Introduction
Every device connecting to a corporate network—laptop, smartphone, IoT sensor—represents a potential attack vector. With remote work, BYOD, and IoT proliferation, perimeter-based security is no longer sufficient. Modern security requires an identity-centric, Zero Trust approach, and IEEE 802.1X enforces it at the network layer.
Initially developed for wired Ethernet, 802.1X now underpins Wi-Fi, VPN, and cloud-based NAC deployments, forming the first line of defense in enterprise networks. This guide provides an authoritative exploration of 802.1X, including core components, packet-level flows, EAPOL frame types, authentication methods, fallback strategies, MDM/UEM deployment, advanced network segmentation, and future trends.
Glossary of key terms
Before diving into the technical details, here are key terms used throughout this guide:
- EAP (Extensible Authentication Protocol): Framework for authentication messages.
- EAPOL (EAP over LAN): Encapsulation of EAP messages in wired/wireless frames.
- RADIUS (Remote Authentication Dial-In User Service): Server that validates credentials and enforces network policies.
- Supplicant: The client device requesting network access.
- Authenticator: Switch or access point that mediates authentication and enforces port control.
- Controlled/Uncontrolled port: Uncontrolled allows only EAPOL; controlled allows full traffic after authentication.
- MAB (MAC Authentication Bypass): Fallback authentication based on MAC addresses.
- dACL (Downloadable Access Control List): Fine-grained policy pushed to the authenticator.
- MDM/UEM (Mobile Device Management/Unified Endpoint Management): Tools for centralized device management and policy enforcement.
What is 802.1X protocol?
802.1X is a standard for port-based Network Access Control (NAC). It defines how endpoints (supplicants) authenticate before being granted access to a network through an authenticator (such as a switch or wireless access point). The authenticator acts as a gatekeeper, controlling whether traffic from the endpoint is forwarded to the broader network.
Instead of relying on static configurations or shared secrets, 802.1X introduces identity-based access control. Authentication requests are relayed to a RADIUS server (the authentication server), which verifies the credentials and returns a policy decision. Based on this, the authenticator either opens the port (granting access) or keeps it blocked.
Key characteristics of 802.1X include:
- Protocol encapsulation: Authentication messages are carried inside EAP over LAN (EAPOL) frames for wired networks and inside 802.11 management frames for wireless.
- Controlled vs. uncontrolled port: Before authentication, the device can only exchange EAPOL packets with the authenticator’s uncontrolled port. Once authentication succeeds, the controlled port is opened for normal network traffic.
- Flexible authentication methods: Supports multiple EAP types (EAP-TLS, PEAP, EAP-TTLS, etc.), allowing both certificate-based and credential-based authentication.
In essence, 802.1X is not just a protocol—it is the foundation of modern secure network access, ensuring that every connection is tied to a verified identity.
Benefits of 802.1X authentication
Deploying 802.1X delivers a wide range of security and operational benefits, making it the gold standard for enterprise access control:
- Strong identity assurance: Ensures that every user or device authenticates uniquely, eliminating the risks of shared passwords or anonymous access.
- Granular policy enforcement: With RADIUS attributes, authenticated sessions can be dynamically assigned to VLANs, ACLs, or role-based policies.
- Improved compliance and visibility: Centralized authentication logs support auditing, incident response, and regulatory reporting.
- Reduced credential risk: Certificate-based EAP-TLS removes the need for passwords, protecting against phishing and credential theft.
- Operational scalability: Scales across wired, wireless, and VPN access without requiring manual port-by-port configuration.
- Alignment with Zero Trust: Functions as the trust anchor, validating identities at the point of network entry and forming the foundation for SASE and ZTNA frameworks.
Key components of 802.1X
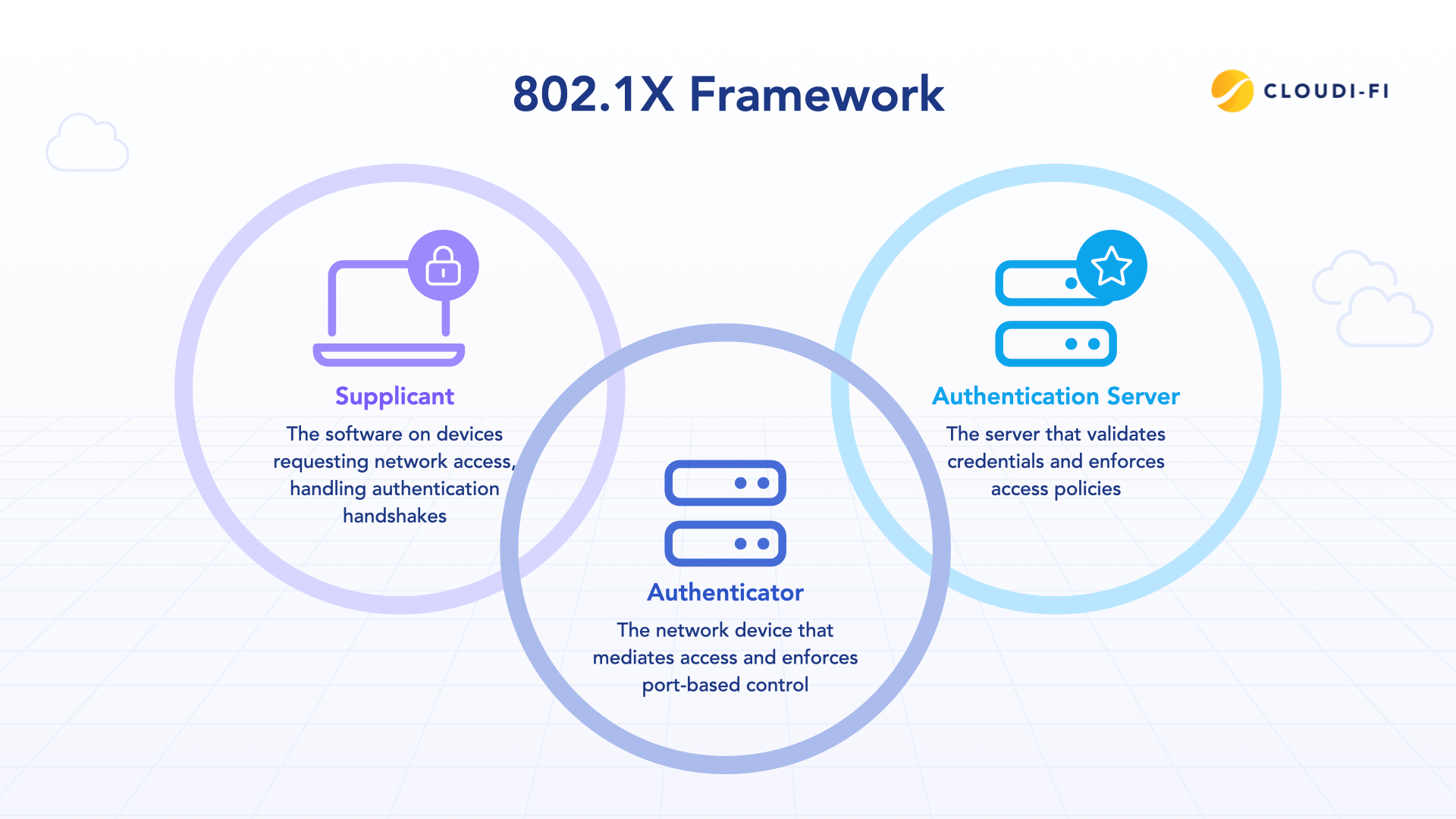
Understanding 802.1X requires familiarity with its three primary components:
Supplicant (the client)
The supplicant is the software running on a device that requests network access. It performs the authentication handshake and ensures the device presents its credentials correctly. Typical examples include:
- Windows, macOS, or Linux built-in clients for standard devices.
- iOS and Android clients for mobile devices.
- Third-party or specialized clients for IoT or legacy systems.
The supplicant is responsible for securely presenting the device identity, often via certificates, to the network.
Authenticator (switch or access point)
The authenticator mediates access to the network and enforces port-based control. Its responsibilities include:
- Maintaining uncontrolled ports that allow only EAPOL traffic until authentication succeeds.
- Transitioning to controlled ports after successful authentication, granting full network access.
- Enforcing dynamic policies, including VLAN assignment and downloadable ACLs (dACLs).
Authentication server (RADIUS)
The RADIUS server validates credentials and enforces access policies. Key details include:
- Core messages: Access-Request, Access-Challenge, Access-Accept, Access-Reject.
- Scalability: RADIUS proxies allow distributed authentication for large or global networks.
- Policy enforcement via attributes: Access-Accept messages may include:
- Tunnel-Private-Group-ID for VLAN assignment
- Filter-Id for downloadable ACLs
- Session-Timeout to limit session duration
- Termination-Action to define end-of-session behavior
This combination of components enables mutual authentication, policy enforcement, and network segmentation.
How 802.1X works
EAP messages are encapsulated in EAPOL frames for wired networks and in 802.11 frames for wireless networks. The authenticator only allows these frames through on its uncontrolled port until authentication is complete.
EAPOL frame types
The protocol defines several frame types to support the full authentication lifecycle:
- EAPOL-Start: Initiates authentication by signaling the supplicant is ready.
- EAPOL-Request/Identity & EAPOL-Response/Identity: Exchanges identity information between the supplicant and the authenticator.
- EAPOL-Key: Used in wireless networks for key derivation and secure traffic encryption.
- EAPOL-Logoff: Allows the supplicant to gracefully terminate a session.
Detailed EAP-TLS flow
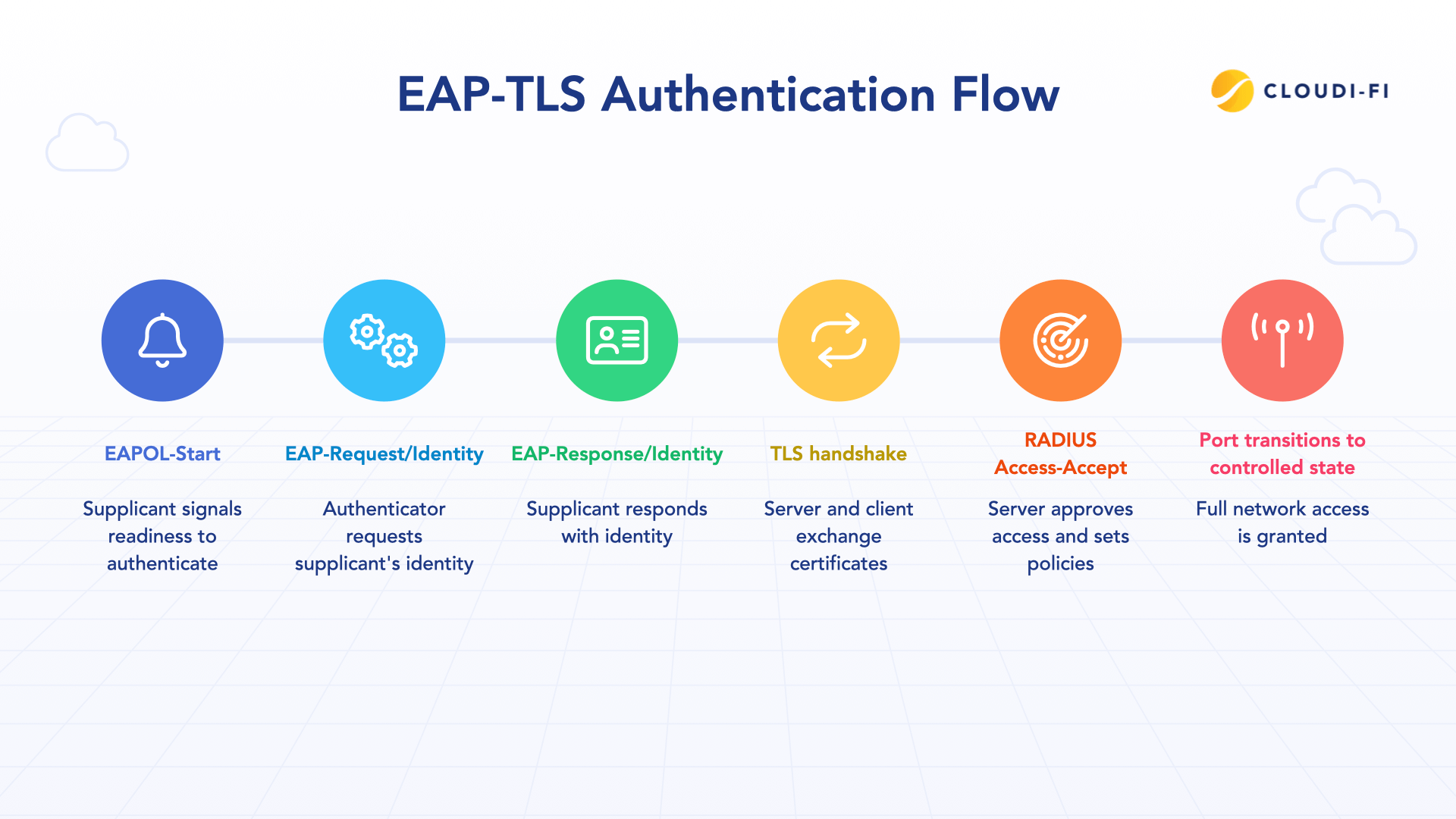
The following steps illustrate a successful EAP-TLS authentication:
- EAPOL-Start: The supplicant signals readiness to authenticate.
- EAP-Request/Identity: The authenticator requests the supplicant’s identity.
- EAP-Response/Identity: The supplicant responds with a username or certificate subject.
- TLS handshake:
- Server sends its certificate; client validates authenticity.
- Client sends its certificate; server validates authenticity.
- A secure TLS tunnel is established.
- RADIUS Access-Accept: The server approves access and may include VLAN assignment, dACLs, session timeout, or termination actions.
- Port transitions to controlled state: Full network access is granted according to policy.
This flow demonstrates how 802.1X enforces secure, identity-based authentication and policy-driven network access.
802.1X authentication methods
Different EAP methods provide varying levels of security and deployment complexity:
- EAP-TLS: Uses mutual certificate-based authentication, eliminating passwords and providing strong security. Best for fully managed devices in Zero Trust environments.
- PEAP: Encapsulates password-based authentication in TLS. Easier to deploy, but susceptible to rogue AP attacks if not properly configured.
- EAP-TTLS: Offers flexible inner authentication methods within a secure tunnel. Useful for mixed device environments.
Comparative analysis and fallback methods
While 802.1X is the strongest NAC method, other mechanisms exist for legacy or special-case devices. A contextual overview helps understand trade-offs:
- 802.1X: Identity-based NAC providing strong security, VLAN/dACL enforcement, and Zero Trust alignment. Complexity arises from PKI management.
- MAC Authentication Bypass (MAB): Authenticates devices via MAC addresses. Useful for IoT or legacy devices, but easily spoofed and insecure for user-facing endpoints.
- Port Security: Limits the number of MAC addresses per port. Simple and foundational, but lacks dynamic, identity-based policy enforcement.
Legacy device & IoT onboarding
Even in modern networks, some devices cannot support 802.1X, typically very old or specialized components. Enterprises often combine 802.1X for managed devices with fallback methods for these exceptions:
- Corporate laptops and managed devices → 802.1X: Fully identity-based authentication using certificates.
- Printers and IoT devices → MAC Authentication Bypass (MAB) + dedicated VLANs: Provides basic access while isolating them from sensitive systems.
- Guest devices → Captive portal or temporary VLANs: Controlled internet access without exposing internal resources.
This hybrid strategy ensures comprehensive network coverage while maintaining security boundaries for endpoints that cannot natively perform 802.1X authentication.
MAC addresses and 802.1X
MAC addresses are fundamental components of the 802.1X authentication process. Every network interface has a unique MAC address that the authenticator uses to identify the device attempting to connect. During the initial EAPOL exchange, the authenticator logs the MAC address of the supplicant, which serves multiple purposes:
- Device identification: Helps the network distinguish each endpoint, even before authentication succeeds.
- Fallback authentication: In cases where devices cannot support 802.1X (legacy or IoT), the MAC address can be used for MAB, allowing basic network access while maintaining isolation.
- Policy correlation: RADIUS servers can correlate MAC addresses with previously known devices, facilitating dynamic VLAN assignment or applying device-specific access policies.
MAC addresses act as the first layer of identity verification, enabling both the standard 802.1X flow and fallback mechanisms.
Role of MDM/UEM in 802.1X deployment
Deploying 802.1X at scale is challenging without centralized device management. MDM/UEM platforms solve this by automating onboarding, certificate provisioning, and policy enforcement:
Automated onboarding
Manual configuration of 802.1X profiles on hundreds or thousands of devices is unfeasible. MDM solutions like Microsoft Intune, Jamf, or VMware Workspace ONE automate this process, pushing profiles to all managed devices.
Certificate provisioning
MDM integrates with Certificate Authority connectors (NDES/SCEP) to automatically request, install, and manage client certificates, removing the PKI management bottleneck for EAP-TLS deployment.
Policy enforcement
MDM can verify device compliance before network access:
- Device encryption status
- Antivirus or endpoint protection
- OS version or patch level
Non-compliant devices can be blocked from receiving the 802.1X profile, ensuring security before connection.
Advanced network segmentation
802.1X not only authenticates devices—it also enforces fine-grained network policies. Dynamic segmentation ensures that each device only accesses the resources it’s authorized for:
- Dynamic VLAN Assignment: Devices are automatically placed into VLANs based on identity. For example, a Marketing employee authenticates via EAP-TLS and is assigned to Marketing-VLAN, while an office printer using MAB goes to Printers-VLAN, preventing them from communicating with each other.
- Downloadable ACLs (dACLs): Even within a VLAN, access can be restricted at the port level. For instance, a guest in the Guest VLAN can only access the captive portal and internet, while corporate devices can access internal applications.
- Continuous Authentication: Modern systems periodically re-authenticate devices to ensure compliance and maintain trust throughout the session.
These capabilities implement microsegmentation and enforce least-privilege access, reducing lateral movement and enhancing security across the network.
IEEE standard for 802.1X
The IEEE 802.1X standard defines a framework for port-based network access control, providing a formal structure for authenticating users and devices on both wired and wireless networks. By combining the controlled/uncontrolled port mechanism with EAP authentication, the standard ensures that only authorized devices can transmit normal network traffic.
Key aspects of the IEEE 802.1X standard include:
- Port-based access control: The switch or access point maintains an uncontrolled port for initial EAP messages and a controlled port that opens only after successful authentication.
- Flexible EAP methods: Supports multiple EAP types (certificate-based or credential-based) to adapt to different security requirements.
- Policy enforcement: Integrates with RADIUS to apply VLAN assignments, ACLs, session timeouts, and other network policies per authenticated device.
- Cross-network security: Ensures that the same authentication model works consistently for both wired and wireless environments, creating a unified security posture.
The IEEE standard provides the technical foundation for secure, identity-driven access, enabling enterprises to enforce consistent security policies across diverse network infrastructures.
Integration with broader security frameworks
802.1X as the trust anchor
802.1X serves as the initial trust assessment, verifying device identity before granting network access. It underpins:
- SASE (Secure Access Service Edge): Ensures only authenticated endpoints reach cloud resources.
- ZTNA (Zero Trust Network Access): Provides continuous, application-level policy enforcement.
Micro-segmentation and threat containment
Dynamic VLANs and dACLs prevent lateral movement and restrict access to authorized resources, which is essential for Zero Trust and regulatory compliance.
The future of 802.1X
Looking forward, 802.1X continues to evolve:
- Passwordless authentication: EAP-TLS enables truly passwordless access, supporting Zero Trust and identity-first security.
- AI-driven security: Identity and policy data from 802.1X can feed SIEM and SOAR platforms, enabling anomaly detection (e.g., IoT device attempting unauthorized access).
- Cloud-native architectures: Cloud-hosted NAC integrates with identity providers (Azure AD, Okta) and SASE/ZTNA frameworks for global, scalable, simplified management.
Conclusion
802.1X is more than a protocol; it is a foundational, identity-driven framework for modern network security. By combining edge authentication, dynamic policies, MDM/UEM automation, and micro-segmentation, it establishes a trust anchor for Zero Trust, SASE, and ZTNA architectures.
Cloud-aware solutions like Cloudi-Fi enhance deployment by providing:
- Cloud-hosted RADIUS/NAC for global scalability
- Automated certificate lifecycle management
- Secure onboarding for BYOD and IoT
- Dynamic VLANs and downloadable ACLs for micro-segmentation
Together, these capabilities deliver secure, compliant, and future-ready network access for modern enterprises.








