IoT
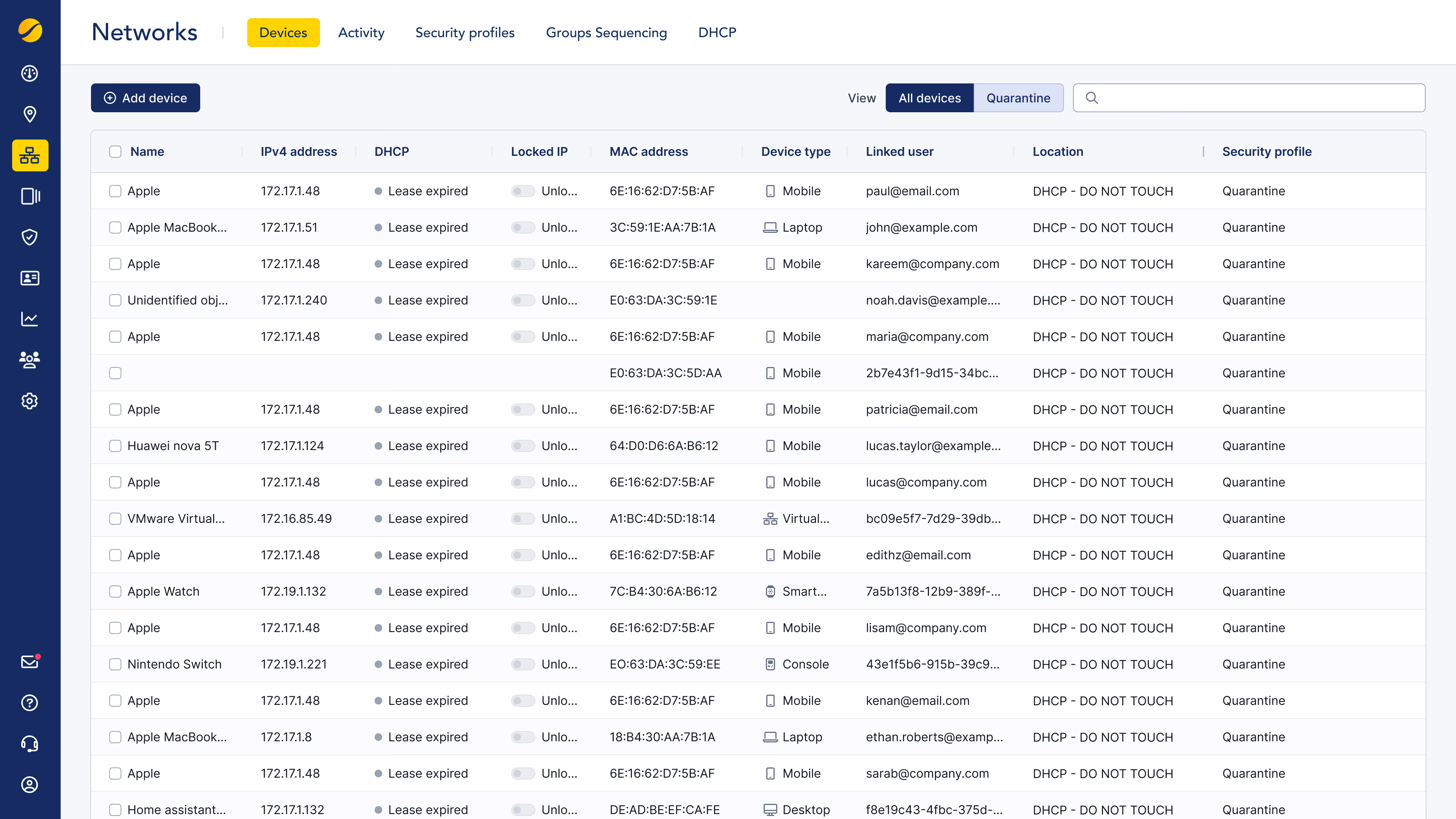
Complete device visibility, identify and manage IoT/OT devices and BYOD to reduce shadow IT risks. Simplified device onboarding enables devices to connect securely, even without user interfaces.

Simplify IoT onboarding
Securely onboard IoT on all your locations from one single admin
As enterprise networks grow, securely connecting a wide range of IoT devices becomes more complex. Manual onboarding processes—like retrieving MAC addresses and registering them through portals—are tedious, prone to error, and increasingly unsustainable for IT teams.
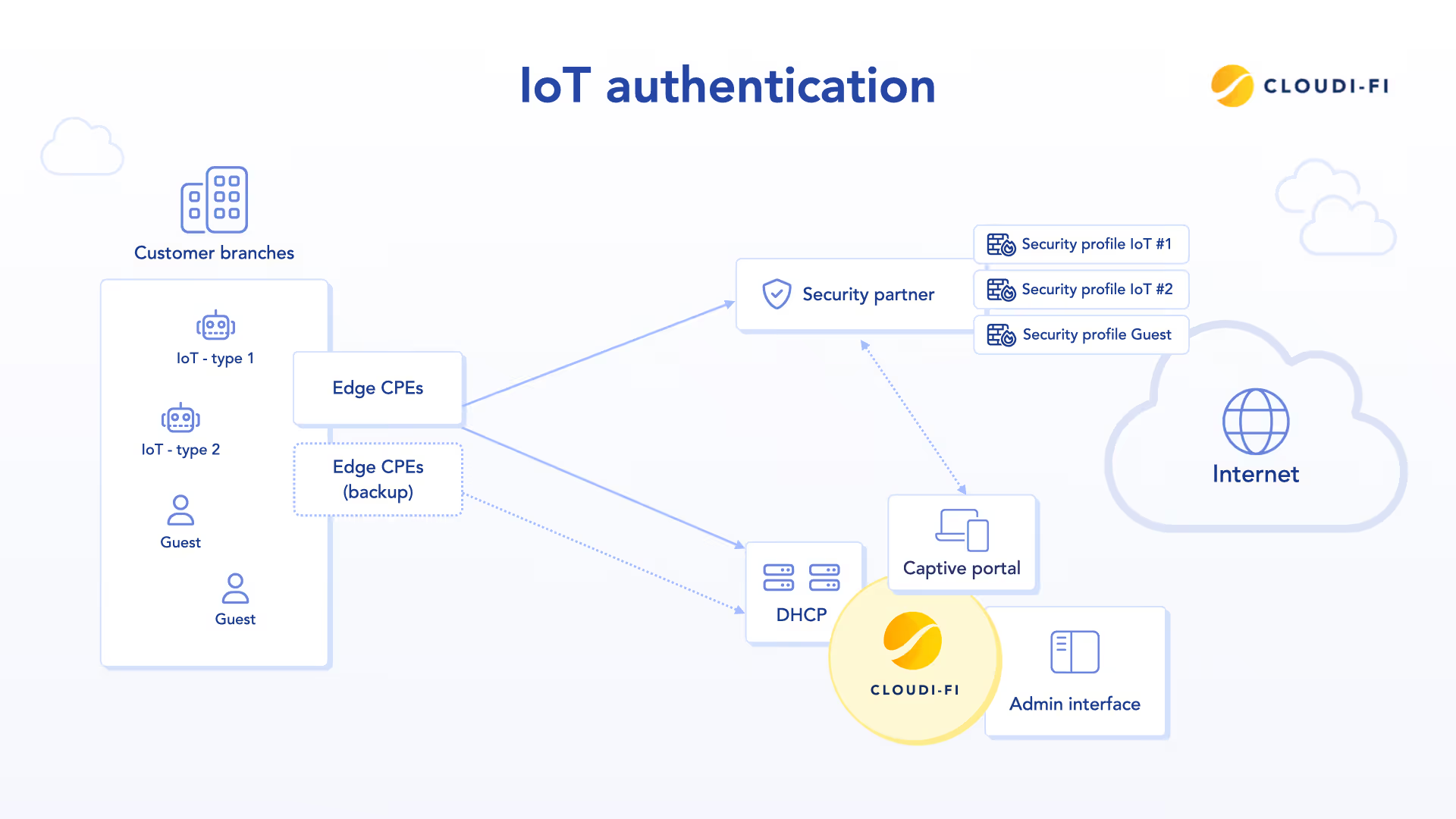
Cloudi-Fi's IoT Engine offers an automated, scalable alternative that simplifies device onboarding without compromising IoT security. It eliminates the need for dedicated SSIDs by enabling unknown devices to securely connect through the existing guest Wi-Fi, aligned with Zero Trust Network Access principles.
The solution automatically identifies devices using DHCP fingerprinting, analyzing key attributes such as type, brand, operating system, and MAC address vendor. Based on this analysis, devices are dynamically assigned to predefined security profiles—whitelisted for complete access, blacklisted to deny the connection, or quarantined pending further classification. This enables intelligent device segmentation, ensuring only trusted devices are granted appropriate access.
An innovative method to manage IoT at scale
Traditionally, enterprises are forced to create separate SSIDs just to connect IoT devices—adding unnecessary complexity and management overhead. Cloudi-Fi's IoT Engine removes that burden with seamless, secure onboarding that works without dedicated SSIDs or on-prem infrastructure, making IoT deployment effortless and scalable.
It empowers organizations to automate IoT device management while maintaining strong network protections. This is achieved through advanced fingerprinting, dynamic security policies, and complete alignment with Zero Trust and device segmentation strategies.
The result: faster deployments, reduced IT burden, and enhanced compliance with modern security standards.

Start your journey with Cloudi-Fi

Robust, scalable, and secure
Fingerprint and onboard IoT at scale
Cloud-based DHCP
Relays traffic via IPSec tunnels for secure, scalable management
Firewall policy automation
Seamlessly integrates with cloud firewalls, applying rules based on IP and profile
Fallback options
Supports manual onboarding, MAC-based rules, and fingerprint customization
Automated management
No on-prem DHCP needed
Enhanced security
Maintains network integrity without the need for a dedicated SSID
Flexible and scalable
Adapts to all IoT categories and enterprise requirements

Instant, secure access to everything, anywhere
One solution for heterogeneous technology platforms and vendors
Integrated with the best technologies on the market
Infrastructure agnostic and plug-and-play deployment: rapidly roll-out Cloudi-Fi across global sites with any infrastructure provider

Unlock the full potential of Cloudi-Fi
A feature-rich platform that empowers you to make informed decisions and drive your business forward with confidence
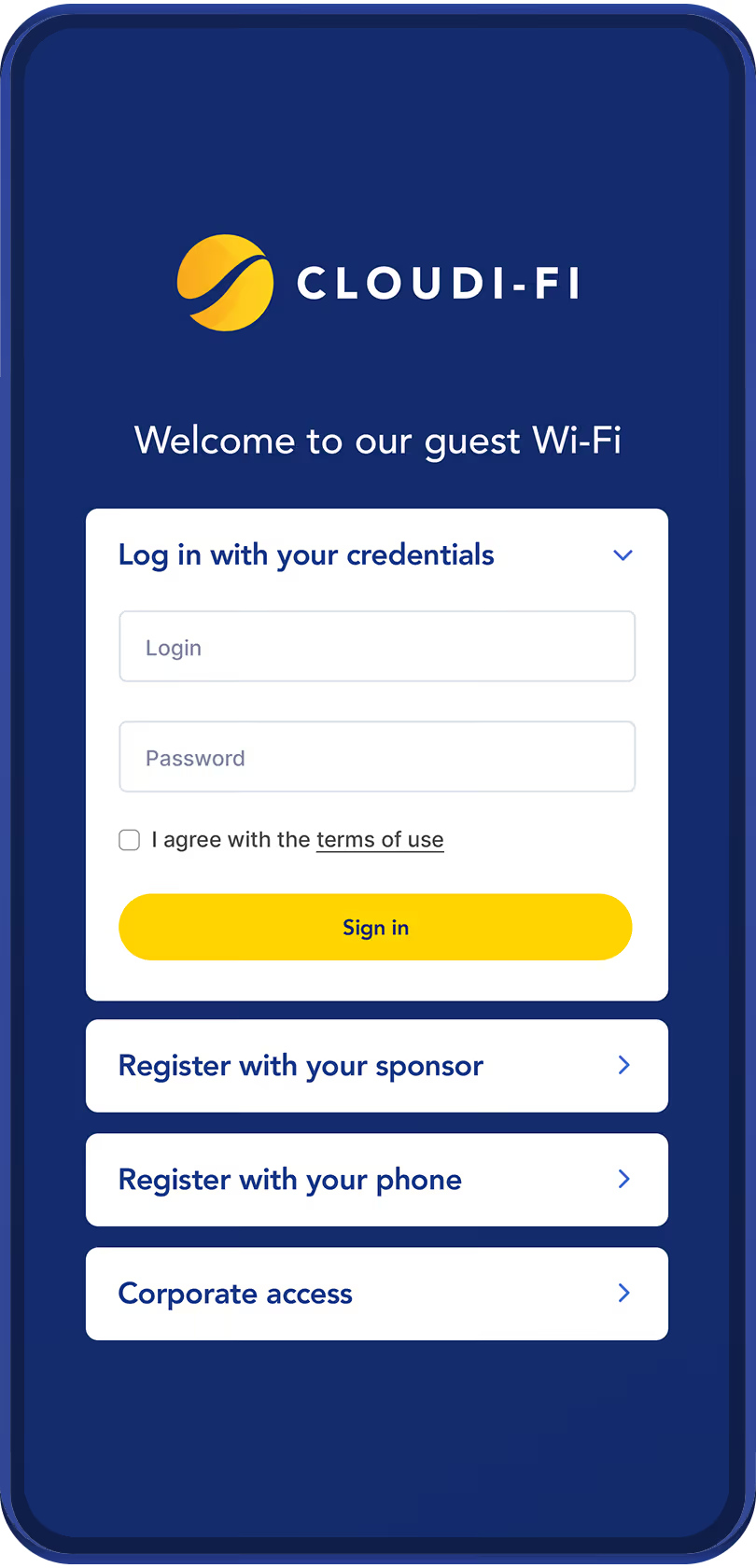
Captive Portal
Cloud-based with centralized user and device authentication.
Offers flexible Wi-Fi onboarding for guests, BYOD users, and employees thanks to social logins, custom forms, SAML, and corporate identity providers.
Compliance
Effortless global compliance with role-based access

Seamless Integration
Easy deployment with any physical and cloud infrastructure
Analytics
Full network access visibility across all sites and devices
Zero Trust security
Strict identification and authentication for every connection, ensuring robust access control

IoT/OT onboarding
Cloud-DHCP fingerprinting for seamless IoT/OT onboarding, identity control, and shadow IT risk reduction

Cloud native, borderless, scalable and global!
Unlocking Universal Zero Trust Network Access on all continents

Trusted by 200+ enterprises worldwide







































