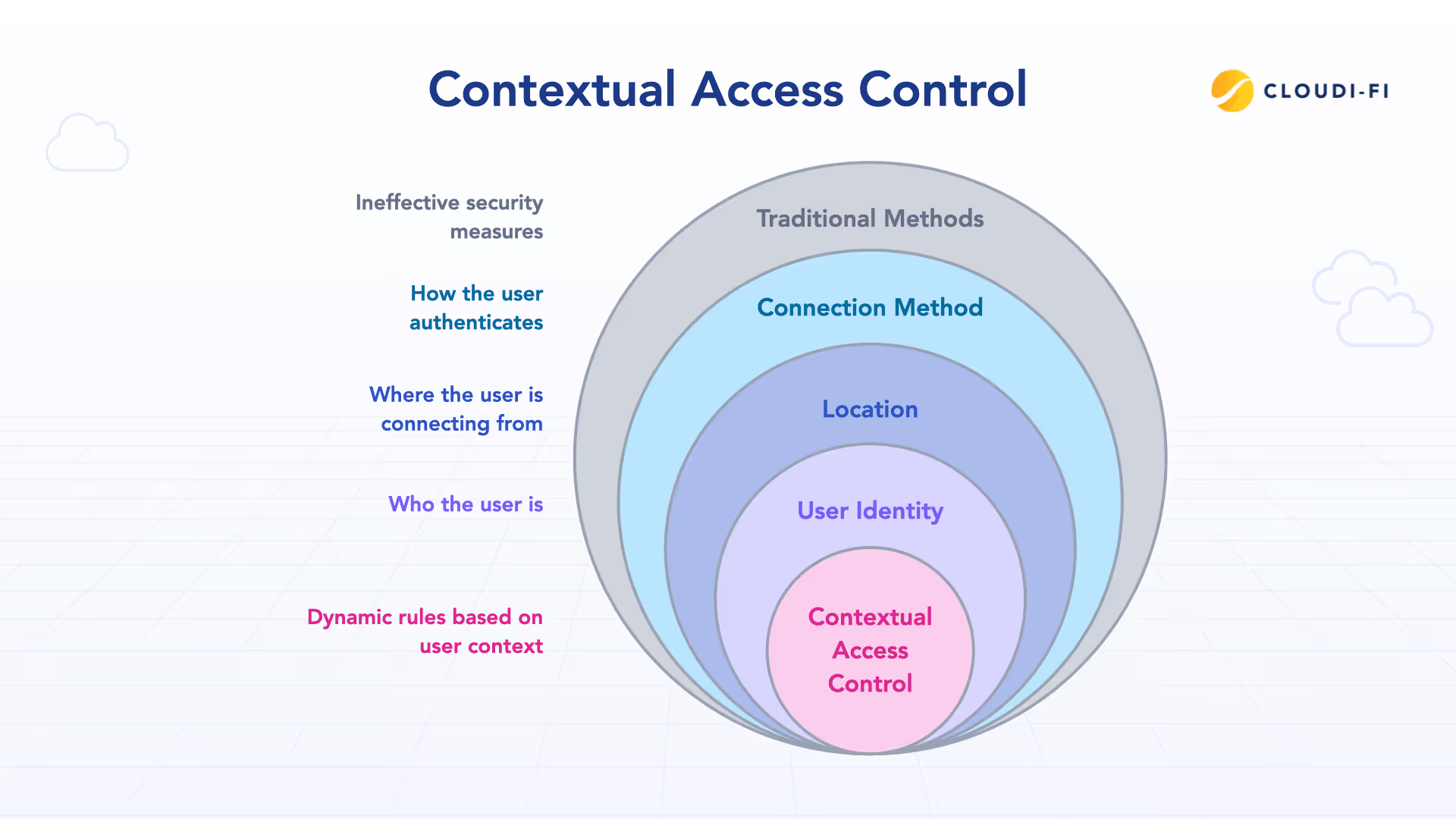
Rethinking access control: Context is everything
Traditional network security methods, such as VLANs, static IPs, and device categories, are becoming increasingly ineffective in modern networks. Users now move freely between locations, connect using personal devices, and authenticate through various methods like SSO, guest registration, or sponsor approval. This necessitates a shift towards contextual access control, where rules dynamically adapt based on user identity, location, and connection method.
The integration of Cloudi-Fi and FortiGate addresses this need by enabling dynamic policy enforcement based on rich user context gathered during authentication through a captive portal.
Alain Sanchez, Field CISO (EMEA) at Fortinet, on the Fortinet × Cloudi-Fi value proposition:
“The new era of cybersecurity requires real time flexibility and granularity in managing all aspects of access and identity. The combined holistic value proposition of Fortinet and advanced network access solutions from Cloudi-Fi enables a swift, policy-based implementation of the next generation of zero trust network access.”
Profiles as the foundation of access control
When a user connects through a Cloudi-Fi-powered captive portal, they are automatically assigned a profile. This profile is determined by several factors:
- The authentication method used (SSO, social login, email-based, or sponsor-validated).
- The sponsor or lobby admin who provisioned the account.
- Network parameters such as SSID and location.
Each profile corresponds to a preconfigured set of RADIUS attributes returned to the FortiGate firewall during the authentication handshake. A critical attribute is Fortinet-Group-Name, which follows a naming convention like cloudifi-Employees, cloudifi-Guests, or cloudifi-Vendors.
This approach eliminates the need for static mappings and enables flexible policy enforcement without manual group assignment or VLAN configuration on the firewall.
Example: From identity to policy in real time
A contractor connects to the corporate Wi-Fi:
- The contractor logs in via a sponsor-approved captive portal form.
- Cloudi-Fi assigns them the Vendors profile based on the authentication method and approval process.
- This profile triggers a RADIUS Access-Accept message containing Fortinet-Group-Name = cloudifi-Vendors.
- FortiGate matches this attribute to a user group and applies a specific firewall policy—e.g., access to a Git repository and internal documentation, but no access to finance systems.
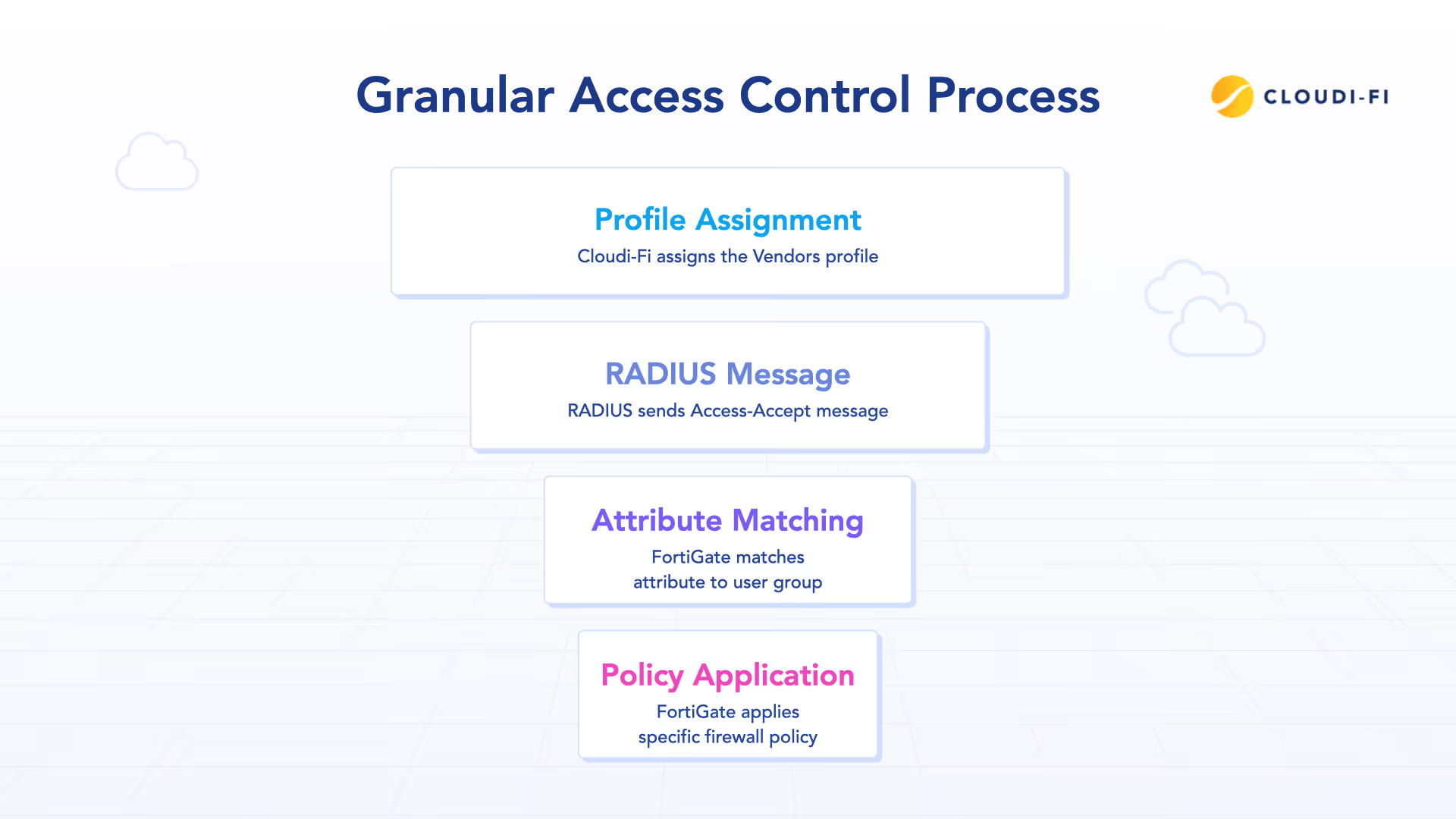
In this example, the contractor’s access is shaped in real time without any static firewall reconfiguration.
Use cases in action
The FortiGate–Cloudi-Fi integration supports a wide range of practical access control scenarios:
- Guests can be isolated from internal resources while maintaining internet access, with rules scoped by location or SSID.
- Employees logging in via enterprise SSO can access collaboration tools and internal dashboards, while other users are restricted to essential services.
- Bandwidth limits can be enforced per profile to prioritize operational traffic—for example, guest traffic can be capped at 5 Mbps.
- Temporary accounts or visitors can be restricted to defined timeframes using FortiGate’s schedule capabilities linked to Cloudi-Fi profiles.
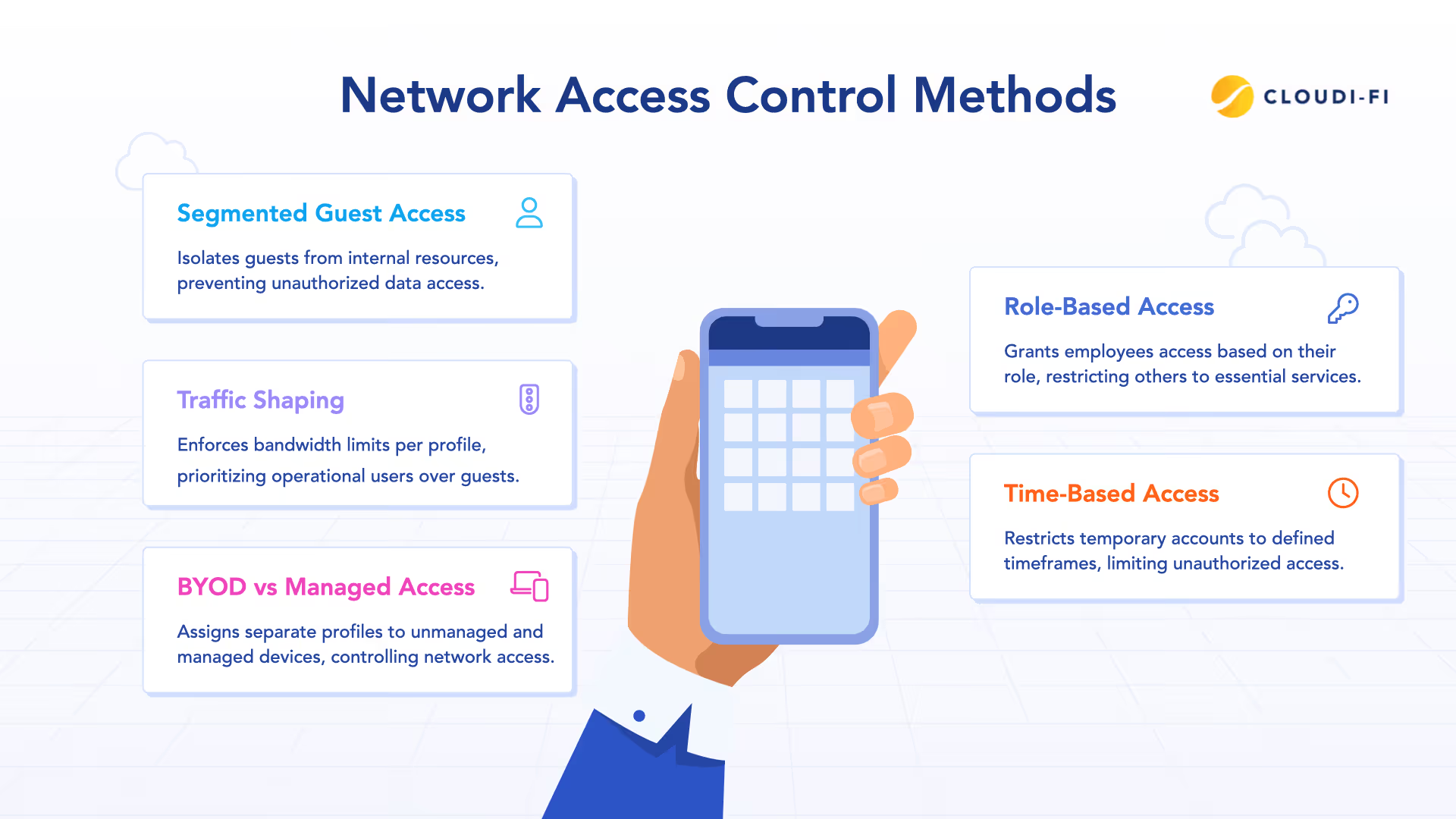
These scenarios support Zero Trust principles by reducing reliance on network location or device assumptions and instead applying policies based on identity and intent. By verifying each user and device before granting access, the risk of unauthorized access is significantly reduced.
Key architectural advantages
This model delivers several operational benefits:
- Decentralized Policy Definition, Centralized Enforcement: Cloudi-Fi handles identity and policy decisions in the cloud, while FortiGate enforces rules locally at the network edge. This separation of concerns simplifies management and improves scalability.
- No Reliance on On-Prem NAC: There's no need to maintain legacy network access control appliances or VLAN sprawl. This reduces the complexity and cost of network infrastructure.
- Dynamic Session-Based Enforcement: User sessions are reevaluated on each login, allowing updated policies to take effect without manual intervention. This ensures that access policies are always up-to-date and reflect the latest security requirements.
Read our blog on Internet on the Edge with Starlink & Cloudi-Fi.
Conclusion
As enterprise networks grow more dynamic and user identities more varied, fine-grained, adaptive access control becomes a baseline requirement. FortiGate and Cloudi-Fi provide a scalable, cloud-native way to enforce policies that follow the user, not the device or subnet.
This integration enables IT teams to simplify operations while adhering to Zero Trust principles—making access control not just a firewall rule, but a reflection of business logic. By leveraging the power of cloud-based identity management and network security, organizations can create a more secure and efficient network environment.
Start your journey with Cloudi-Fi by clicking Get Cloudi-Fi button.
Learn about Fortinet x Cloudi-Fi partnership








