Introduction to Zero Trust Security (ZTS)
The Zero Trust Security (ZTS) framework is founded on the principle of "Never Trust, Always Verify." Unlike traditional perimeter-based security models, which assume that internal network traffic can be trusted, ZTS challenges this notion by treating all network interactions as potential threats, regardless of origin. This paradigm shift emphasizes the importance of continuous trust validation, ensuring robust security measures are always in place. ZTS has become critical for wireless networks, where the dynamic nature of connections and the diversity of devices amplify security challenges. The increasing adoption of wireless technologies necessitates proactive measures to mitigate risks and secure sensitive information.
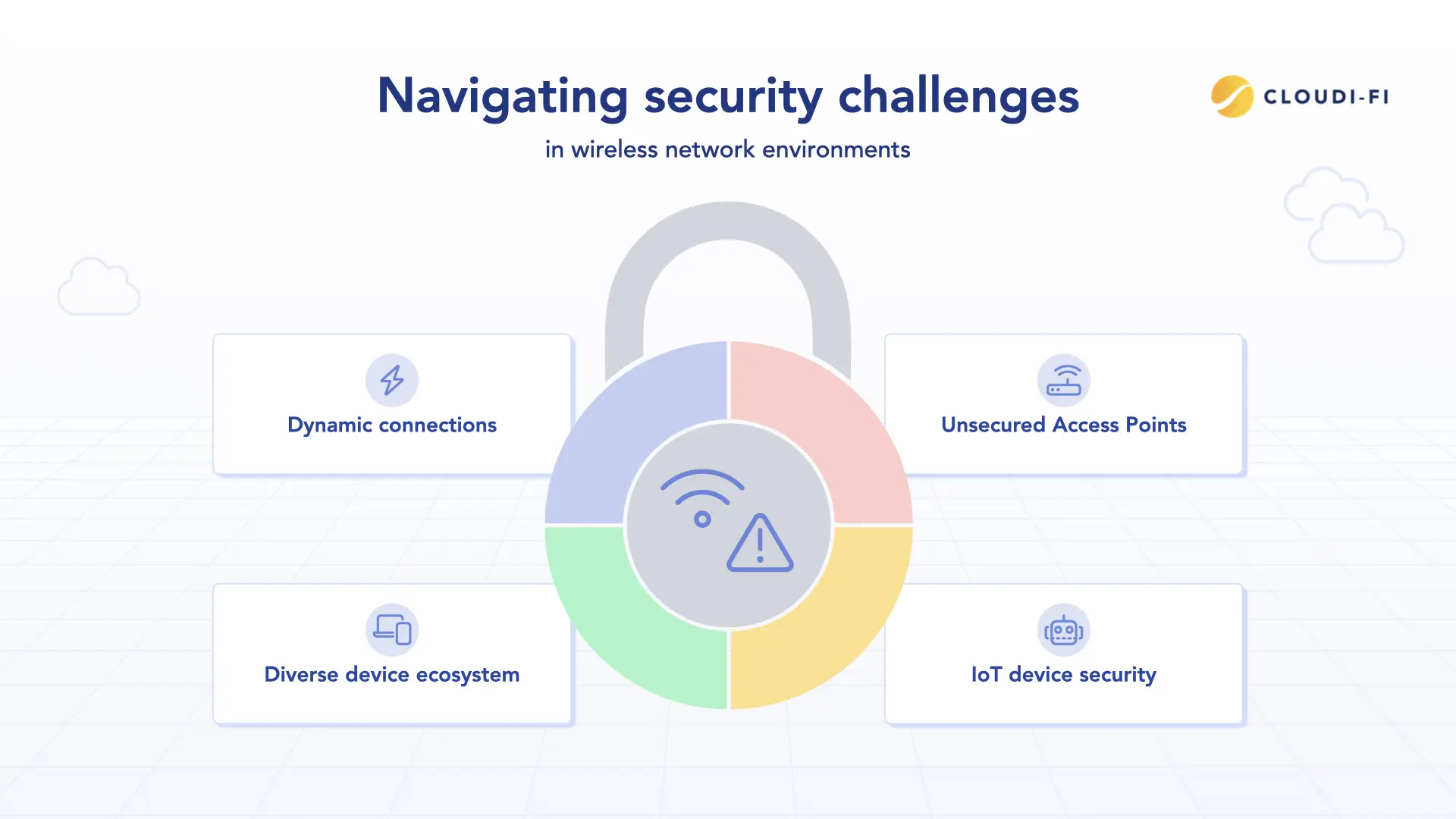
Understanding the risks of wireless networks
Wireless networks present unique vulnerabilities, including:
- Unsecured access points: Public Wi-Fi and poorly configured networks increase exposure to man-in-the-middle (MITM) attacks, rogue access points, and packet sniffing.
- IoT devices: Many IoT devices lack robust security features, creating potential entry points for attackers who exploit weak default credentials or outdated firmware.
- Diverse device ecosystem: The wide range of devices accessing networks, including BYOD (Bring Your Own Device), complicates security management and increases the attack surface.
- Dynamic connections: Devices' frequent connection and disconnection make it difficult to maintain consistent security postures across the network.
5 actionable steps to implement Zero Trust Security (ZTS)
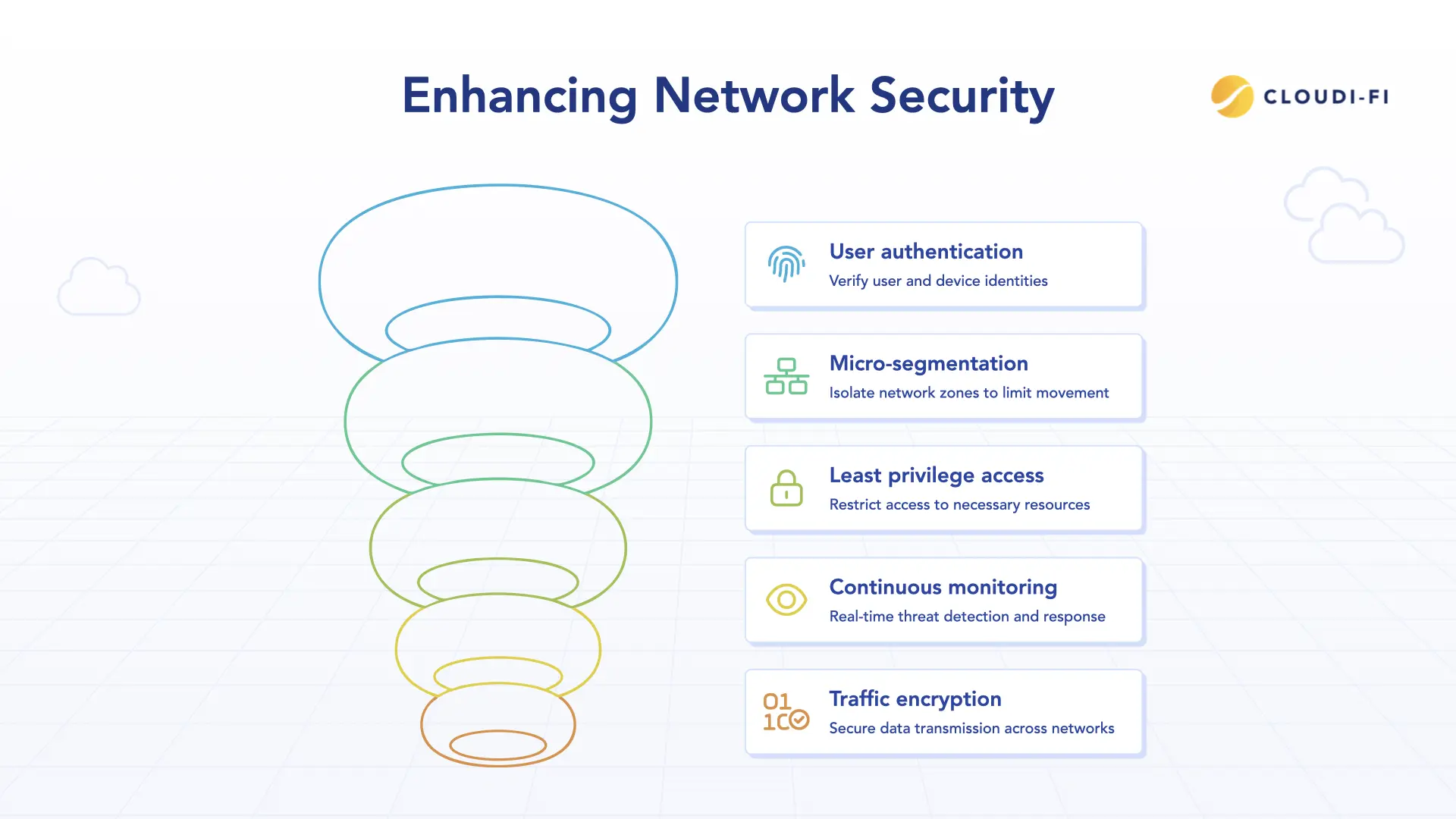
Step 1: Identity verification
Ensure every user and device is authenticated before accessing network resources. Implement Multi-Factor Authentication (MFA), biometric verification, and contextual data analysis, such as device type and location, to strengthen security. Leverage identity providers like Okta or Azure AD to integrate MFA seamlessly with existing systems. Enforce conditional access policies to adapt authentication requirements based on risk factors and real-time context.
Step 2: Microsegmentation
Segment the network into isolated zones to limit lateral movement and enhance security. Utilize VLANs and software-defined networking (SDN) to create granular segments tailored to specific roles or device types, such as guest, BYOD, and IoT. Enforce access policies through firewalls and SDN controllers, ensuring strict traffic control. Implement dynamic segmentation that adapts in real-time based on device behavior and risk scores.
Step 3: Least privilege access controls
Restrict access to only the necessary resources for each user or device based on their function. Implement role-based access controls to minimize permissions and reduce security risks. In wireless networks, ensure IoT devices communicate only with designated servers, preventing unauthorized interactions. Regularly audit access controls to adapt to evolving security requirements.
Step 4: Continuous monitoring and threat detection
Continuously monitor network activities in real-time to detect and mitigate potential threats. Leverage AI-driven threat detection systems and Network Intrusion Detection Systems (NIDS) for enhanced security. Utilize advanced log analysis and anomaly detection tools such as Splunk or Elastic Security for proactive threat identification. Implement automated incident response protocols to ensure rapid and effective threat mitigation.
Step 5: Encryption of network traffic
Encrypt all wireless communications to protect data. Use WPA3 for Wi-Fi encryption and apply end-to-end encryption for application data. Ensure all devices support WPA3 and configure wireless access points accordingly. Implement TLS for secure web traffic and regularly update encryption protocols to address emerging vulnerabilities.
Enhanced ZTS with Cloudi-Fi: Securing your wireless network
Cloudi-Fi significantly enhances Zero Trust Security (ZTS) by providing cloud-based solutions that ensure robust security and management for wireless networks. As organizations face increasing complexities with IoT devices, BYOD policies, and dynamic network environments, Cloudi-Fi offers tools that align perfectly with the principles of ZTS, ensuring continuous, real-time monitoring, secure access, and seamless device onboarding.
Cloud captive portal: A secure, scalable solution for device authentication
A captive portal is a web page that requires users to authenticate before granting access to a network. In public spaces like cafes, hotels, and airports, captive portals are essential for managing untrusted devices and ensuring secure internet access. Cloudi-Fi’s Cloud-based Captive Portal goes beyond traditional solutions, offering a range of advanced features:
How does a cloud-based captive portal work?
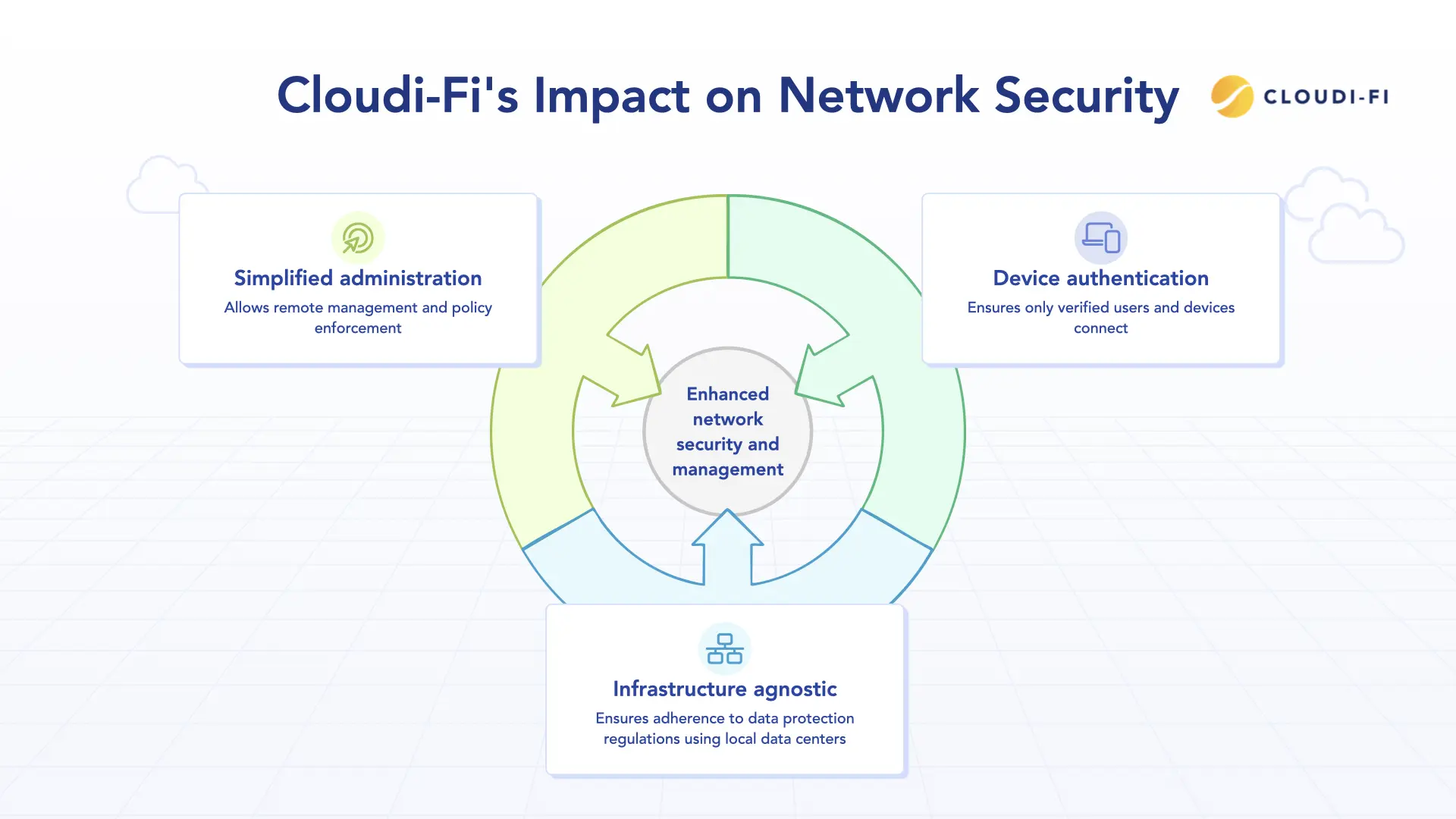
- Authentication across device types: Cloudi-Fi's Captive Portal authenticates devices such as guests, employees, BYOD, and IoT devices, ensuring that only verified users and devices can connect to the network. This is done without requiring additional on-premises hardware, streamlining the process and reducing complexity.
- Infrastructure agnostic: The cloud-based solution operates independently of on-site hardware, offering centralized deployment and management that can scale across multiple locations, making it easier for organizations to manage remote teams or global operations.
- Simplified administration: Cloud-based portals allow seamless remote network management. Through a centralized dashboard, administrators can enforce security policies, configure user access, and monitor network traffic in real time.
Benefits of Cloudi-Fi’s Cloud Captive Portal for ZTS
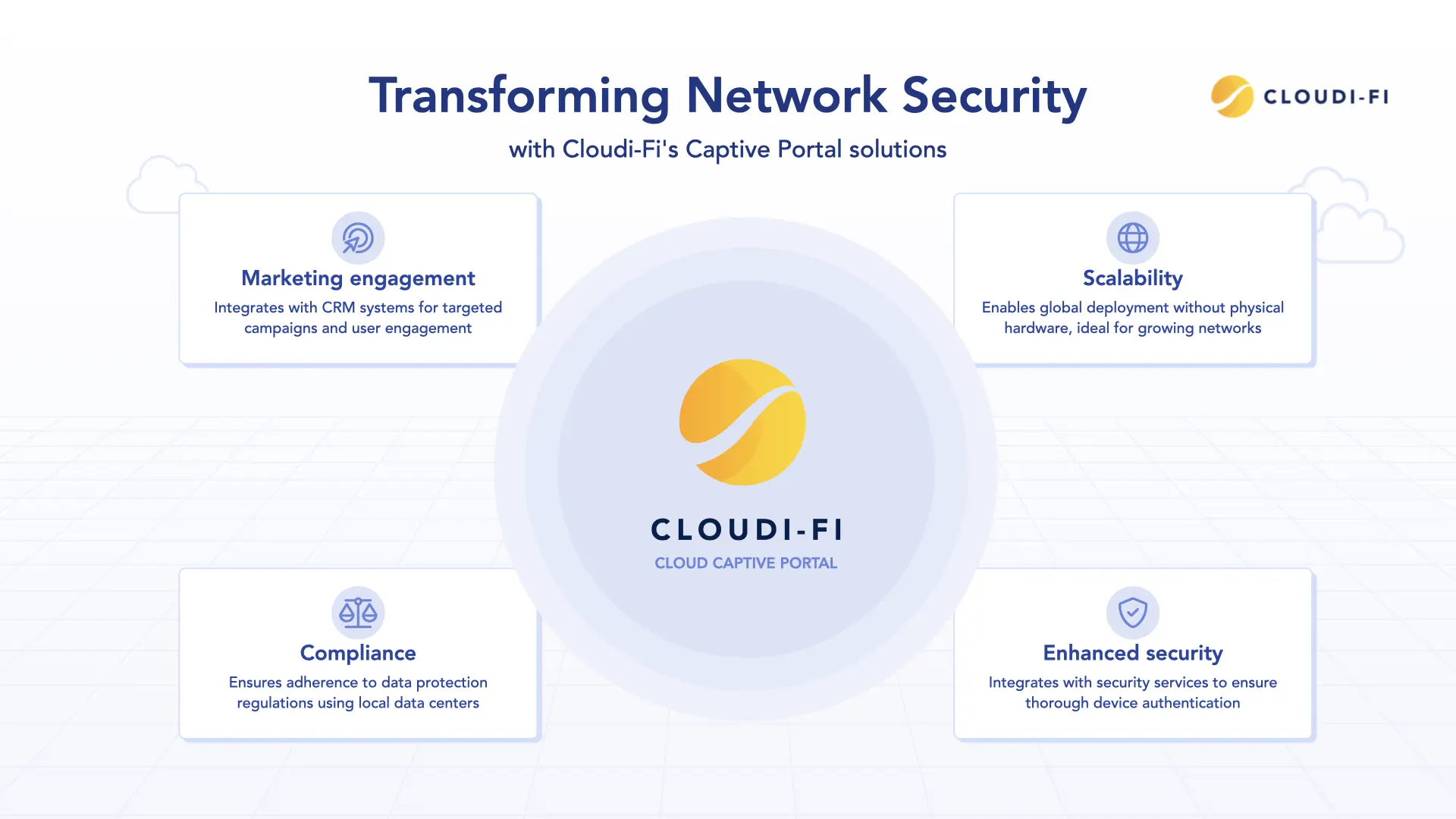
- Scalability: Cloud-based portals can be deployed globally without physical hardware, making them ideal for organizations with dispersed locations or rapidly growing networks.
- Enhanced security: Integrating third-party security services like Zscaler, Palo Alto, Netskope, or FortiSASE Networks strengthens security by adding additional layers of protection, ensuring devices are thoroughly authenticated before gaining network access.
- Compliance: Cloudi-Fi’s solution ensures compliance with data protection regulations such as GDPR by using local data centers to store logs, providing peace of mind for businesses handling sensitive information.
- Marketing and engagement: Beyond security, Cloudi-Fi’s captive portal can integrate with CRM systems to run targeted marketing campaigns, enhancing user engagement and business growth.
Cloud DHCP service: Simplifying IoT device onboarding
The growing number of IoT devices in wireless networks introduces unique security and device management challenges. Cloudi-Fi’s cloud-based DHCP service simplifies this process by automating the onboarding of untrusted IoT devices, ensuring they are correctly assigned IP addresses and meet security policies before accessing the network.
Cloud DHCP service benefits for ZTS:
- Efficient device management: Cloudi-Fi's cloud-based service eliminates the need for on-premises DHCP servers. Devices automatically receive necessary configurations as they connect to the network, reducing manual setup and potential errors.
- Dynamic device access control: Cloudi-Fi can use DHCP fingerprinting to assign IP addresses based on device type, role, or location, enforcing network segmentation and preventing unauthorized devices from accessing critical resources.
- Zero Trust enforcement: Devices are continuously monitored to ensure compliance with access policies. Non-compliant or unknown devices are automatically quarantined or denied network access.
Impact of cloud DHCP services on ZTS:
- Scalability and flexibility: Cloudi-Fi’s DHCP Service scales effortlessly with your network, providing seamless support as more devices—especially IoT devices—are added.
- Reliability: The service is hosted in secure, redundant cloud environments, ensuring high availability and reducing the risk of downtime from hardware failures.
- Cost efficiency: Minimizes the need for physical infrastructure and reduces overhead costs, allowing businesses to scale their networks without significant capital investment.
How Cloudi-Fi strengthens ZTS
- Improved security: Only trusted devices are allowed onto the network, and their behavior is continuously monitored to mitigate potential threats and protect sensitive data.
- Global scalability: Cloudi-Fi’ s infrastructure-agnostic platform supports effortless scaling, freeing organizations from hardware constraints.
- Simplified network management: Centralized control makes it easy for IT teams to manage device onboarding, authentication, and network policies—remotely and efficiently.
- Enhanced user experience: CRM integration allows for secure, personalized engagement and targeted marketing without compromising network integrity.
- Continuous threat detection: Real-time monitoring identifies suspicious activity and policy violations, enabling fast and proactive responses.
In a landscape where Zero Trust is no longer optional, Cloudi-Fi stands out by delivering robust and easy—to—deploy security. It supports organizations in protecting their wireless environments without adding operational complexity.
Conclusion
Cloudi-Fi is a key enabler of Zero Trust Security (ZTS) for wireless networks, offering cloud-native tools like the Cloud Captive Portal and Cloud DHCP Service. These solutions ensure only verified devices access the network while continuously monitoring behavior to maintain a strong security posture. As organizations shift toward perimeter-less architectures, Cloudi-Fi provides the flexibility, scalability, and control needed to implement Zero Trust effectively.








