Picture this: Your branch office employees are trying to access Microsoft 365, and their data is taking a detour through your central headquarters hundreds of miles away before reaching the cloud. It's like taking a flight from Paris to London via New York, completely inefficient, right? Welcome to the world of traditional hub-and-spoke network architecture, and why it's time for a change. The good news? There's a smarter way forward, and it's called Local Internet Breakout.
What is Local Internet Breakout?
Local Internet Breakout is essentially an internet access positioned as close to your users as possible. Instead of forcing all internet-bound traffic to backhaul through your corporate data center, Local Internet Breakout allows branch offices and remote locations to connect directly to the internet via a local Internet Service Provider (ISP).
Think of it this way: the traditional model is like sending all your mail to headquarters for postage, even when there's a perfectly good post office right next to your branch. Local Internet Breakout is simply using that local post office, it just makes sense.
Here's what technically happens: when traffic from your branch office needs to reach a cloud application like Salesforce or Microsoft 365, it routes directly to the internet through a local gateway at the edge of your network. This bypasses the corporate core network entirely, reducing latency, improving speed, and lowering costs.
How Local Internet Breakout works
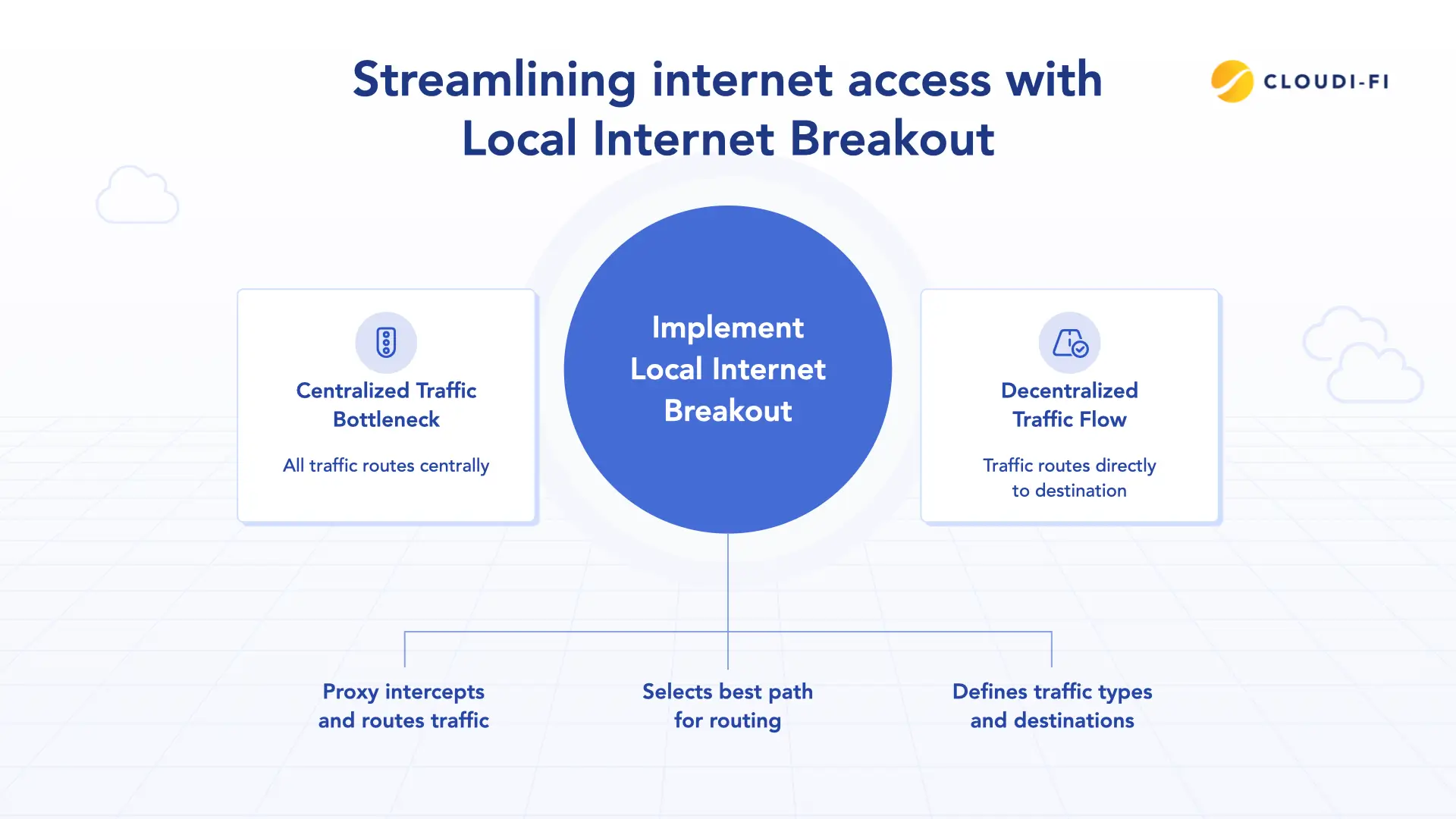
The architecture is more straightforward than you might think. In a typical Local Internet Breakout setup:
- The local gateway approach: You install a gateway at the network edge (close to end-users) that acts as a proxy, intercepting traffic and routing it directly to the appropriate internet destination.
- SD-WAN integration: Software-Defined WAN overlays work hand-in-hand with Local Internet Breakout. SD-WAN uses software-defined policies to intelligently select the best path for routing traffic; whether it's heading to the internet, cloud applications, or your data center.
- Policy-based routing: You define which traffic types go where. Critical internal applications might still route through your data center, while SaaS traffic breaks out locally.
The beauty is in its flexibility. According to Zscaler, organizations increased their available bandwidth at some locations by up to 15 times using Local Internet Breakout, making MPLS upgrades completely unnecessary.
Why the migration to Local Internet Breakout is no longer optional
The enterprise landscape has fundamentally changed, and the numbers tell a compelling story:
The cloud revolution is here: By early 2025, more than 70% of enterprise workloads had migrated outside traditional data centers, according to Markets and Markets research. Companies are using an average of 106 SaaS applications in 2024 (Hostinger), and worldwide SaaS spending is expected to hit $300 billion by 2025.
When most of your WAN bandwidth is consumed by traffic destined for the internet and your employees spend their days in Microsoft 365, Zoom, Salesforce, and other cloud applications, backhauling everything to a central data center becomes not just inefficient, but genuinely problematic for user experience.
The SD-WAN market explosion: The SD-WAN market is projected to expand from USD 7.91 billion in 2025 to USD 21.67 billion by 2030, growing at a CAGR of 22.3% (Markets and Markets). This isn't just hype, it's organizations voting with their budgets.
Real business impact: Companies migrating their core enterprise applications to Microsoft Azure and implemented Cisco SD-WAN to connect global offices via Local Internet Breakout. The results? Faster access, better user experience, and reduced costs.
The challenges of implementing Local Internet Breakout
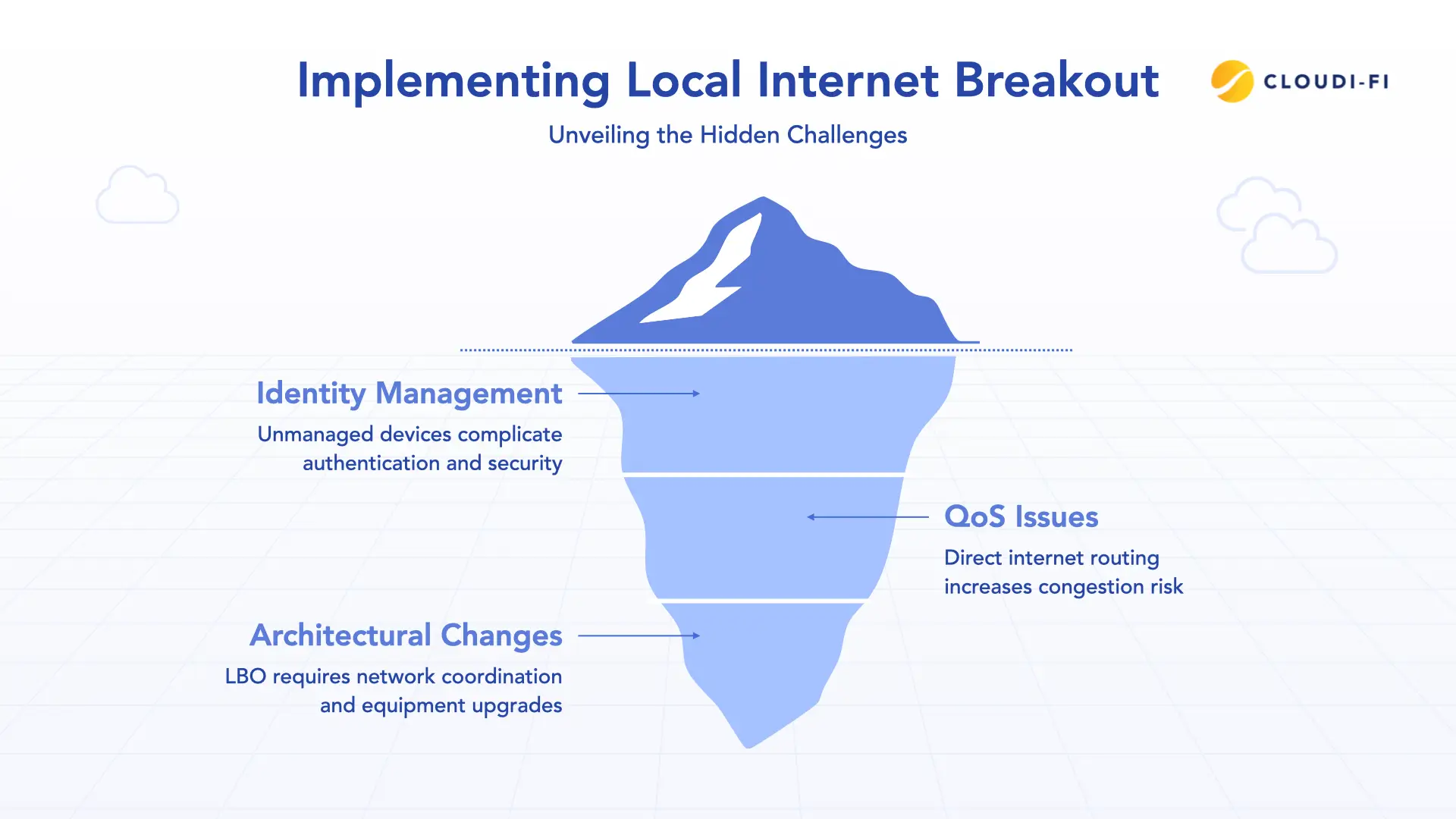
1. Security becomes distributed
When you enable local breakouts at every branch, you're essentially creating multiple points of egress. Each one needs the same level of security you previously had centralized at your data center. Deploying traditional security appliances at each branch simply isn't viable, it's expensive, complex, and doesn't scale.
2. Identity management complexity
Your corporate devices might authenticate fine, but what about guests, BYOD (Bring Your Own Device), and IoT devices? These unmanaged devices need to be identified, authenticated, and secured, and this is where things get tricky with traditional approaches.
3. Quality of service concerns
When traffic routes directly to the internet, there's a greater risk of congestion and network overload. You need sufficient capacity and the ability to prioritize traffic appropriately to maintain consistent user experience.
4. Architectural changes required
Moving to Local Internet Breakout isn't just flipping a switch. It involves coordination between different network elements, changes to routing policies, and often requires upgrading or replacing existing equipment.
How to leverage Local Internet Breakout effectively
The key to success with Local Internet Breakout lies in three critical areas:
1. Cloud-based security services: Instead of replicating security appliances at every location, leverage cloud-delivered security. This is where the magic happens. Security travels with your traffic, regardless of where it breaks out to the internet.
2. Intelligent traffic management: Use SD-WAN policies to determine which applications should break out locally and which should still traverse your core network. Not all traffic is created equal.
3. Comprehensive identity and access management: Every device and user (corporate, guest, BYOD, or IoT) needs to be properly identified and secured based on their profile and trust level.
Why SaaS solutions enhance local breakouts: The cloud-native advantage
Traditional, appliance-based security simply cannot keep pace with the dynamic, distributed nature of modern networks. Here's why SaaS solutions are better suited for local breakouts:
- Infrastructure agnostic: Cloud-based solutions don't care where your breakout happens, they provide consistent security everywhere.
- Highly ccalable: Adding a new branch? No need to ship hardware or deploy appliances.
- Centralized management: One interface to manage security policies across all locations.
- Always current: Security updates deploy automatically without you managing patches and upgrades.
- Cost effective: No capital expenditure on hardware, just operational expenses that scale with usage.
Cloudi-Fi + Zscaler integration: A perfect match for Local Internet Breakout
Let’s introduce why the integration between Cloudi-Fi and Zscaler creates a powerful solution for Local Internet Breakout scenarios.
The challenge solved together
Zscaler excels at authenticating and securing employees and their managed corporate devices. It's a cloud-based security platform with a global network of data centers ensuring fast, secure connectivity. But here's the thing: Zscaler alone doesn't address the challenge of identifying and authenticating unmanaged devices: guests, BYOD, and IoT devices.
Cloudi-Fi, as a cloud-based NAC (Network Access Control) and identity provider, specifically handles the authentication and identification of these untrusted devices and users. The integration is native and seamless.
How it works in practice
Here's the flow:
- Open SSID with Cloudi-Fi portal: Branch offices configure an open SSID for guests and BYOD devices.
- Automatic redirection: When unmanaged devices try to access the internet, Zscaler automatically redirects them to the Cloudi-Fi captive portal.
- Identity verification: Cloudi-Fi authenticates users through various methods (SMS, social networks, email) and identifies IoT devices.
- Policy enforcement: Once authenticated, Zscaler applies specific security policies based on the user profile or device category.
- Secure breakout: Traffic then breaks out locally to the internet with appropriate security in place.
The real benefits
According to Zscaler and Cloudi-Fi deployment guide, this integration provides:
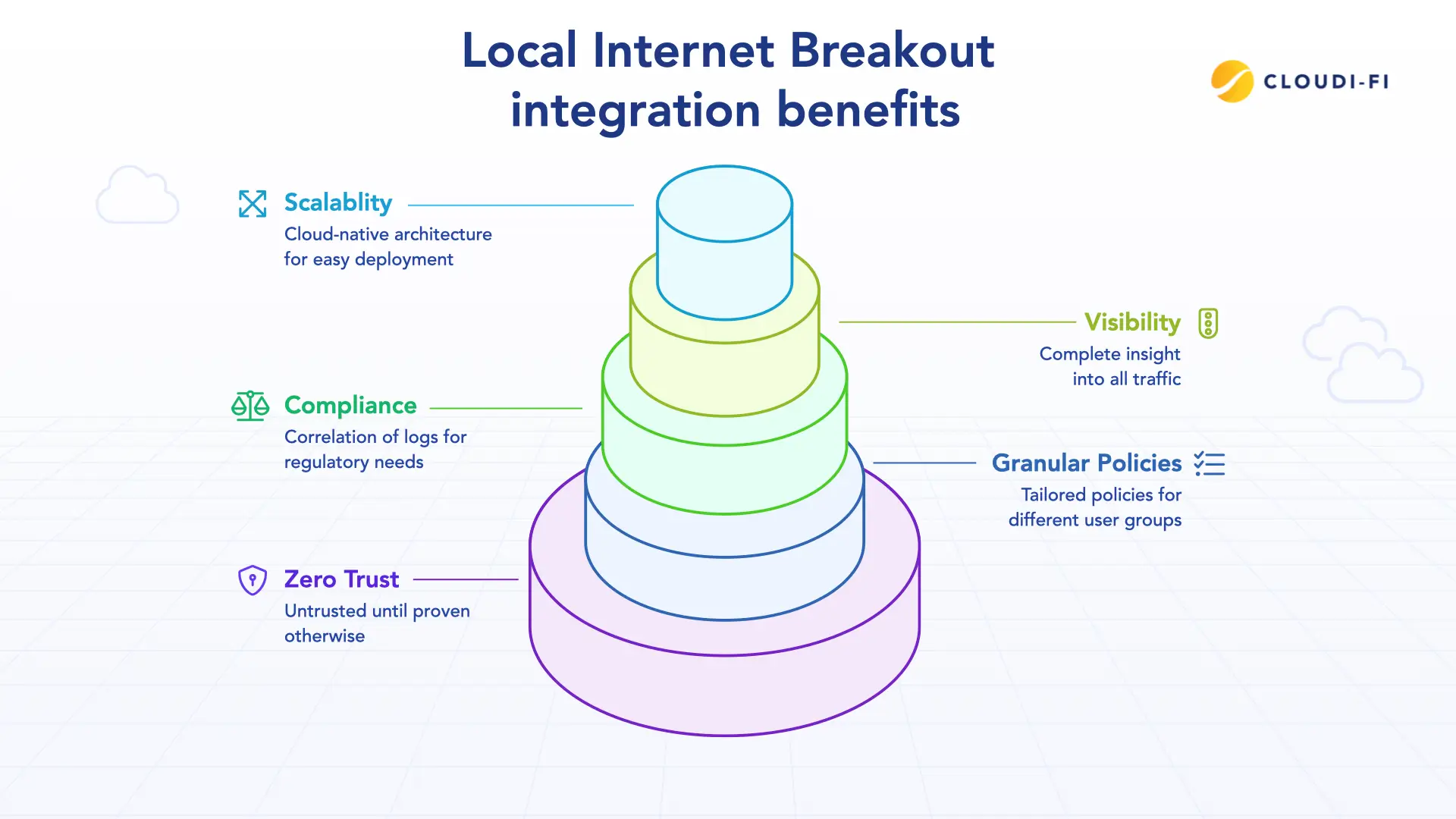
- Zero Trust policy deployment: Every device and user is considered untrusted until proven otherwise.
- Granular security policies: Different policies for daily guests, consultants, employees, and IoT categories.
- Compliance: Correlation of authentication logs (in Cloudi-Fi) with pseudonymized internet logs (in Zscaler) for regulatory requirements.
- Total visibility: Complete insight into all traffic, including guests and IoT.
- Scalability: Cloud-native architecture means you can deploy at hundreds of locations without hardware concerns.
The integration particularly shines in SD-WAN architectures where high levels of local access breakout are needed. For organizations with distributed networks: retail chains, educational campuses, hospitality venues, or multi-site enterprises; this combination delivers enterprise-grade security without the complexity of traditional approaches.
Conclusion
Local Internet Breakout isn't just a networking trend, it's a fundamental shift in how we should think about enterprise connectivity in a cloud-first world. The statistics don't lie: with 94% of enterprises using cloud computing and over 60% of corporate data in cloud storage, the old hub-and-spoke model simply doesn't align with how modern businesses operate.
The challenges are real: security, identity management, and quality of service, all require careful planning. But the solutions are also available, particularly through cloud-native approaches that match the distributed nature of modern networks.
By combining SD-WAN for intelligent routing, Zscaler for cloud-delivered security, and Cloudi-Fi for comprehensive identity management, organizations can embrace Local Internet Breakout with confidence. The result? Better user experience, lower costs, improved security, and a network architecture that's ready for whatever comes next.
The question isn't whether to implement local breakout, it's how quickly you can make the transition. Because in a world where the internet is the corporate network, bringing access closer to your users isn't just smart engineering, it's essential for staying competitive.
How Local Internet Breakout impacts personal data protection








