Securing employee Wi-Fi is no longer optional. With cloud applications, IoT devices, and remote work on the rise, corporate networks face increasingly sophisticated threats. WPA2/3-Enterprise with 802.1X authentication provides the foundation for secure, scalable, and future-proof wireless access.
Introduction to WPA2/3-Enterprise
WPA2/3-Enterprise is the advanced Wi-Fi security standard for modern businesses. It moves beyond simple shared passwords to provide strong protection, individual user authentication, and strict, identity-based access control. By making every connection unique and auditable, it keeps wireless networks secure, compliant, and ready for today’s complex device ecosystem.
The evolution of Wi-Fi security: From WEP to WPA3
Understanding modern enterprise Wi-Fi security requires a look back at the historical evolution of Wi-Fi encryption standards.
WEP (Wired Equivalent Privacy)
Introduced in the late 1990s, WEP aimed to offer "wired-equivalent" security for wireless networks. However, its design flaws made it highly insecure:
- Static, Short Keys: WEP used fixed 40- or 104-bit keys, combined with a 24-bit Initialization Vector (IV).
- Key-Stream Reuse Vulnerability: The IV was transmitted in plain text and reset frequently, leading to repeated key streams. This allowed attackers to crack WEP with tools like Aircrack-ng in minutes.
WPA (Wi-Fi Protected Access)
WPA was a transitional standard bridging WEP and WPA2. It introduced TKIP (Temporal Key Integrity Protocol), which acted as a "wrapper" around the WEP encryption algorithm (RC4):
- Per-Packet Key Mixing: Ensured that each transmitted packet used a unique encryption key.
- Message Integrity Check (MIC): Detected tampering of wireless frames.
While TKIP significantly improved security over WEP, it did not fundamentally fix RC4’s cryptographic weaknesses, leaving residual vulnerabilities.
Network architecture
A strong WPA2/3-Enterprise setup depends on a well-structured network architecture. Key principles include:
- Strategically placed access points (APs): Ensures consistent wireless coverage and optimal performance throughout the enterprise environment.
- RADIUS server deployment: Centralizes authentication and supports flexible EAP methods to validate users and devices dynamically. Access points are added as RADIUS clients in the authentication server configuration.
- Segmentation and policy enforcement: Allows administrators to control access per user, device type, profiles, location...Network policies can be enforced by dynamically assigning VLANs to manage client traffic based on user roles or device types.
By combining access points with a robust RADIUS server and flexible authentication methods, enterprises can securely manage and control wireless access while providing a seamless experience for trusted users and devices.
WPA2/3-Enterprise and 802.1X: The authoritative security framework
The limitations of WEP and WPA paved the way for WPA2 and WPA3-Enterprise, which rely on 802.1X authentication to provide strong, per-user security.
WPA2-Enterprise vs. WPA2-Personal
The primary difference lies in credential management and key generation:
- WPA2-Personal (PSK): Uses a single Pre-Shared Key (PSK) for all users. If one user leaves or their key is compromised, all network security is instantly jeopardized.
- WPA2-Enterprise (802.1X): Eliminates the PSK entirely, replacing it with individual credentials and dynamic session keys, providing stronger security and full auditability.

The 802.1X framework and the EAP stack
802.1X is a port-based network access control protocol, utilizing the Extensible Authentication Protocol (EAP) to handle authentication.
Key components:
- Supplicant: The client device requesting access.
- Authenticator: The network device (typically an Access Point) controlling the physical network port.
- Authentication Server: A RADIUS server validating credentials against a backend database (e.g., Active Directory).
The EAP state machine: Establishing trust
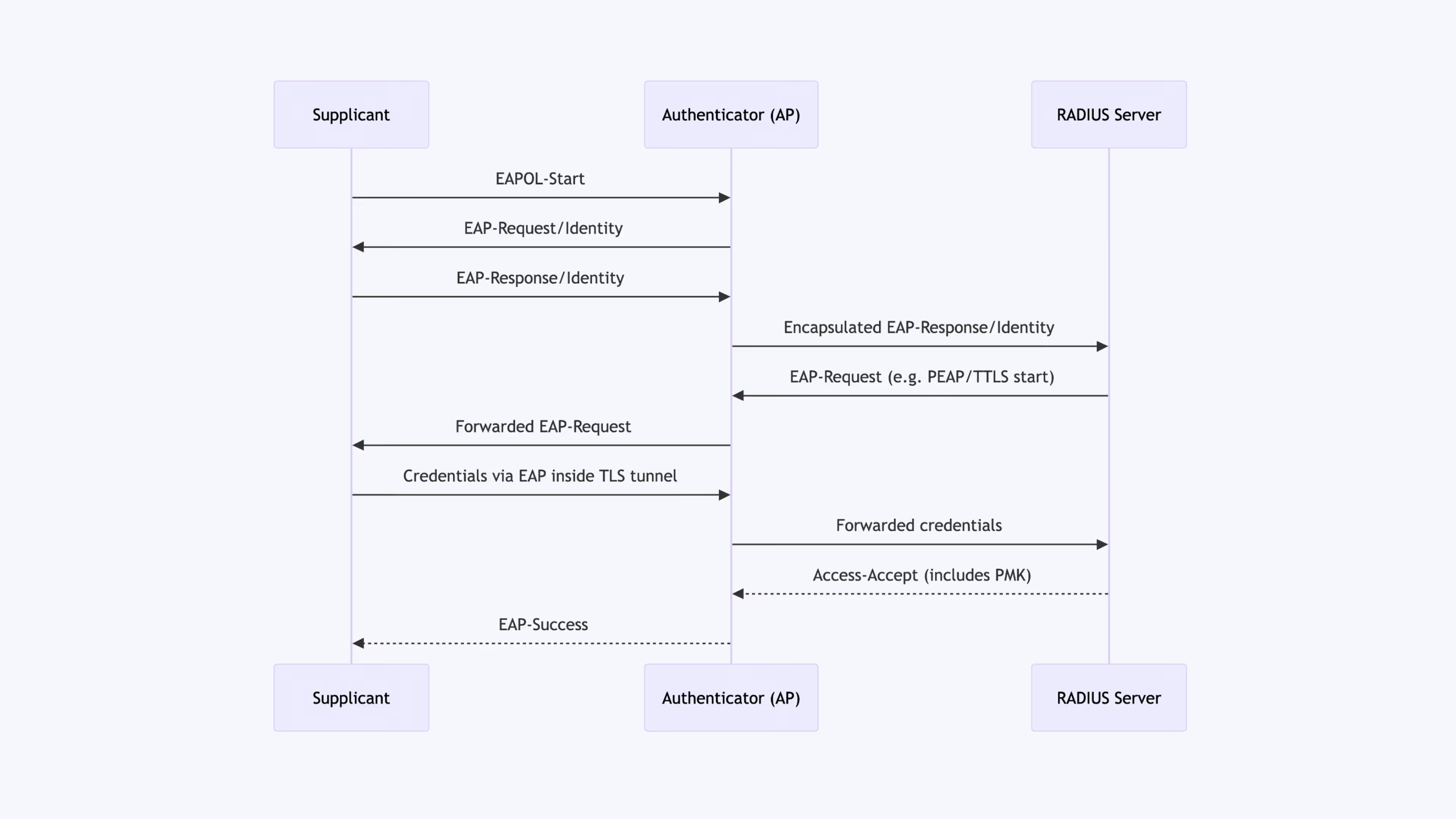
EAP is a framework, not an authentication method itself. The authentication process involves a specific state machine:
- Initiation: The Supplicant sends an EAP-Start (or EAPOL-Start) frame.
- Identity Request: The Authenticator (AP) responds with an EAP-Request/Identity.
- Authentication Exchange: The Supplicant responds with its identity. The AP encapsulates the EAP messages and forwards them to the RADIUS Server.
- EAP Tunneling (PEAP/TTLS): For methods like PEAP, a secure TLS tunnel is first established between the client and the RADIUS server using the server's certificate. Only then are the inner credentials (username/password) securely transmitted.
- Access Decision: The RADIUS server returns an Access-Accept or Access-Reject. Upon acceptance, the RADIUS server securely shares the generated Pairwise Master Key (PMK) with the Access Point.
The four-way handshake: Cryptographic key derivation
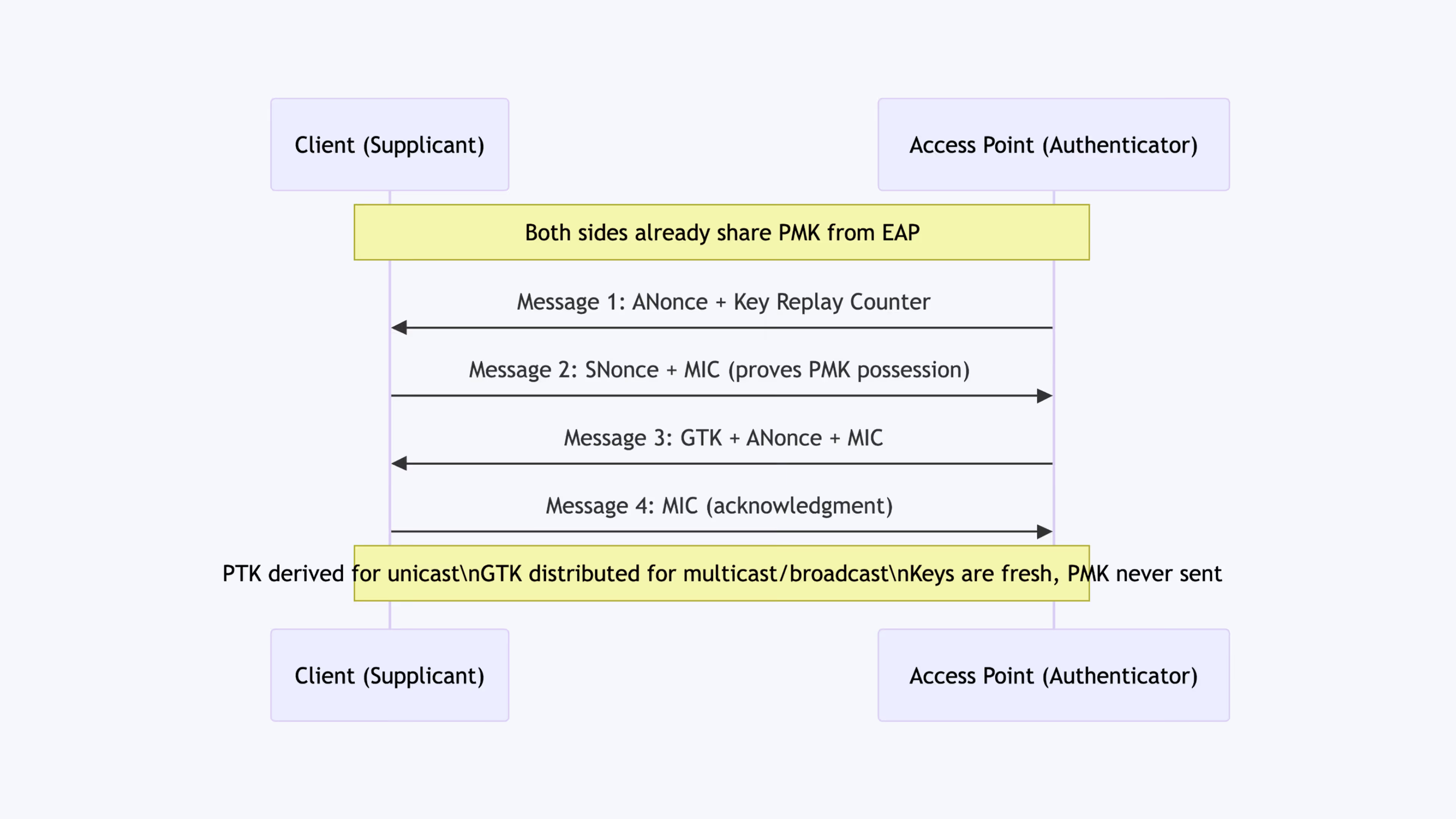
Following successful EAP authentication, the PMK is used to secure the actual wireless session via the Four-Way Handshake:
- PMK Derivation: The Pairwise Master Key (PMK) is derived from the successful EAP exchange. This is the cryptographic secret that distinguishes Enterprise security from PSK.
- PTK Generation: The PMK is used to generate the Pairwise Transient Key (PTK), which encrypts unicast (client-to-AP) traffic.
- GTK Generation: The AP also generates the Group Transient Key (GTK) for encrypting broadcast/multicast traffic.
- Key Freshness: The handshake proves that both the client and AP possess the PMK without ever sending the PMK itself, and it establishes key freshness to prevent replay attacks.
Authentication methods for 802.1X Wi-Fi
When implementing 802.1X, different EAP-based authentication methods provide flexibility depending on security requirements and organizational infrastructure:
- EAP-TLS (Transport Layer Security):
The most secure method, leveraging client and server certificates. Commonly used for company-issued laptops or high-security devices. - PEAP (Protected EAP):
Encapsulates a simple authentication method, like MS-CHAPv2, inside a TLS tunnel. This allows the secure use of existing username/password credentials, such as Active Directory accounts. - EAP-TTLS (Tunneled TLS):
Similar to PEAP but more flexible, supporting multiple inner authentication protocols within a TLS tunnel. Useful in mixed-device environments. - EAP-FAST (Flexible Authentication via Secure Tunneling):
Cisco’s method that provides secure authentication without requiring client certificates, often used in BYOD scenarios.
Selecting the right authentication method balances security, scalability, and user convenience.
Explore the full 802.1X explanation.
Key deployment and operational considerations
Implementing WPA2/3-Enterprise requires careful planning and deep infrastructure integration.
RADIUS server high availability and configuration
- Redundancy and Load Balancing: Critical for large deployments. If a single RADIUS server fails, new Wi-Fi connections are blocked. Deploy primary and secondary servers, and consider Load Balancing for massive environments to distribute authentication load.
- Client Configuration: The client must be configured to trust the RADIUS server's certificate. A common failure is a client not trusting the Root Certificate Authority (CA) that issued the RADIUS server's certificate.
Public key infrastructure (PKI) authority
For certificate-based methods like EAP-TLS (the most secure), a robust PKI is essential:
- Mutual Authentication: EAP-TLS requires both the client and the server to present a certificate, proving identity to each other and eliminating the threat of a man-in-the-middle attack using a rogue RADIUS server.
- Lifecycle Management: Automation is mandatory. Use protocols like SCEP (Simple Certificate Enrollment Protocol) or NDES (Network Device Enrollment Service) to automate the enrollment, renewal, and revocation (OCSP/CRL) of client certificates.
Advanced Troubleshooting: Technical deep dive
WPA3 & Zero Trust: Concrete technical detail
WPA3 and Zero Trust Architecture (ZTA) represent the future of security, and the wireless network is the crucial enforcement point.
WPA3-Enterprise: The gold standard for encryption
WPA3 introduces critical security upgrades over WPA2:
- SAE (Simultaneous Authentication of Equals): Replaces the WPA2-Personal PSK handshake with a secure key establishment protocol that is resilient to offline dictionary attacks—a major WPA2 weakness.
- Enhanced Open (OWE): Provides opportunistic encryption for open networks (like guest Wi-Fi) by ensuring that even if authentication isn't used, the traffic cannot be passively snooped.
- 192-bit Security Mode: WPA3-Enterprise offers an optional, high-security mode leveraging Suite B cryptography, ideal for government or defense networks. This mode mandates:
- AES-256 encryption.
- SHA-384 for message integrity and key derivation.
- This provides a cryptographic basis for securing highly sensitive data.
Wireless as the Zero Trust Policy Enforcement Point (PEP)
Modern cybersecurity is shifting from perimeter defense to Zero Trust Architecture (ZTA): “never trust, always verify.” In this model, the wireless network is the first line of defense.
- Identity-Based Verification: WPA2/3-Enterprise with 802.1X ensures that before a device can access any resource, both the user identity and the device identity (via certificate/MAC) are verified. The connection doesn't just grant network access; it authenticates a subject.
- Policy Enforcement Point (PEP): The Access Point and the integrated Network Access Control (NAC) system act as the ZTA PEP. They enforce identity-based access policies immediately after the 802.1X authentication succeeds.
- Dynamic Micro-Segmentation: Robust 802.1X deployments enable dynamic segmentation. Based on the successful authentication, the RADIUS server returns Vendor-Specific Attributes (VSAs) that dynamically:
- Assign the client to a specific VLAN.
- Apply a unique firewall filter/ACL.
- Assign a Security Group Tag (SGT).
This approach ensures that a compromised IoT camera, for example, is automatically isolated to a single micro-segment, minimizing the blast radius of a potential breach across the entire network.
How Cloudi-Fi delivers enterprise Wi-Fi authority
Deploying and maintaining the complexity of WPA2/3-Enterprise, especially the required PKI and RADIUS infrastructure, is often the greatest challenge. Cloudi-Fi simplifies these authoritative requirements by offering a unified, cloud-native platform.
Cloudi-Fi transforms the operational burden into seamless security by providing:
1. Zero-maintenance RADIUS and high availability
- Eliminating On-Premise Servers: Cloudi-Fi provides a fully managed, global cloud-based RADIUS service, eliminating the need for enterprises to deploy, patch, and maintain dedicated primary and secondary physical servers.
- Built-in Load Balancing: The cloud architecture inherently provides load balancing and failover, ensuring that authentication remains continuous and robust, supporting high-density and geographically dispersed environments without configuration overhead.
2. Simplified PKI and certificate lifecycle management
- Automated EAP-TLS Deployment: Cloudi-Fi automates the most complex part of secure Wi-Fi:
- EAP-TLS certificate management. It removes the reliance on cumbersome internal PKI tools (like NDES/SCEP) for client onboarding.
- Seamless Provisioning: It provisions employee and BYOD devices with the required client certificates and Wi-Fi profiles automatically, ensuring mutual authentication without requiring complex end-user configuration or IT intervention.
3. Identity-driven Zero Trust enforcement
- Centralized Policy Engine: Cloudi-Fi acts as the single source of truth for identity. It integrates with existing identity providers (Active Directory, Azure AD, Okta) and sends the necessary Vendor-Specific Attributes (VSAs) to the Access Points.
- Dynamic Micro-Segmentation at Scale: This integration ensures that the moment a user authenticates via 802.1X, they are instantly placed into the correct security segment (VLAN, ACL, SGT) based on their role and device compliance status, serving as the core enabler for Zero Trust access on the wireless network.
By combining the proven security of WPA2/3-Enterprise, robust 802.1X authentication, and Zero Trust principles with Cloudi-Fi’s automation and policy management, organizations can secure their wireless networks efficiently, support modern workforces, and stay ahead of evolving threats.
Conclusion
WPA2/3-Enterprise with 802.1X authentication is more than just a security measure; it is the foundational technology that enables the modern, flexible, and secure enterprise. By adopting this standard, organizations transition from simple password protection to a sophisticated, identity-based security model that is resilient to current threats and ready for future standards like Zero Trust Architecture.
By combining proven security protocols with advanced automation and policy management, enterprises can secure their wireless networks efficiently, support modern workforces, and stay ahead of evolving threats. Secure your enterprise Wi-Fi with confidence—deploy WPA2/3-Enterprise the smart way with Cloudi-Fi.








