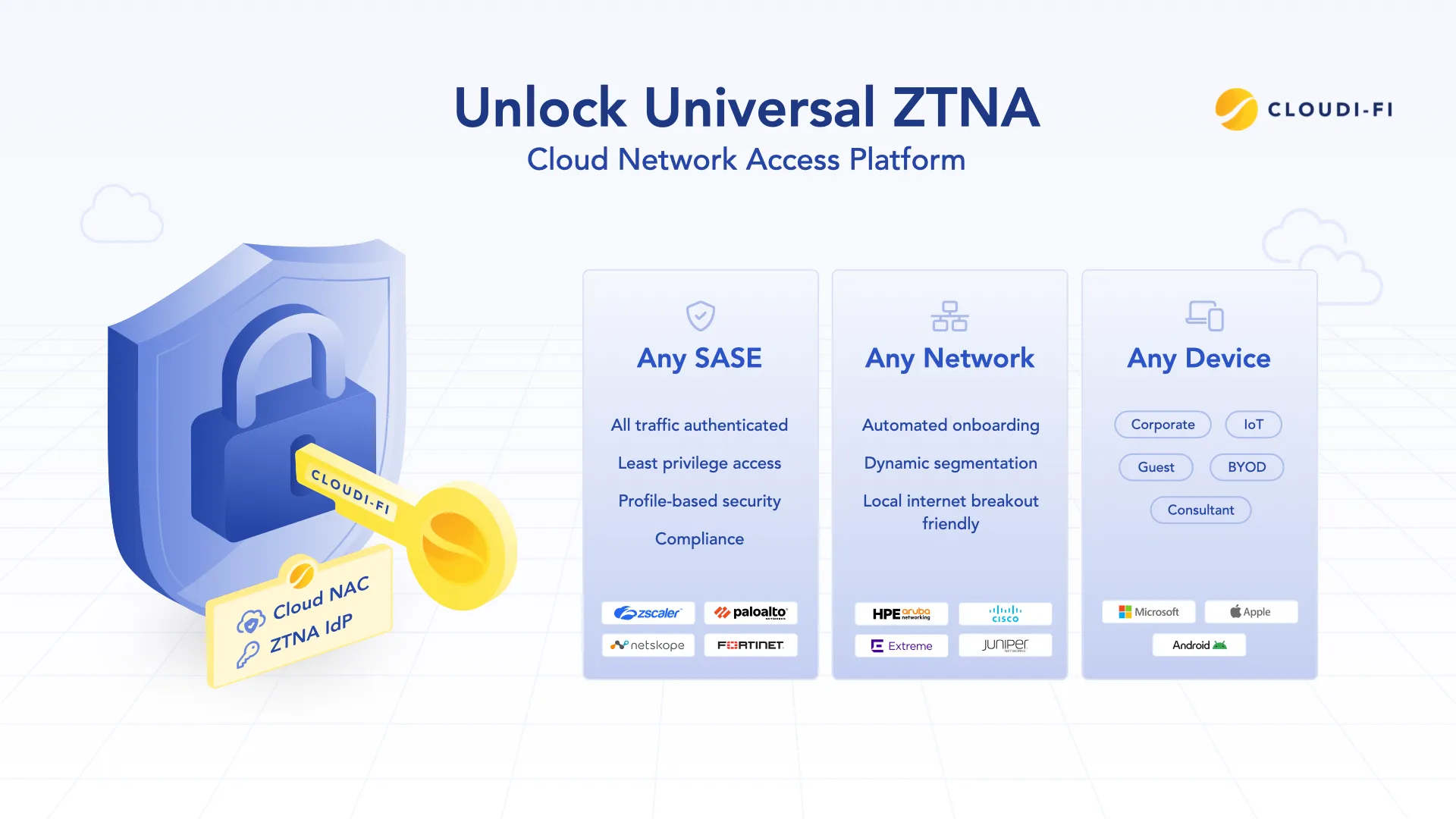
Evolving from traditional ZTNA to Universal ZTNA
There’s a lot of hype around Zero Trust Network Access (ZTNA*) right now, so to ground the discussion, we’ll start by clearly defining what Universal ZTNA** is, beginning with a comparison to traditional ZTNA, followed by a quick overview of its key components.
What are the foundations of Universal ZTNA?
- Identity-based access: Access decisions are driven by verified user identity and contextual factors (device posture, location, time), rather than relying on traditional network location.
- Least privilege: Users are granted only the least privileges required to perform their tasks, reducing the attack surface and limiting lateral movement.
- Continuous verification: Access is continuously re-evaluated based on user behavior, device health, and context, ensuring that trust is never static.
- Visibility and control: Universal ZTNA provides granular visibility into user activity and resource access, enabling stronger security posture, real-time analytics, and better incident response.
- Cloud-native and simplified management: As a cloud-native solution, Universal ZTNA delivers centralized policy management, automatic updates, and elastic scalability—removing the need for local appliances and making cloud-first security the new standard.
Why traditional network access fails and how ZTNA solves it
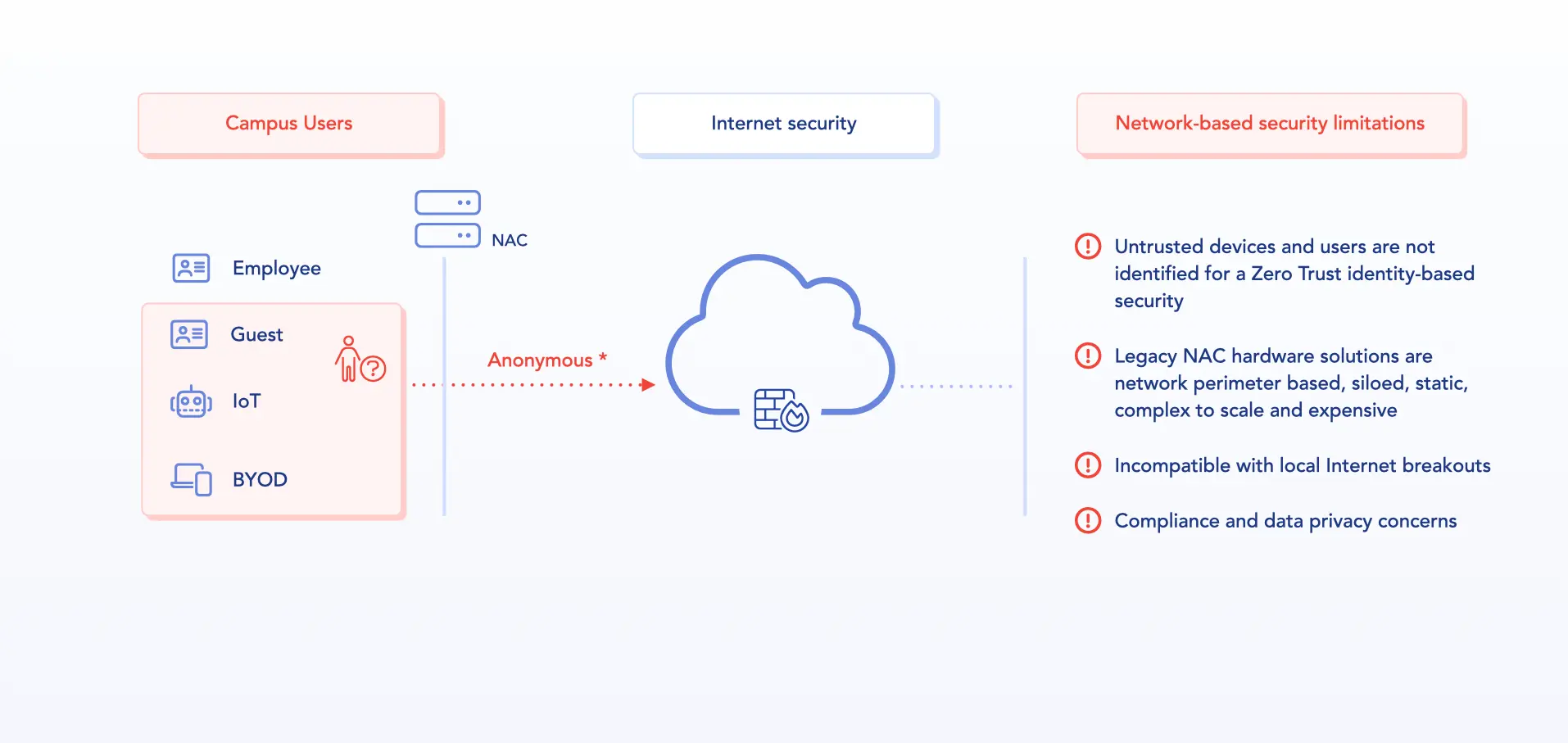
Cloud adoption, hybrid work, and the rise of a mix of managed and unmanaged devices have redefined the enterprise network. Employees, BYOD, guests, contractors, and IoT now access resources from anywhere, on any device, expanding both connectivity and security risks.
To adapt, many organizations moved away from legacy solutions such as hardware-based NAC and firewalls, which granted broad, implicit network access based on network location. But those access models no longer align with modern realities. They are siloed, resource-intensive, and fundamentally built on outdated assumptions: that networks can be trusted, and users can be segmented by location. Here are some key limitations of legacy models:
- Performance bottlenecks degrade user experience and rely on implicit trust in the corporate network.
- Dependence on on-prem appliances, requiring heavy maintenance, lacking scalability and facing growing obsolescence.
- Compliance demands more granular access control, full auditability, and region-specific data governance, which legacy models struggle to support.
- Workforces are increasingly distributed, with a mix of managed, unmanaged, BYOD, and third-party devices, rendering perimeter-based security models obsolete.
Zero Trust Network Access (ZTNA) emerged as a more secure alternative, moving away from network-based trust and enforcing application-level access based on identity and context. This marked a significant step forward: access is no longer tied to network location, but to verified user identity and device posture. It introduced modern Zero Trust foundations that transformed enterprise security:
- Identity-based access: Policies verify user identity and device context (posture, location, time) rather than network location.
- Least privilege: Users receive only the access necessary to perform their tasks, minimizing the attack surface.
- Continuous verification: Trust is dynamically reassessed based on behavior, device health, and context.
- Visibility and control: Provides granular insight into user activity and resource access, enabling stronger analytics and response.
- Cloud-native management: Centralized policies, automated updates, and elastic scalability—removing the need for local appliances.
However, this progress only solved part of the problem.
The agentless gap: Why standard ZTNA doesn’t cover all devices
ZTNA proves highly effective when applied to corporate-managed and agent-equipped devices. It enables control, posture verification, and context-aware policies; all pillars of a mature Zero Trust strategy. However, this model breaks down when extended to the real-world diversity of devices that enterprises must support.
As Gartner notes, the true challenge lies in extending this robust security model to encompass all devices and users, achieving what is known as "Universal ZTNA." This extension is critical because modern enterprise environments are characterized by a diverse ecosystem of agentless devices, including employee personal devices (BYOD), IoT, and third-party devices (contractors, guests, etc.). These devices are often unmanaged, with no agent, no MDM, and limited visibility, each introducing unique security considerations and potential vulnerabilities.
Successfully implementing universal ZTNA requires overcoming several hurdles, such as:
- Device diversity and management: Managing and securing an ever-growing array of device types, many of which are unmanaged or difficult to control centrally.
- Legacy infrastructure integration: Integrating ZTNA solutions with existing, often complex, legacy network infrastructures that were not designed with Zero Trust principles in mind.
- User variety and access needs: Catering to the varied access requirements of different user groups, from internal employees to external partners, without compromising security or user experience.
- Policy enforcement and granularity: Developing and enforcing highly granular access policies that adapt dynamically based on user identity, device posture, location, and application context.
While the promise of Universal ZTNA is compelling, implementing it is far from straightforward, especially when applied to legacy environments.
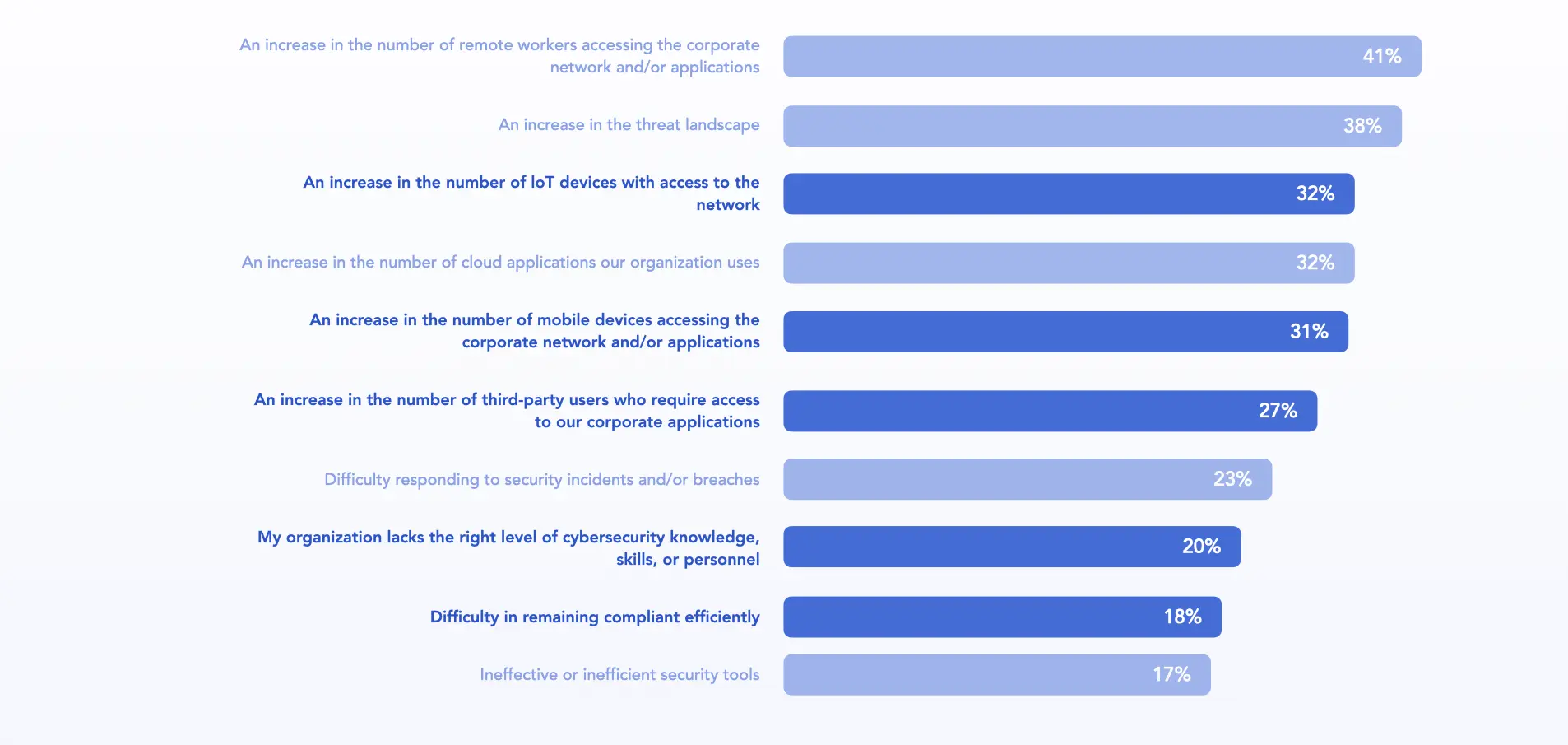
According to research from TechTarget’s Enterprise Strategy Group (ESG), 59% of organizations say cybersecurity has become more difficult in the past two years, driven by factors such as the rising number of IoT devices (32%), the continued surge in mobile devices accessing resources (31%), and the increasing number of third-party users requiring access to corporate applications. These technical challenges are compounded by organizational gaps, including a widespread shortage of cybersecurity knowledge, skills, and qualified personnel.
These risks, both technical and organizational, collide with the reality of legacy infrastructures. Most enterprises cannot start from a blank slate. They operate within complex, layered infrastructures built over years, often decades, around traditional security models. Attempting to retrofit Zero Trust principles into these environments reveals deep operational and architectural challenges.
Integrating Universal ZTNA without disrupting legacy infrastructure
Universal ZTNA isn’t about ripping and replacing existing security, it’s about unifying it. Enterprises have invested years in NAC, firewalls, and tightly coupled infrastructure; discarding these is neither practical nor cost-effective. The real power of Universal ZTNA lies in integrating Zero Trust principles with existing controls, creating a seamless, end-to-end access framework.
While ZTNA introduces a more innovative model, replacing traditional controls like NAC or firewalls is rarely feasible. A full re-engineering to Zero Trust often demands extra network appliances and struggles to completely replace existing solutions. This is due to several key challenges:
- Infrastructure overlap and redundancy: A full ZTNA implementation may duplicate some NAC or firewall functions but lack others, such as network-level posture enforcement or device onboarding, making full replacement impractical. If not managed carefully, this can lead to redundant infrastructure, increased operational overhead, and a convoluted security posture. Organizations may be hesitant to invest in new solutions that seem to duplicate existing capabilities, especially when the return on investment for a complete overhaul is not immediately clear.
- Interoperability with legacy systems: Many on-prem applications, protocols, and devices were not built for Zero Trust. Retrofitting ZTNA into these environments introduces complexity and risk.
- Resource constraints and skill gaps: Building and operating a complete Zero Trust architecture requires specialized expertise in identity, policy, and cloud-native security, which many organizations lack. The cost and time associated with training existing staff or hiring new specialists can be prohibitive.
- Vendor lock-in and ecosystem challenges: Enterprises have significant investments in their existing firewalls or NAC ecosystems. Shifting to a new ZTNA provider may require abandoning these investments or managing complex multi-vendor integrations. Some vendors promote proprietary edge connectors to extend Zero Trust to the network edge, but integrating them into heterogeneous legacy systems often introduces operational complexity and reduces architectural flexibility.
These challenges underscore why a phased and hybrid approach to ZTNA adoption is often necessary, rather than an immediate and complete architectural overhaul. Enterprises typically seek solutions that can gradually integrate with their existing infrastructure, providing incremental improvements in Zero Trust security posture without necessitating a wholesale replacement of critical legacy systems.
NIST SP 800‑207 defines Policy Enforcement Points (PEPs) as the mechanisms that enforce access decisions, which can include NAC, firewalls and segmentation. The companion SP 1800‑35 guide further illustrates that Zero Trust architectures succeed by integrating these network-level PEPs with centralized identity and policy systems, ensuring seamless coordination between cloud-delivered and on-premises security controls rather than replacing existing infrastructure.
This shift calls for solutions that bridge the gap between network-based access control and ZTNA, adding identity and context to the network layer, enabling posture-based access for unmanaged or agentless devices, and reducing reliance on legacy trust assumptions.
Why NAC is essential for Zero Trust Network Access to become Universal
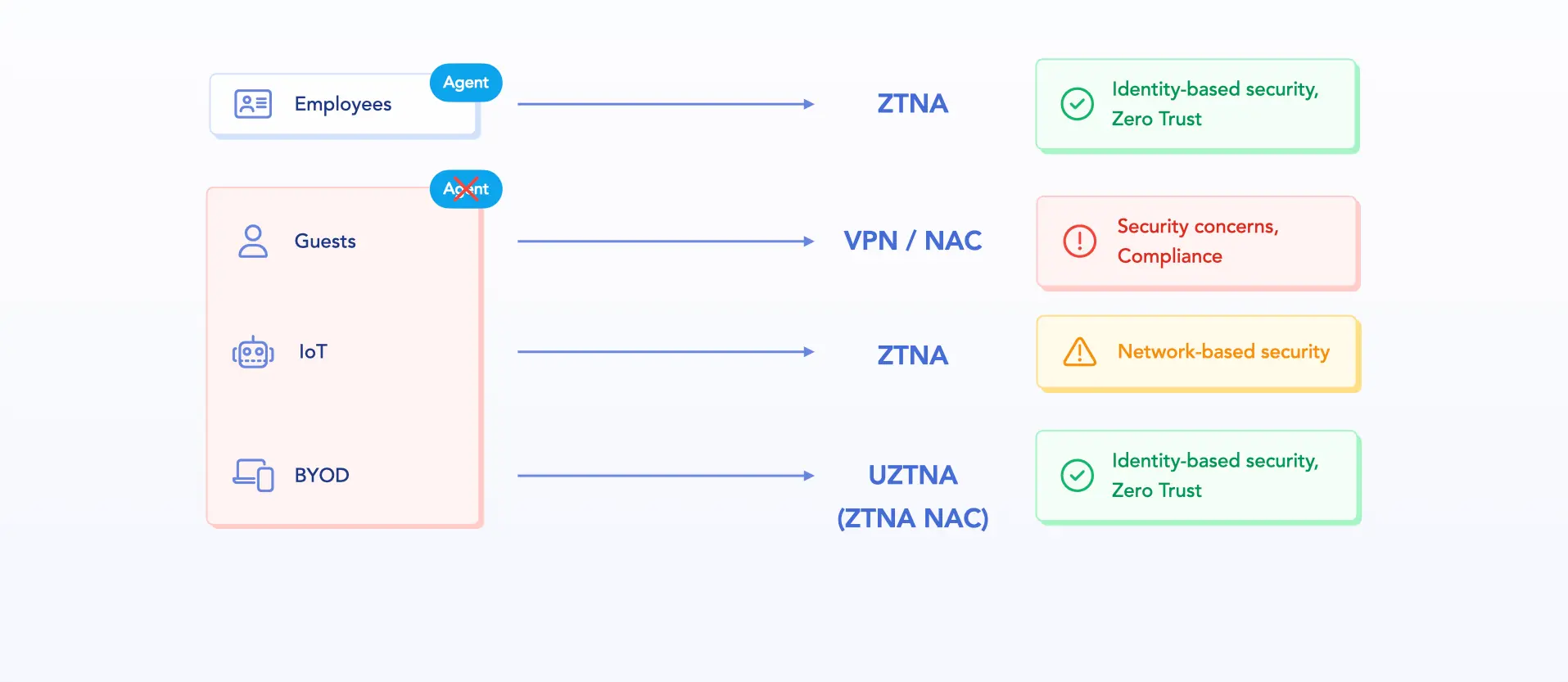
Zero Trust Network Access (ZTNA) enforces strong application-level controls based on user identity and context. But in many implementations, the network layer remains implicitly trusted once access is granted. This undermines the core Zero Trust principle: "never trust, always verify".
Most ZTNA solutions were largely designed to secure remote and on-site users, primarily through agents installed on managed or semi-trusted devices. As a result, organizations remain exposed to risks from unmanaged BYOD, guest, or IoT/OT devices that gain network visibility before Zero Trust policies are enforced, creating blind spots and opportunities for lateral movement.
To close this gap, some vendors introduced edge appliances and local enforcement points to push policy closer to users and enable micro-segmentation within branch networks. While this can help in simple environments, these solutions rarely scale to complex, distributed enterprise infrastructures.
In particular, most of these edge solutions and appliances act more like add-ons than fully integrated security controls and lack key network-layer capabilities:
- 802.1X authentication
- MAC filtering and device fingerprinting
- Firewall rules based on real-time posture
- Pre-connect policy enforcement
These limitations underscore a broader issue: ZTNA enforcement is incomplete and leaves gaps for security breaches, while fulfilling its promise requires global coverage. This is where NAC (Network Access Control) plays a critical role. Rather than being replaced, NAC complements ZTNA.
According to NIST SP 800‑207 and its companion SP 1800‑35 guide, Universal ZTNA works by integrating NAC and other network-level enforcement tools into a centralized Zero Trust policy framework—coordinating cloud and on‑prem components rather than disrupting existing infrastructure.
By enforcing identity-based access and segmentation when a device connects to the network, whether or not it runs an agent. NAC acts as the first line of Zero Trust enforcement and provides:
- Authentication of users and devices at the point of connection, with or without an agent
- Dynamic access policies based on identity, role, posture, or device type
- Microsegmentation through VLAN assignment or ACLs before any communication occurs, to block lateral movement from the start
- Visibility and control across all device types: corporate, guest, unmanaged, BYOD, or IoT
Think of it like airport security:
ZTNA is the boarding gate, checking whether you’re allowed onto a specific flight (application). NAC is the airport entrance security checkpoint, where ID is checked, bags are scanned, and anyone who is unauthorized is stopped before even reaching the gate.
By enforcing security at the first connection point, NAC closes a fundamental gap: ensuring no device is implicitly trusted, and no traffic flows unchecked before ZTNA takes over. This foundational layer allows ZTNA to become truly Universal, extending Zero Trust from the cloud down to the network edge.
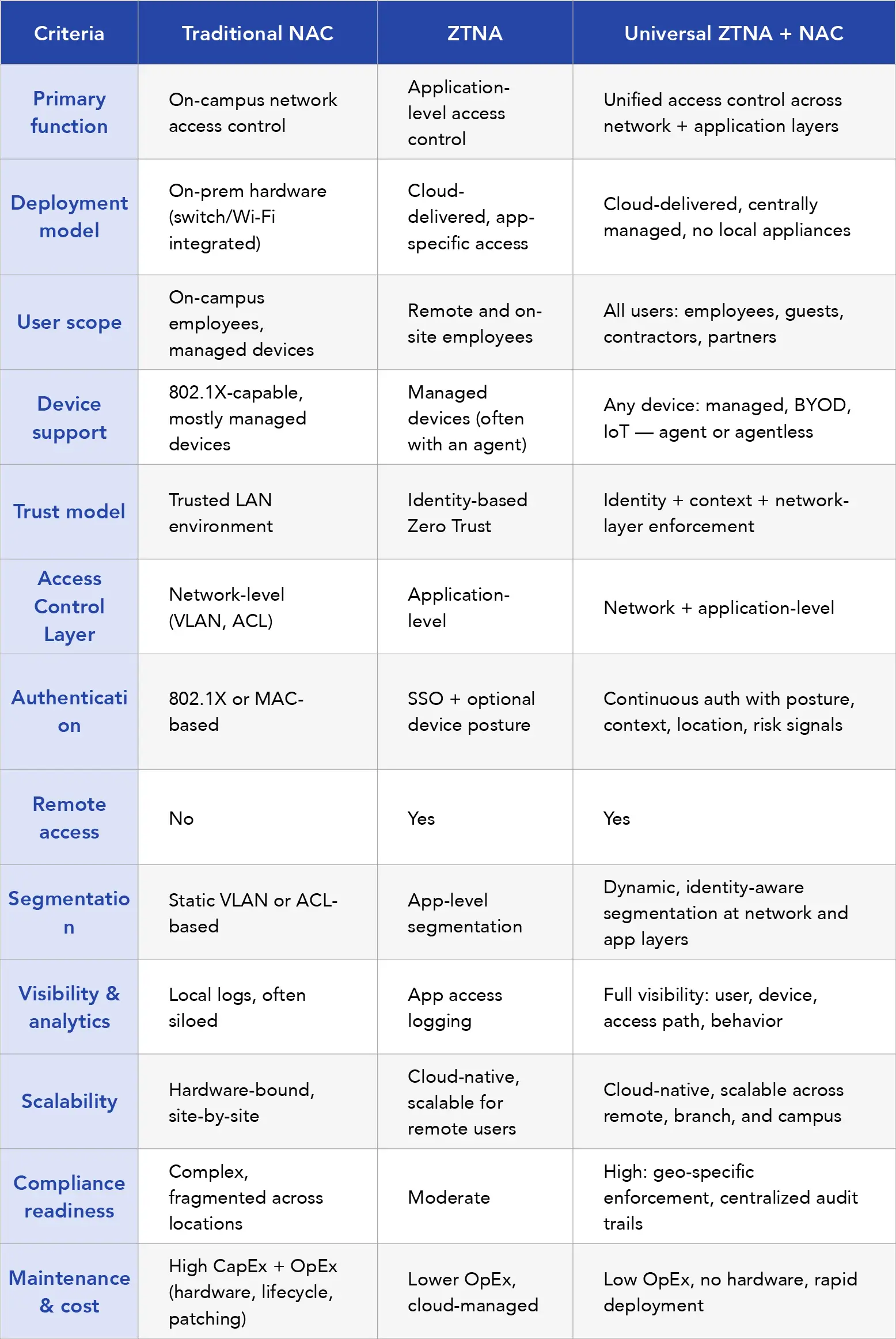
Universal ZTNA in practice: Real-world use cases
The value of Universal ZTNA becomes clear when applied to real-world environments. While traditional ZTNA primarily focuses on securing remote user access to specific applications or resources, often as a VPN replacement, it was designed to complement SSE, and its scope is limited.
Universal ZTNA broadens this approach by securing all users (authenticated and unauthenticated), all devices (managed and unmanaged), and all locations, ensuring a consistent security posture across both on-premises and off-premises environments.
By combining ZTNA with NAC-like capabilities, Universal ZTNA enables context-aware, scalable, and hardware-free access control, reducing reliance on legacy appliances and manual processes. Below are key scenarios with different use cases that Universal ZTNA addresses :
Guest and BYOD access
Enforce secure, identity-based access for guest users and personal devices without relying on VPN or legacy captive portals.
What it enables:
- Agentless onboarding via NAC with identity-based posture checks
- Application-layer restrictions via ZTNA
- No need for IT ticketing or manual provisioning
Real-world examples:
- A visiting partner needs secure, compliant internet access during an on-site meeting without VPN or IT tickets.
- A contractor from a finance company accesses a bank’s environment from their own unmanaged laptop, NAC applies posture checks ensuring the device is allowed to connect to the network, and ZTNA limits access to approved apps.
- Employees use personal smartphones to access corporate apps without compromising network security.
- A retail customer connecting to in-store Wi-Fi Internet access to receive personalized promotions and a shopping experience, while being assured of security and compliance
IoT and OT device onboarding
Secure devices that lack traditional user identities (such as printers, sensors, or industrial equipment) by using NAC for network-layer enforcement and traffic isolation with ZTNA for exposure limitation.
What it enables:
- Network-based segmentation for non-agent devices
- Granular controls without relying on MAC address whitelisting
- Reduced manual workload
Real-world use case example:
- A global luxury retailer brand operating 1,000+ stores worldwide replaces manual MAC filtering across 15,000+ IoT devices with dynamic posture-based controls, saving time, reducing errors, and scaling operations without on-site IT.
Branch office security without local appliances
Apply centralized Zero Trust policies across distributed sites without deploying on-prem firewalls or NAC appliances.
What it enables:
- Centralized access policy management via cloud-native controls
- Local enforcement through NAC
- Elimination of hardware lifecycle and refresh costs
Real-world use case example:
- A Global Food Manufacturer running 16 on-premise NAC appliances for 802.1x authentication across its global sites, facing its NAC infrastructure limitations that needed to be regularly maintained and refreshed without guarantees on upcoming features or predictability of associated costs.
Global compliance and local enforcement
Enforce country-specific access policies, content filtering, and data sovereignty rules, even with local internet breakout.
What it enables:
- Identity-aware ZTNA and policy enforcement at the edge via NAC
- Adaptability to regional data privacy laws and compliance frameworks
- Centralized visibility with local enforcement
Real-world use case example:
- A large company transitioning from 3 regional internet access to local internet breakouts across its global sites, and facing compliance challenges as each country imposes different regulations and data privacy laws.
Extending Zero Trust to the network access layer with NAC does more than just closing a security gap, it unlocks a unified approach to managing identity, access, and compliance across every environment. By combining NAC with ZTNA, organizations move from fragmented controls to a cohesive, scalable model that adapts to any user, device, or location. But this shift isn’t only about solving technical limitations. It’s also about meeting new organizational demands: agility, compliance, cost reduction, and operational scale.
How Universal ZTNA builds a strategic foundation for enterprise security
Enterprises today face a reality where access is everywhere, across users, devices, locations, and clouds. Traditional security models can’t keep up. Even standard ZTNA falls short when faced with unmanaged devices, complex compliance needs, or campus environments.
Universal ZTNA addresses this gap by combining the contextual intelligence of ZTNA with the network-layer control of NAC. It delivers secure, identity-aware access at both the application and network layers, across all environments, all devices, and all users, with or without agents.
At Cloudi-Fi, we believe security should enable business, not slow it down. That’s why we’ve built a platform designed to integrate, not disrupt, existing infrastructure, and scale with the realities of global enterprise networks. This isn’t about replacing legacy tools. It’s about adapting security to the speed of business: making it more agile, compliant, and resilient.
Definition index:
- *Traditional ZTNA:
Primarily designed to replace VPNs, traditional ZTNA secures remote access to specific applications or resources. It focuses on managed users and devices and was originally built to complement SSE (Security Service Edge).
- **Universal ZTNA:
Extends the ZTNA model to encompass all user types (authenticated, unauthenticated), device profiles (managed, unmanaged, IoT/OT), and access locations (on-premises or remote). It delivers consistent policy enforcement and posture validation across the entire enterprise environment.