The rise of cloud technology, remote work following the global pandemic, the strict requirements for personal data protection, and the maturity of Software-Defined Wide Area Networking (SD-WAN) have all contributed to the acceleration in the use of Local Internet Breaks. Many organizations are adopting due to its scalability, cost-effectiveness, enhanced security, and support for regulatory compliance.
What is Local Internet Breakout and why it is gaining traction
Local Internet Breakout is an internet access point located as close to the user as possible. Instead of sending all data through a central hub or data center, Local Internet Breakout lets branch offices and remote sites connect directly to the internet. This approach becomes more popular as businesses rely more on cloud services and need quicker and more efficient connections.
Clear signs of Local Internet Breakout growth in practice
Given that Local Internet Breakout is a core capability of SD-WAN, the expansion of the SD-WAN market strongly indicates a parallel rise in the adoption of Local Internet Breakout. The SD-WAN market size is estimated at USD 9.33 billion in 2025, and is expected to attain USD 35.83 billion in 2030, at a compounded annual growth rate of 30.42% in the forecast period – from 2025 to 2030. (source)
Drivers of Local Internet Breakout adoption
Traditionally, companies have routed all data through centralized data centers, allowing for unified security inspections, streamlined compliance, and supported network control. However, market demands for speed, scalability, and security are accelerating Local Internet Breakout adoption because it helps:
- Improving performance and reducing latency: allowing internet-bound traffic to exit directly at the local site enables users to experience faster application performance. With multiple internet access points, Local Internet Breakout reduces the risk of a single point of failure.
- Cost efficiency: reducing the need for expensive multiprotocol label switching (MPLS) circuits, particularly for cloud-bound traffic.
- Flexible and scalable network solution: scales efficiently to support new locations and traffic volumes, with centralized SD-WAN-based management.
Read more about Local Internet Breakout and its benefits.
Implications of Local Internet Breakout on personal data protection
In addition to its technical implications, Local Internet Breakout presents legal and compliance considerations, especially in the era of growing concerns over personal data protection, where companies are subject to increasing regulatory requirements to safeguard the rights of data subjects.
Advantages of Local Internet Breakout
Data localization
Many countries require localizing data of users within their territories to ensure the protection level, such as China or India. By enabling routing data within the users’ country and regions, Local Internet Breakout helps organizations to meet this requirement without having to follow a complex process to establish a data center.
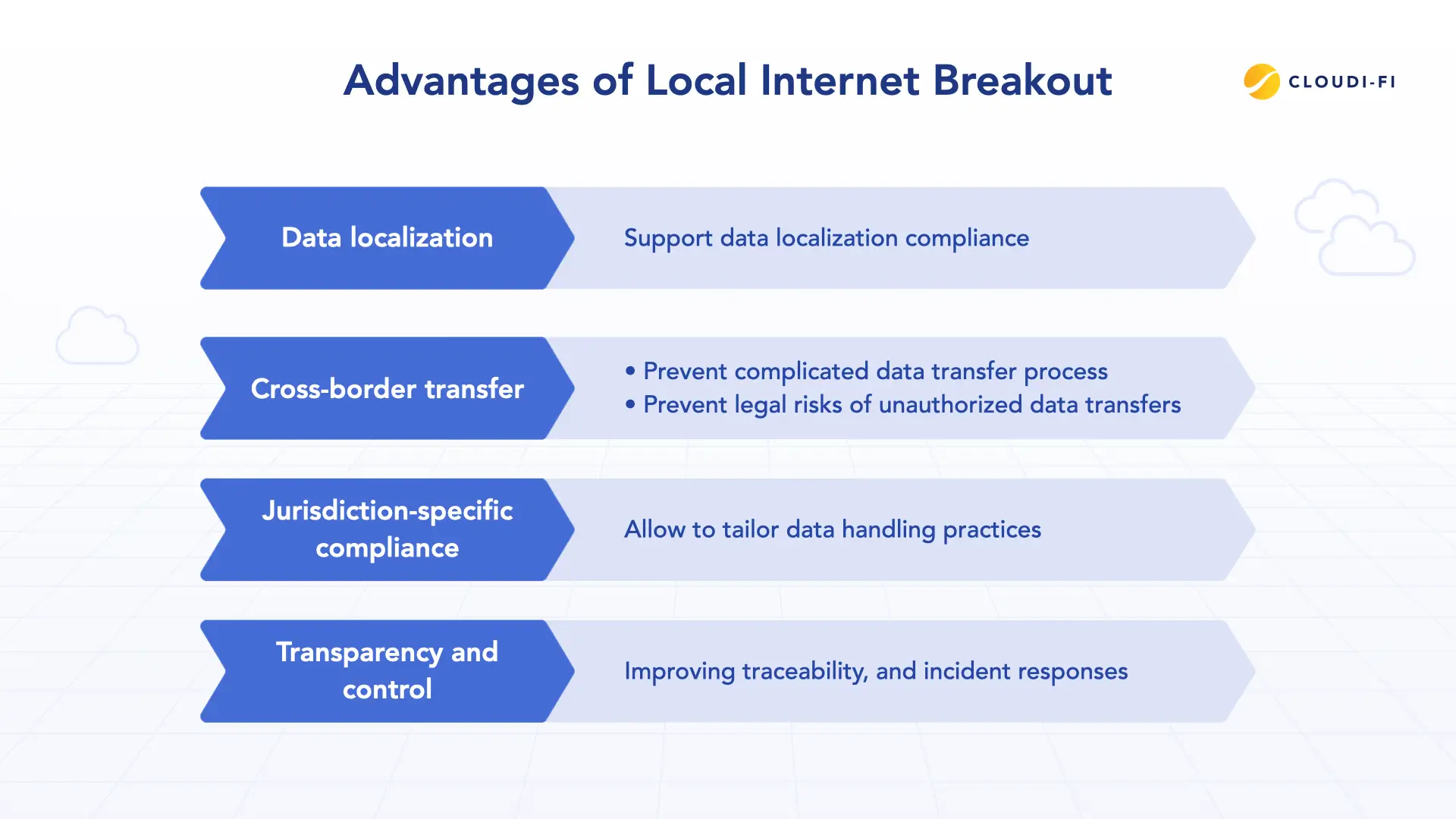
Cross-border transfer
Most countries either mandate data localization or impose complicated cross-border data transfer regulations involving significant government oversight. As a result, compliance can still be challenging despite organizations’ best efforts. Local Internet Breakout enables easy data localization, which will help prevent these cumbersome processes and potential legal risks associated with international data transfers.
Jurisdiction-specific compliance
Different countries and regions will have different rules for processing, monitoring, and retaining data. Since data is kept within the territories of each country/region, Local Internet Breakout allows organizations to define local-specific routing rules. Data processed through Local Internet Breakout can be monitored and logged within regional boundaries, which makes it easier for controllers/processors to apply local regulations if required.
Transparency and control
Local Internet Breakout allows processing data closer to the source, which will improve traceability, incident response, and audit readiness.
In contrast, using Local Internet Breakout also introduces some challenges that companies need to address before deploying it.
Disadvantages of Local Internet Breakout
Decentralized logs
Since data traffic is monitored and logged at multiple access points, it scatters the data trails, making it difficult for organizations to monitor data flow and access logs.
Various protection policies
Local Internet Breakout allows for tailoring data handling practices, however, the existence of diverse processes and policies at each local point could make it challenging to maintain consistent oversight and ensure uniform compliance.
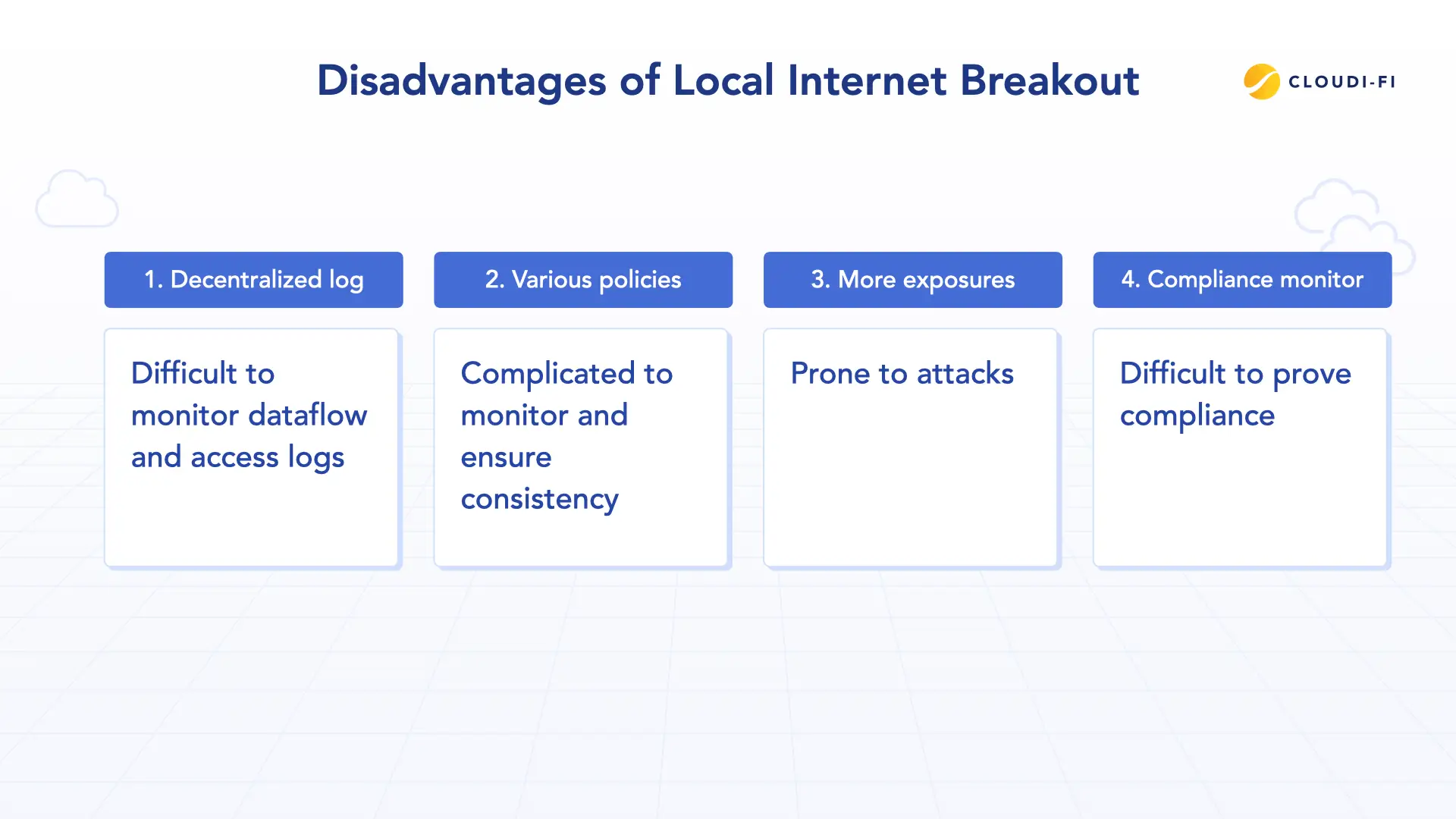
More exposures
Multiple breakout points equal more potential entry points for attacks. If security is not ensured across all Local Internet Breakout locations, data breaches or unauthorized access could increase.
Compliance monitor
Managing multiple processes and policies across Local Internet Breakout locations requires extensive documentation and administration, which can become a challenge. It could be an issue if organizations cannot prove their compliance across their whole Local Internet Breakout locations because of administrative burdens.
Mitigation strategies for Local Internet Breakout challenges
Centralized logging and analytics platform
Provide a centralized logging and analytics platform to aggregate logs from all Local Internet Breakout locations to facilitate the monitoring of data flow and log access.
Internationally recognized standards
Monitor and update local applicable regulations to ensure compliance. Maintain consistent oversight and uniform adherence by following internationally recognized standards, such as the General Data Protection Regulation, which is referred to and applied by many countries in the world.
Security and zero trust integration
Integrate Zero Trust Network Access and cloud-based security into the network to protect the system against potential attacks.
Centralized compliance administration
Store and centralize compliance documentations, and organize them neatly and systematically to ensure easy access when required.
Cloudi-Fi’s approach to secure Local Internet Breakout adoption
As Local Internet Breakout adoption grows and data privacy regulations tighten, companies need to equip themselves with knowledge about Local Internet Breakout as well as its benefits and challenges to be prepared. With Cloudi-Fi’s services, we ensure that exposure is minimized by applying Zero Trust principles, requiring every user to be authenticated under all circumstances. We also centralize logging for consistent and streamlined control across our systems. At the same time, Cloudi-Fi continuously monitors evolving technologies and local regulations to ensure our services remain compliant, secure, and relevant in a rapidly evolving digital environment.
FAQ
What is Local Internet Breakout?
Local Internet Breakout is an internet access point located close to the users that allows traffic to exit directly from a local branch, office, or remote location. (source)
What is a Software-defined Wide Area Network (SD-WAN)?
SD-WAN is a technology that uses software to manage and route network traffic across multiple connections between branch offices, data centers, and the cloud. (source)
What role does SD-WAN play in enabling Local Internet Breakout?
SD-WAN provides intelligence, control, and security needed to manage decentralized internet access efficiently. SD-WAN simplifies how traffic is routed in the branch, and makes it easy to establish Local Internet Breakout.
Is Local Internet Breakout compliant with data localization requirements like those in China or India?
Yes, Local Internet Breakout allows data to be processed and transmitted within the local region, however, it still requires security, storage, and processing compliance policies.








