Network Access Control explained
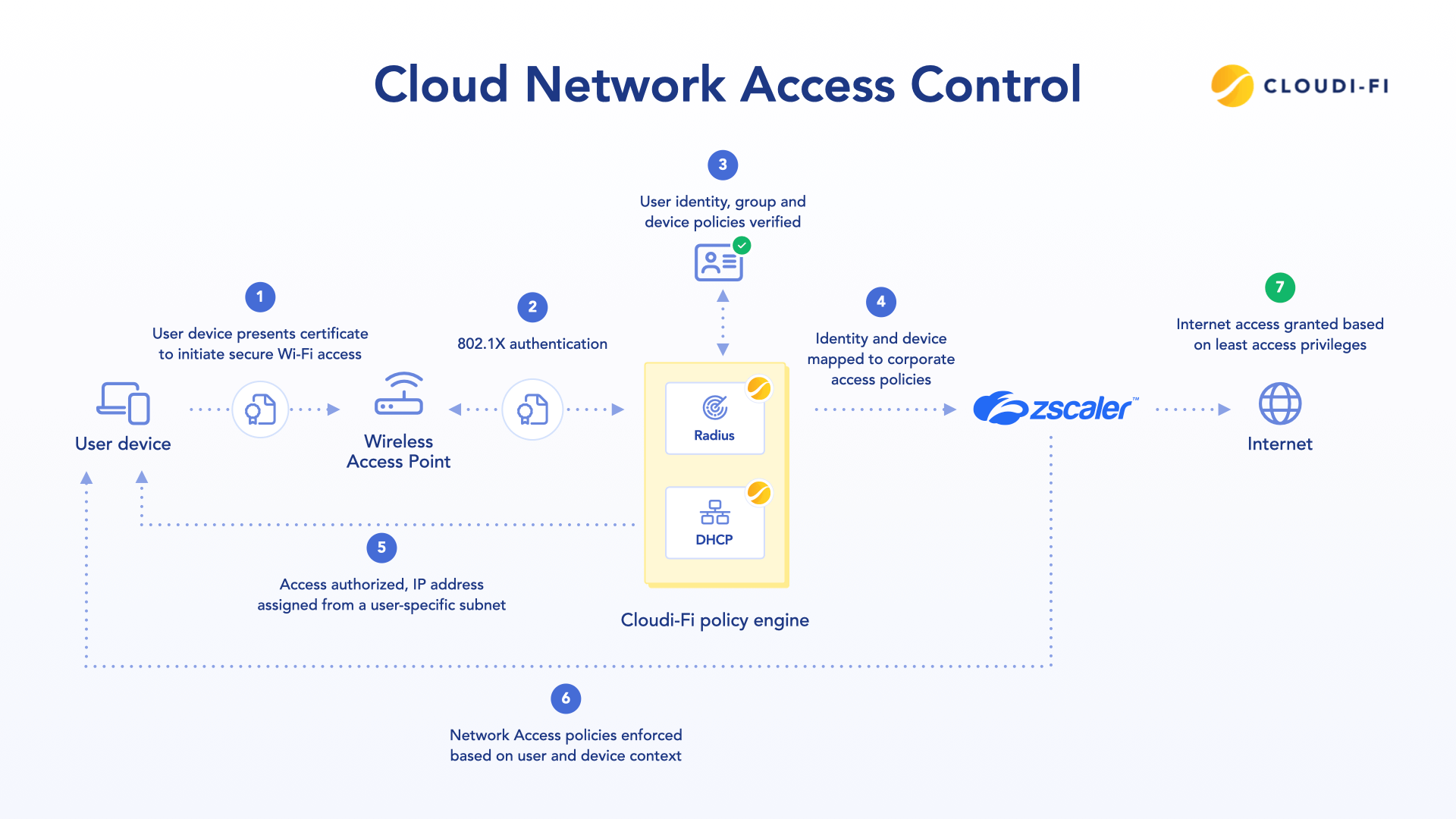
Network Access Control (NAC) is a cybersecurity framework that manages which users, and devices can connect to an organization’s network. It works by authenticating identities—including managing user identities, using authentication methods such as 802.1X, RADIUS, and certificates, checking device compliance, and enforcing access policies to keep unauthorized or risky endpoints out.
A NAC system acts as a security solution that integrates with network management tools to verify user identities and enforce security policies.
As networks expand with remote work, IoT devices, and cloud services, traditional perimeter-based security is no longer enough. NAC provides centralized visibility and control, supporting modern security models like Zero Trust.
What NAC does
NAC ensures that only authorized and compliant devices and users can access sensitive resources. It combines:
- Authentication: verifies user or device identity to authenticate users and devices (passwords, multi-factor authentication (MFA), digital certificates).
- Authorization: grants access only to approved resources based on roles, policies, and assigns access levels according to compliance status.
- Device compliance checks: ensures endpoints, including employee devices, meet security standards (antivirus, patches, encryption).
- Continuous monitoring: tracks device behavior after access is granted and can quarantine risky endpoints, providing restricted access to non-compliant devices until requirements are met.
In summary, NAC enforces policies so that only compliant devices and authenticated users can access network resources, protecting the organization's infrastructure.
How NAC works
- Device detection: NAC identifies any device connecting via wired, wireless, or VPN. Each access attempt is logged and evaluated.
- Identity verification: The network access server receives the access request and initiates authentication using methods like 802.1X, RADIUS, or Active Directory.
- Policy evaluation: The policy server evaluates user and device attributes, such as security posture, role, location, and time, to determine compliance.
- Enforcement: Based on the evaluation, the NAC system will grant access, deny access, or provide limited access. Non-compliant devices may be denied access and enter a quarantine network. Only after successful checks do users or devices obtain access to network resources.
- Ongoing monitoring: Devices remain under continuous security checks.
Key features of Network Access Control solutions
- Authentication & authorization: Enforces strong identity controls and least-privilege access.
- Endpoint compliance & posture assessment: While compliance checks are applied to network endpoints, it's not universal for all. Headless IoT/OT and many BYOD/guest devices often cannot run a posture agent and therefore only receive profiling and restricted access, rather than full posture assessment.
- Network visibility: Discovers all connected endpoints, including shadow IT and IoT. NAC provides increased network visibility into all connected devices and endpoint devices.
- Granular policy enforcement: Adjusts access by role, device type, location, and time.
- Quarantine & self-remediation: Isolates compromised or non-compliant devices and guides users to fix issues.
- Integration with security tools: Works with SIEM, EDR, and Zero Trust frameworks. NAC integrates with network infrastructure and dynamic/downloadable ACLs or policy tags depending on platform. lists for controlling access.
Types of NAC
- Pre-admission NAC (also known as pre admission network control): Devices are checked before joining the network to ensure compliance with security policies and proper authorization; highly secure but may delay access.
- Post-admission NAC: Devices connect first but are continuously monitored to support post-admission network security; this approach can dynamically adjust access levels based on user roles or device status, enforcing security policies as needed.
- Role-based access control (RBAC): Assigns access and user permissions by user role (e.g., HR staff, guests, IoT sensors), regulating access to network resources and establishing authentication protocols.
- Time-based access control: Limits network availability to defined hours for contractors or sensitive systems; can be applied to wireless networks and can enforce limited network access for certain users or devices, such as guests or non-compliant endpoints.
Benefits of Network Access Control
- Stronger security: Blocks unauthorized access, protects sensitive data, and prevents lateral movement.
- Improved visibility: Complete inventory of devices, including IoT and BYOD.
- Regulatory compliance: supports the access control and logging portions. Other layers (encryption, DLP, governance) are still needed.
- Reduced breach costs: Automation cuts IT workload and speeds incident response.
- BYOD & remote work enablement: Safely supports personal and off-site devices by implementing NAC solutions to ensure network security and enforce security policies for all devices.
- Simplified management: Centralized policy control reduces complexity and human error.
In summary, organizations implement NAC solutions to align with their security policy and ensure network security.
Common use cases
- BYOD management: Apply security standards to personal laptops and smartphones.
- Guest access: Provide isolated internet access to visitors while protecting internal assets.
- Third-party & contractor access:Time-limited, role-based permissions for vendors and partners.
Managing IoT devices and securing medical devices
As organizations connect more IoT and medical devices to their corporate networks, the need for robust Network Access Control (NAC) becomes critical. These devices often lack built-in security features, making them attractive targets for attackers seeking unauthorized access. NAC solutions help organizations gain visibility into all connected devices by automatically discovering and profiling them to determine their type, behavior, and risk level.
Because many IoT and medical devices do not support traditional authentication methods such as 802.1X, NAC enforces access policies based on device profiling and segmentation rather than user-based authentication. This ensures that only authorized and compliant devices can communicate with sensitive parts of the network. For medical devices, which frequently handle sensitive patient data, NAC provides an essential layer of control, isolating noncompliant or unknown devices and minimizing exposure to potential threats. By combining discovery, profiling, and policy enforcement, NAC helps organizations safeguard networked resources, maintain compliance, and reduce the risk of breaches originating from IoT and medical devices.
Guest access and network security
Allowing guest access to a corporate network can introduce significant security risks if not properly managed. Network Access Control (NAC) solutions help address these challenges by providing secure, segmented access for guests without compromising overall network protection. Unlike corporate devices, guest users typically connect with unmanaged personal devices that cannot undergo posture checks such as antivirus or firewall verification.
Instead of enforcing compliance, NAC focuses on segmentation, automatically identifying guest connections and restricting them to isolated network zones or internet-only access. This prevents guests from reaching sensitive corporate systems while still allowing them the connectivity they need. Although methods like certificate-based or multi-factor authentication are not always feasible for guests, NAC can still apply tailored access policies based on user role, device type, or connection method.
By isolating guest traffic and enforcing clear access boundaries, organizations can offer convenient guest connectivity while maintaining strong security controls across the corporate network.
Incident response and network security
When a security incident occurs, rapid containment and response are essential to protect network resources. Network Access Control (NAC) solutions play a supporting role in incident response by helping organizations quickly identify and isolate compromised devices to prevent further spread. While NAC does not directly remediate infected or compromised endpoints, it can automatically enforce access controls—restricting affected devices to quarantine networks or blocking them from accessing critical systems. In some cases, NAC solutions also provide self-remediation portals that guide users through required security steps before regaining access.
NAC enhances visibility by correlating device identity, user information, and connection details (such as switch port or access point), giving incident response teams valuable context when investigating security events. However, detailed malware analysis and full remediation typically rely on endpoint detection and response (EDR) or security information and event management (SIEM) tools.
By integrating NAC into their incident response workflows, organizations can strengthen containment efforts, support faster recovery, and ensure that only authorized and compliant devices remain connected during and after a security event.
NAC and Zero Trust security
Network Access Control (NAC) plays a foundational role in implementing a Zero Trust architecture , the “never trust, always verify” security model. NAC governs network-level access, determining who and what can join the corporate LAN, WLAN, or VPN. By continuously monitoring connected devices, enforcing segmentation, and verifying device compliance, NAC ensures that only authorized and trusted entities gain network connectivity.
Zero Trust Network Access (ZTNA), on the other hand, governs application-level access, controlling who or what can reach specific SaaS or private applications based on identity and context. While NAC and ZTNA operate at different layers, they are complementary components of a comprehensive Zero Trust strategy.
Together, NAC provides the first line of defense at the network perimeter, while ZTNA extends granular access control to applications—creating a unified, end-to-end Zero Trust framework that protects both network and application resources.
If you want to learn more about how NAC and 802.1X authentication work together, read our introduction to 802.1X and NAC authentication with Cloudi-Fi Cloud RADIUS.
FAQ
Is NAC being replaced by Zero Trust?
Network Access Control (NAC) is not being replaced by Zero Trust; instead, NAC serves as a foundational component within Zero Trust security architectures. NAC provides the continuous visibility, control, and enforcement needed to implement Zero Trust principles effectively. By continuously verifying trust levels, enforcing segmentation, and integrating with identity providers and Zero Trust Network Access (ZTNA) solutions, NAC helps ensure that only authorized and compliant users and devices can access network resources. In this way, NAC complements and strengthens Zero Trust strategies rather than being supplanted by them.










