Every second, thousands of devices knock on your network's door, but should you let them all in? In an era where a single compromised endpoint can cost organizations millions, Network Access Control isn't just another security tool; it's your first and most critical line of defense against unauthorized access, malware propagation, and data breaches.
What is Network Access Control?
Imagine your corporate network as a high-security building. Would you give everyone the same access card, or verify each person's identity and clearance level before granting entry?
That's precisely what Network Access Control (NAC) does for your network infrastructure.
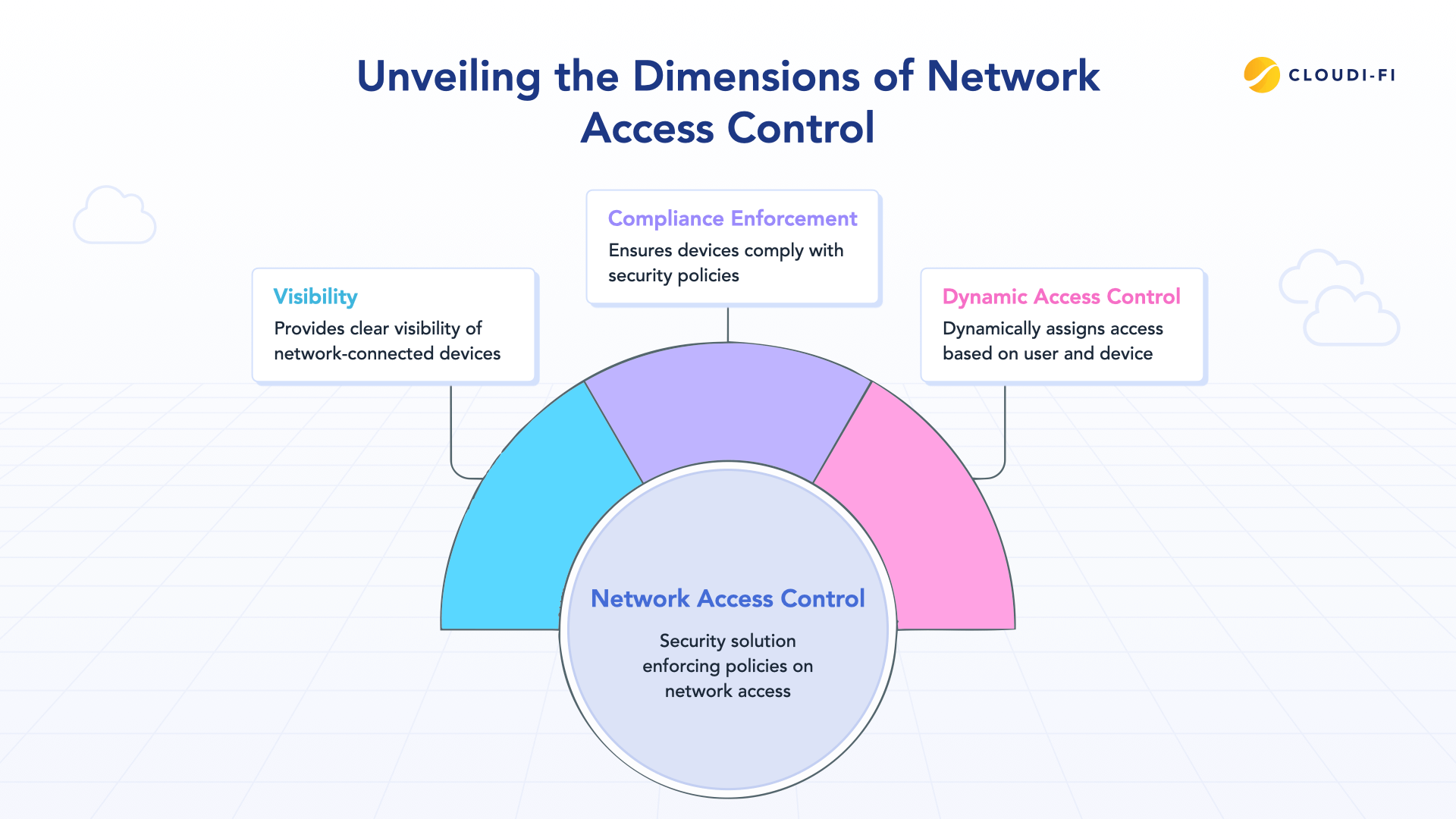
Network Access Control is a security solution that enforces policies on devices attempting to access network resources. At its core, NAC validates the identity of devices and users, checks their compliance with security policies, and determines what level of access they should receive. It acts as an intelligent gatekeeper that continuously monitors who and what connects to your network.
NAC solutions address several critical business needs in today's complex IT environments. First, they provide visibility. You can't secure what you can't see. With the proliferation of IoT devices, BYOD policies, and remote work, organizations often have hundreds or thousands of endpoints connecting to their networks.
Second, NAC enables compliance enforcement. According to Gartner research, organizations that implement NAC reduce security incidents related to non-compliant endpoints by up to 50%. The solution ensures devices meet minimum security requirements like updated antivirus, proper certificates, and enabled firewalls, before granting network access.
Third, NAC provides dynamic access control. Rather than static network segmentation, NAC dynamically assigns access privileges based on user role, device posture, location, and time. A contractor's device might receive guest-level access, while a C-level executive's managed laptop gets full corporate network privileges.
The security challenges NAC confronts head-on
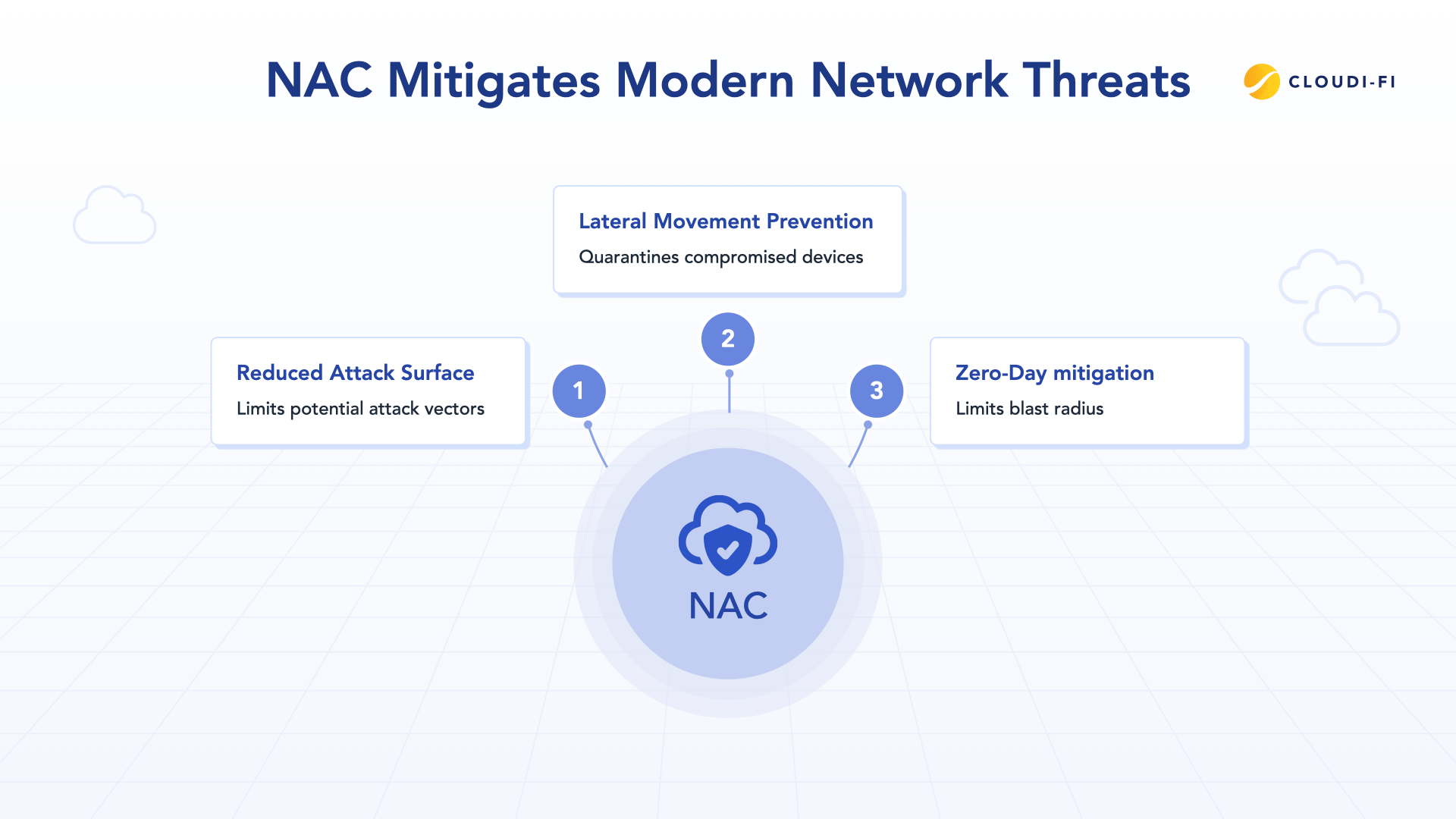
Cybercriminals don't need to break down your front door when they can simply walk through it disguised as a legitimate user. Modern networks face unprecedented security challenges that traditional perimeter defenses simply cannot address.
The BYOD and IoT explosion: The average enterprise now manages over 30,000 connected devices, according to a 2024 IDC study. Each device represents a potential attack vector. When employees connect personal smartphones, tablets, or even smart watches to corporate Wi-Fi, they create security blind spots. IoT devices often ship with default credentials and rarely receive security updates, making them attractive targets for attackers.
Insider threats and lateral movement: The 2024 Verizon Data Breach Investigations Report found that 20% of breaches involved insider threats. Once an attacker compromises a single endpoint or a malicious insider gains access, they can move laterally across the network, escalating privileges and exfiltrating data. Without NAC, a compromised guest device on your network could potentially access sensitive financial databases.
Remote work complexity: With 58% of the workforce now working in hybrid arrangements (Gallup, 2024), the traditional network perimeter has dissolved. VPN connections alone don't validate device health or user context. An employee connecting from a coffee shop on a malware-infected laptop poses the same risk as inviting that malware directly into your datacenter.
Zero-day vulnerabilities: NAC mitigates risks from unknown threats by enforcing baseline security postures. Even if a device harbors a zero-day exploit, NAC can quarantine non-compliant devices, limiting the blast radius of potential attacks.
NAC confronts these challenges through continuous authentication, real-time device posture assessment, automated threat response, and micro-segmentation. When NAC detects a compromised device exhibiting suspicious behavior, it can automatically quarantine that device to a remediation VLAN, preventing lateral movement while maintaining business continuity.
Authentication deep dive: Credentials that guard your network
Your authentication mechanism is only as strong as its weakest credential type, and choosing the wrong one is like using a flimsy padlock on a bank vault. Let's explore the authentication methods that power NAC solutions and understand when to use each.
Digital Certificates (802.1X/EAP-TLS): Digital certificates represent the gold standard of network authentication. In this method, both the device and the authentication server prove their identities using cryptographic certificates issued by a trusted Certificate Authority (CA). The device presents its client certificate, the server validates it, and mutual authentication occurs without transmitting passwords over the network.
Certificates provide exceptional security; they're nearly impossible to phish, can't be brute-forced, and enable automated machine authentication. However, they require robust Public Key Infrastructure (PKI), certificate lifecycle management, and proper deployment procedures. Organizations typically use tools like Microsoft Active Directory Certificate Services or third-party PKI solutions to issue and manage certificates across thousands of endpoints.
Username and Password Authentication (PEAP-MSCHAPv2 or EAP-TTLS): Traditional username/password combinations remain the most common authentication method due to their simplicity and user familiarity. In NAC deployments, these credentials typically authenticate against Active Directory, LDAP, or RADIUS servers. The Protected Extensible Authentication Protocol (PEAP) creates an encrypted tunnel before transmitting credentials, protecting against eavesdropping.
While passwords are convenient, they're vulnerable to phishing, brute-force attacks, credential stuffing, and social engineering. According to the 2024 Verizon DBIR, 81% of hacking-related breaches leveraged stolen or weak passwords. Organizations should enforce strong password policies, implement multi-factor authentication (MFA), and consider passwords a stepping stone toward certificate-based authentication.
PAC Files and EAP-FAST: Protected Access Credentials (PACs) offer a middle ground between certificates and passwords. Cisco's EAP-FAST protocol uses PAC files, small encrypted files stored on devices, to establish secure tunnels for authentication. The server initially provides the client with a PAC through a secure process, and subsequent authentications use this PAC without requiring certificate infrastructure.
PAC files excel in environments transitioning from weak authentication methods to stronger ones, particularly when full PKI deployment isn't immediately feasible. They're less complex than certificates but more secure than plain password authentication. However, PAC files require careful management; if a PAC is compromised, it must be revoked and reissued.
MAC Address Authentication Bypass (MAB): For devices that cannot authenticate, like printers, IP phones, badge readers, NAC uses MAC Authentication Bypass. The switch sends the device's MAC address to the authentication server, which checks it against an approved list. While convenient for headless devices, MAC addresses can be spoofed, making MAB the weakest authentication method suitable only for low-risk IoT devices, combined with additional controls like network segmentation.
Implementing NAC within your IT infrastructure
Deploying NAC isn't a "flip the switch" moment; it's an architectural transformation that touches every corner of your network infrastructure. Successful implementation requires careful planning, phased rollout, and alignment with existing systems.
Infrastructure prerequisites: Your network infrastructure must support 802.1X authentication. This means switches and wireless access points (APs) need to act as authenticators, forwarding authentication requests to your RADIUS server. Most enterprise-grade equipment from vendors like Cisco, Aruba, Juniper, and HPE supports 802.1X, but older hardware may require upgrades. Your wireless controllers must support WPA2-Enterprise or WPA3-Enterprise encryption.
RADIUS server deployment: The RADIUS server is NAC's authentication engine. Popular solutions include Cisco ISE, Aruba ClearPass, FreeRADIUS, Microsoft NPS, and Cloudi-Fi. The RADIUS server integrates with your identity store (Active Directory, Azure AD, LDAP) to validate credentials and applies authorization policies based on user groups, device types, and compliance status.
High availability is critical. Deploy RADIUS servers in redundant pairs across different physical locations. If your primary RADIUS server fails during business hours, thousands of users could lose network access. Many organizations deploy a primary server in their main datacenter, a secondary in a DR site, and load balance authentication requests between them. Cloudi-Fi accelerates the cloud migration by delivering a cloud-native, identity-first approach that modernizes 802.1X and integrates it seamlessly with Zero Trust principles.
Network segmentation strategy: NAC enables dynamic VLAN assignment based on user identity and device posture. Design your VLAN structure before deployment: corporate-managed devices might get VLAN 10 with full access, BYOD devices get VLAN 20 with internet-only access, guest devices get VLAN 30 with isolated web browsing, and quarantined devices get VLAN 99 for remediation.
Deployment guidelines for IT teams: From planning to production
The difference between a successful NAC deployment and a nightmare that brings down your entire network lies in methodical execution and respecting the golden rule: never disrupt business operations. Here's your roadmap.
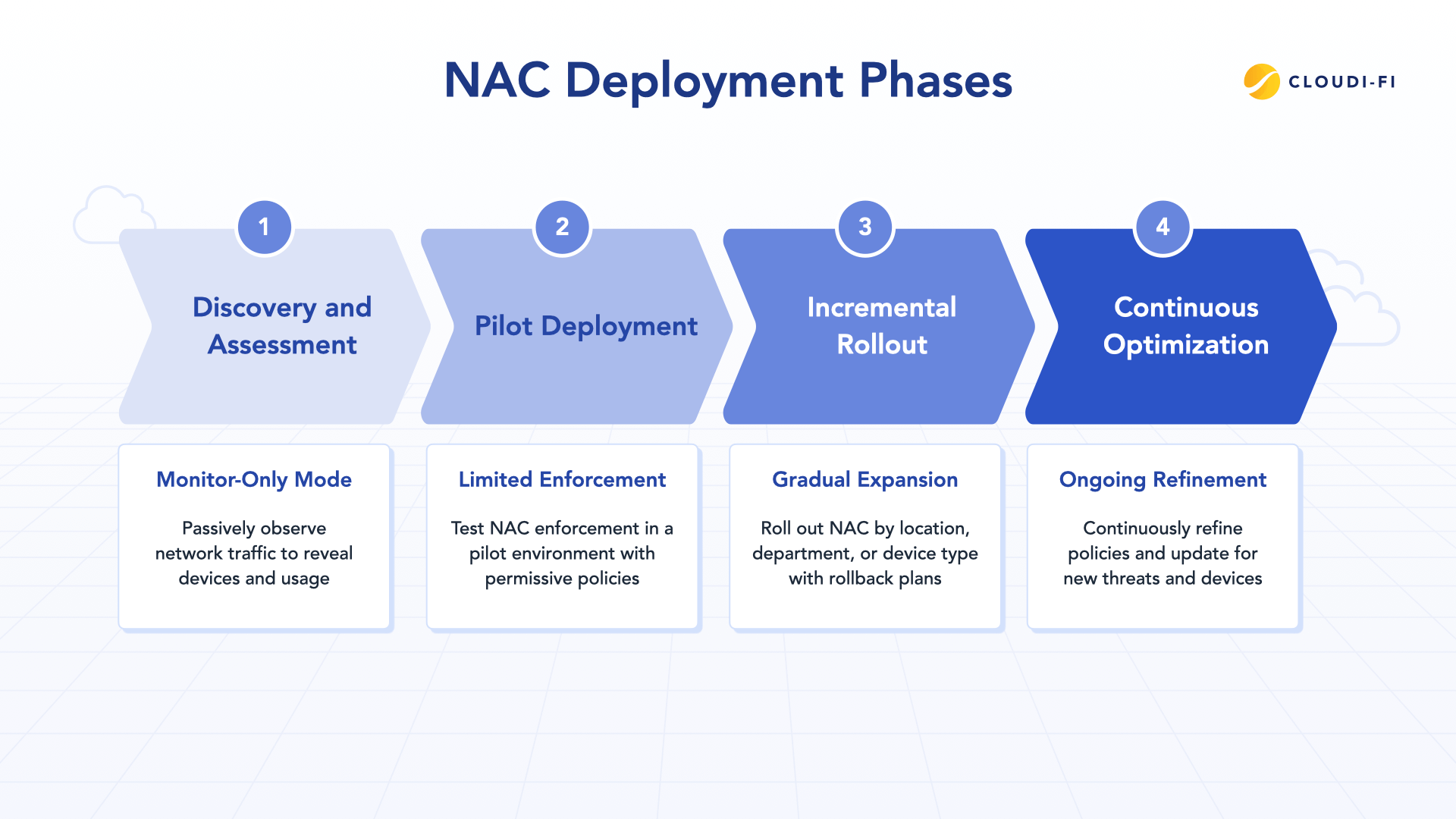
Phase 1 - Discovery and assessment: Begin in monitor-only mode. Deploy NAC to passively observe network traffic without enforcing policies. This discovery phase reveals what's actually on your network. Organizations typically discover 30-40% more devices than they anticipated, including forgotten servers, rogue access points, and shadow IT.
Document everything: device types, connection methods, peak usage times, and authentication protocols currently in use. Interview department heads about critical systems that cannot tolerate downtime. Identify pilot groups, typically IT departments or a small branch office, for initial deployment.
Phase 2 - Pilot deployment: Implement NAC enforcement in your pilot environment with reduced scope. Configure permissive policies that allow access while logging authentication attempts. This phase tests your RADIUS server configuration, certificate deployment processes, and troubleshooting procedures without impacting the broader organization.
Monitor closely and iterate. When issues arise, document the problem, root cause, and solution. Build a troubleshooting playbook. Common pilot phase issues include certificate trust problems, incorrect VLAN assignments, and authentication timeouts. Resolve these in the pilot before expanding.
Phase 3 - Incremental rollout: Roll out NAC by location, department, or device type. Start with less critical sites and gradually expand. Maintain rollback plans for each phase. If issues emerge, you can quickly revert that segment to pre-NAC configuration without affecting other areas.
Communication is paramount. Notify users well in advance about changes to their network experience. Provide clear instructions for certificate installation or password requirements. Establish a dedicated help desk queue for NAC-related issues during rollout periods.
Phase 4 - Continuous optimization: NAC deployment never truly ends. Continuously refine policies based on usage patterns and security intelligence. When new threats emerge, update posture requirements. When new device types appear, create appropriate authorization profiles. Schedule quarterly reviews of authentication logs to identify anomalies and policy violations.
Deployment checklist
Checklists don't just prevent mistakes; they transform complex deployments into repeatable, predictable processes that even new team members can execute flawlessly.
Before deployment
Infrastructure readiness:
- Verify all network switches support 802.1X and are running the current firmware
- Confirm wireless infrastructure supports WPA2/WPA3-Enterprise encryption
- Deploy redundant RADIUS servers with load balancing configured
- Establish RADIUS server connectivity to identity stores (AD, LDAP, Azure AD)
- Design a VLAN structure for different authorization levels
- Configure VLAN interfaces on the routing infrastructure with appropriate ACLs
- Implement management VLAN access for out-of-band administration
Authentication infrastructure:
- Deploy or validate the existing PKI infrastructure if using certificates
- Create certificate templates for different device types
- Test certificate auto-enrollment and renewal processes
- Configure certificate revocation list (CRL) and OCSP responder
- Establish password policies in Active Directory aligned with NAC requirements
- Create service accounts with appropriate permissions for RADIUS-AD integration
Policy development:
- Document all user roles and their required access levels
- Identify all device types requiring network access
- Define compliance requirements (AV status, OS version, patch level, firewall state)
- Create authorization policies for each device type and user role combination
- Design quarantine and remediation workflows for non-compliant devices
- Establish exception processes for temporary access requirements
Team preparation:
- Train network and security teams on NAC architecture and troubleshooting
- Train help desk staff on common NAC user issues and resolutions
- Develop user-facing documentation and FAQs
- Create network diagrams showing NAC architecture and data flows
- Establish escalation procedures for complex issues
During deployment
Technical execution:
- Enable monitor-only mode in pilot areas
- Verify all expected devices appear in NAC inventory
- Validate authentication success rates meet 95%+ baseline
- Test each authorization policy with representative devices
- Verify VLAN assignments occur correctly for each policy
- Confirm posture assessment accurately detects compliance status
- Test remediation workflows for non-compliant devices
- Validate failover to secondary RADIUS server functions properly
Change management:
- Obtain change control approval for each deployment phase
- Schedule deployment during maintenance windows
- Notify affected users 72 hours and 24 hours before changes
- Staff help desk with additional support during deployment
- Have rollback procedures documented and tested
- Maintain an open communication channel with the deployment team (conference bridge)
Monitoring and validation:
- Monitor authentication success/failure rates in real-time
- Track help desk ticket volume for NAC-related issues
- Review logs for unexpected authentication failures
- Verify business-critical applications function normally
- Document any deviations from expected behavior
- Update the troubleshooting playbook with new issues encountered
After deployment
Operations handoff:
- Transfer monitoring responsibilities to NOC/SOC teams
- Provide final as-built documentation, including configurations and diagrams
- Deliver a comprehensive troubleshooting guide to support teams
- Conduct knowledge transfer sessions for operations staff
- Establish SLAs for NAC availability and authentication response times
Optimization and tuning:
- Review authentication logs to identify authorization policy gaps
- Analyze false positive quarantines and adjust posture policies
- Fine-tune session timeout and re-authentication intervals
- Optimize RADIUS server performance based on load patterns
- Review and update device profiling rules for accuracy
Continuous improvement:
- Schedule quarterly policy reviews and updates
- Implement automated compliance reporting for leadership
- Integrate NAC events with SIEM for correlation and alerting
- Plan certificate renewal and rotation procedures
- Conduct annual disaster recovery testing for RADIUS infrastructure
- Monitor industry trends for new authentication methods and NAC capabilities
Conclusion: NAC as your security force multiplier
Network Access Control represents a fundamental shift from perimeter-based security to identity-based, Zero Trust architecture. By validating every device and user before granting access, continuously monitoring compliance, and dynamically enforcing policies, NAC transforms your network from a flat, vulnerable surface into a defensible, intelligent infrastructure.
The investment in NAC pays dividends beyond security; organizations gain unprecedented visibility into their networks, can enforce compliance requirements automatically, and respond to threats in real-time. While deployment requires careful planning and phased execution, following the guidelines and checklists outlined here will help your IT team implement NAC successfully without disrupting business operations.
Remember: NAC isn't a project with a finish line; it's an ongoing security practice that evolves with your organization's needs and the threat landscape. Start with strong fundamentals, deploy methodically, and continuously optimize. Your future self and your CISO will thank you when NAC prevents the breach that could have cost millions.








